Void Banshee Exploits Legacy Internet Explorer In Attack
While Microsoft has released an update patch, experts fear many systems may remain vulnerable.
Alan J July 17, 2024

Share on LinkedInShare on Twitter
Researchers have uncovered a critical vulnerability (CVE-2024-38112) that the Void Banshee threat actor group has been actively exploiting in a recent campaign to deploy the Atlantida info-stealer through a disabled version of Internet Explorer.
The campaign highlights the security risks introduced by the maintenance of legacy software on modern systems.
Anatomy of Void Banshee Attack-Chain
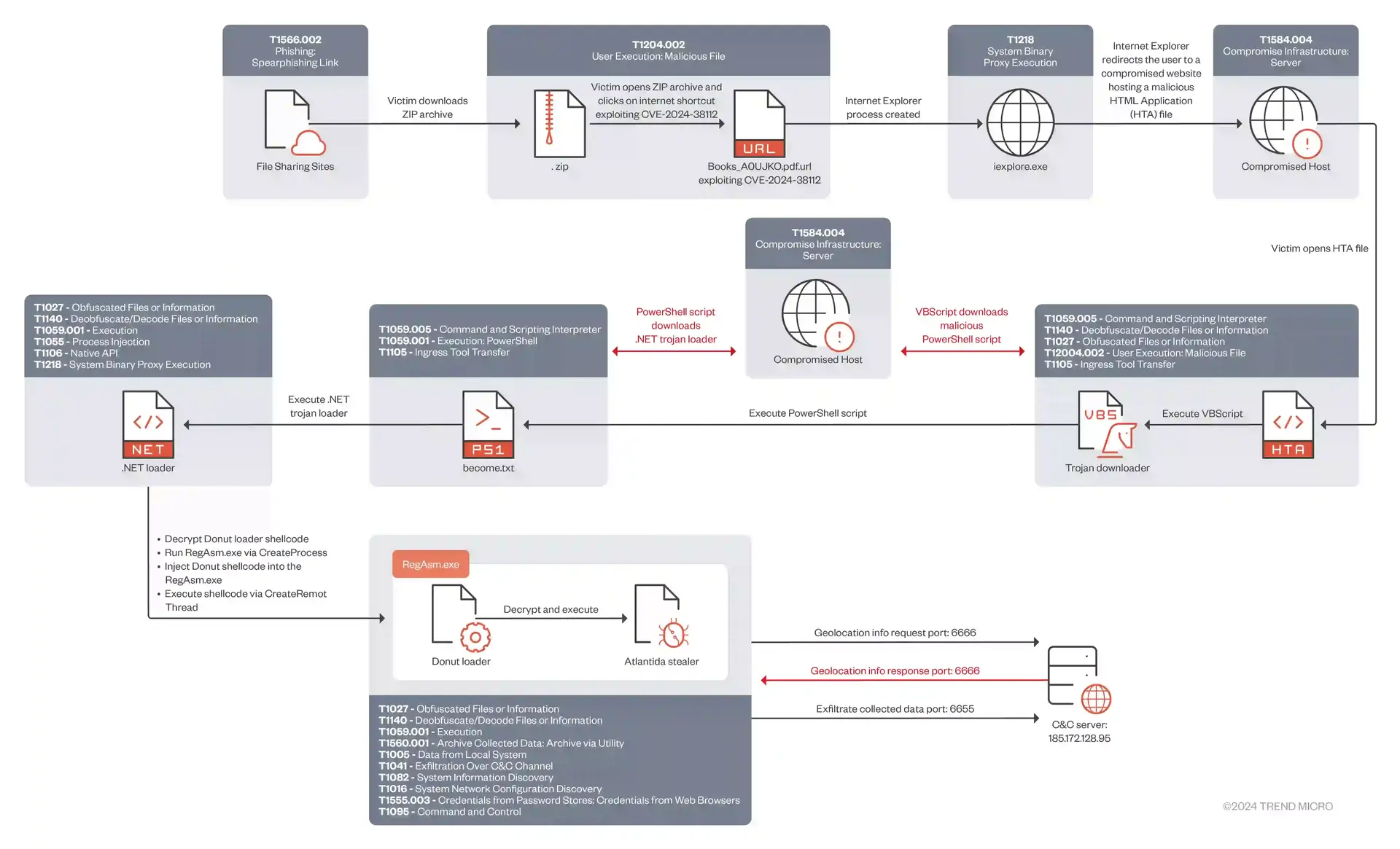
The Void Banshee group lures victims by disguising malicious files as e-books and sharing them through cloud services, Discord servers and online libraries. When a user opens one of these files – typically a zip archive masquerading as a PDF and containing malicious shortcut files, they trigger a chain of events that ultimately installs the Atlantida stealer.

Source: trendmicro.com
Researchers from Trend Micro stated that the the attack chain begins with a spearphishing email containing a zip archive with a malicious file disguised as a PDF. The file, named “Books_A0UJKO.pdf.url”, uses the MHTML protocol handler and the x-usc! directive to exploit the CVE-2024-38112 vulnerability.
This allows the attacker to access and execute files through the disabled IE process. The malicious file downloads an HTML file, which in turn downloads an HTA file that contains a Visual Basic Script (VBScript) that decrypts and executes a PowerShell script.

Legacy Internet Explorer version on Modern Systems (Source: trendmicro.com)
The PowerShell script downloads an additional script from a compromised web server and executes it, creating a new process for the downloaded script. This script is designed to download and execute a PowerShell trojan, which can be used to compromise the victim’s system.
The campaign ultimately exploits the vulnerability in the MHTML protocol handler to access and run files through the system in-built disabled instance of Internet Explorer. This technique bypasses normal security controls and allows the attackers to directly execute the Atlantida info-stealer malware on the victim’s system.
The researchers note that Atlantida is based on previous open-source stealers such as NecroStealer and PredatorTheStealer, designed with many of the same capabilities as these stealers.
It targets sensitive information from various applications, including Telegram, Steam, FileZilla, cryptocurrency wallets and web browsers such as Chrome and Microsoft Edge to exfiltrate sensitive and important data, such as passwords and cookies.
The malware allows attackers to capture victim’s screens and exfiltrate information from cryptocurrency-associated browser extensions, registering each extension with a unique ‘Extension ID.’ Data exfiltrated from the attack is compressed within a ZIP archive file and transmitted via TCP.
Microsoft Patched Vulnerability
The researchers disclosed the vulnerability to Microsoft, which patched the vulnerability in its July 2024 update cycle, unregistering the MHTML handler from Internet Explorer. However, experts warn that many systems may remain unpatched and vulnerable.
To protect against this and similar attacks, security professionals recommend:
- Promptly applying all available Windows security updates
- Implementing robust email filtering to block malicious attachments
- Educating users about the dangers of opening suspicious files or links
- Deploying endpoint protection software capable of detecting and blocking such attacks
As cybercriminals continue to exploit overlooked vulnerabilities in legacy systems, the discovery of CVE-2024-38112 serves as a stark reminder of the importance of comprehensive security measures and timely patching.





