Surge In Mekotio Targeting Of Latin American Financial Systems

The Mekotio malware has been active since 2015, and has primarily been used to target targets countries like Brazil, Chile, Mexico, Spain and Peru.
Alan J July 5, 2024

Share on LinkedInShare on Twitter
The Mekotio banking trojan has resurfaced as a significant threat to financial institutions and individuals across Latin America. The Mekotio malware active since 2015, has primarily been used against several persistent target countries such as Brazil, Chile, Mexico, Spain and Peru with the focus of stealing sensitive information such as banking credentials.
Mekotio shares similarities with other Latin American banking malware, such as Grandoreiro, who’s operations had been recently disrupted by law enforcement.
Mekotio Infection and Operation
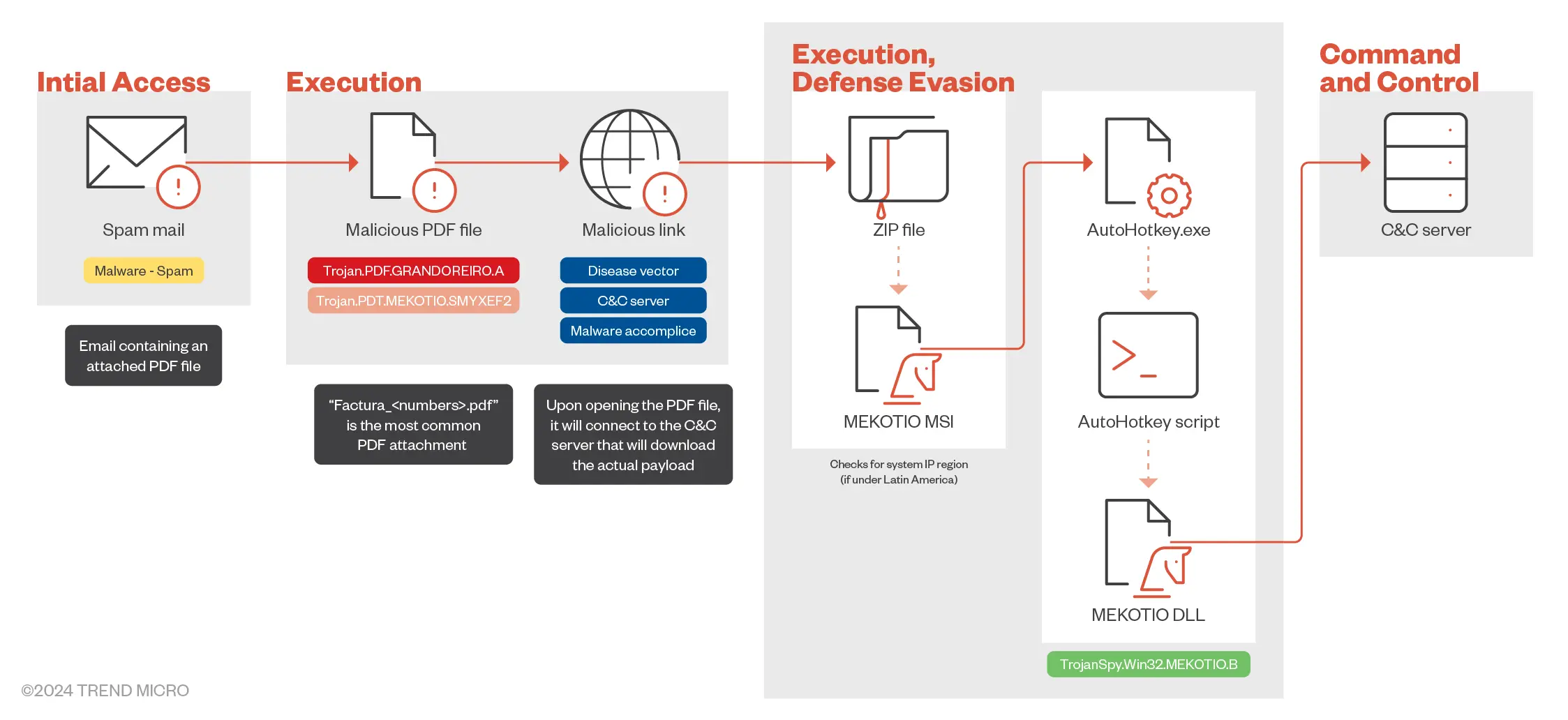
Researchers from Trend Micro noticed an uptick in the use of the Mekotio malware across campaigns. The researchers stated that Mekotio typically infiltrates systems through phishing emails purporting to be communications from tax agencies. These messages often claim the recipient has unpaid tax obligations while embedding malicious ZIP file attachments or links that download and execute the malware on the victim’s system.

Source: trendmicro.com
Once activated, Mekotio gathers system information and establishes a connection with a command-and-control server. The malware performs the following operations on infected systems:
- Credential theft: Mekotio displays fake pop-ups mimicking legitimate banking sites to trick users into entering their login details.
- Information gathering: The trojan captures screenshots, logs keystrokes and steals clipboard data.
- Persistence: Mekotio employs tactics like adding itself to startup programs or creating scheduled tasks to maintain its presence on infected systems.
Several security researchers have investigated previous campaigns involving the use of the Mekotio malware, often noting it as a geolocation-specific Trojan. A threat summary from Microsoft Security Intelligence states, “The Mekotio Trojan evades detection using a malicious DLL that executes using DLL sideloading, since the DLL and executable loading the DLL is dropped in the same folder. The folder is the first location where an executable searches for a loading module to help execute the malicious dropped DLL before reaching the original DLL.”
The page also notes that victims may be restricted from accessing legitimate banking websites after infection.
Prevention and Mitigation Against Mekotio
The researchers have advised the maintenance of proper practices to combat threats such as Mekotio. These include:
- Being skeptical of unsolicited emails and verifying the sender’s email address.
- Avoiding clicking on links and downloading attachments unless absolutely certain of the sender’s identity.
- Verifying sender identity by contacting the sender through known contact details.
- Using email filters and anti-spam software, and ensuring they are up to date.
- Reporting phishing attempts to IT and security teams when applicable.
- Educating employees on security best practices, including phishing and social engineering tactics.
The researchers also shared the following potential indicators of compromise:
File Hashes:
5e92f0fcddc1478d46914835f012137d7ee3c217
f68d3a25433888aa606e18f0717d693443fe9f5a
3fe5d098952796c0593881800975bcb09f1fe9ed
1087b318449d7184131f0f21a2810013b166bf37
ef22c6b4323a4557ad235f5bd80d995a6a15024a
C&C servers:
23[.]239[.]4[.]149:80
68[.]233[.]238[.]122:80
34[.]117[.]186[.]192:80
68[.]221[.]121[.]160:9095
68[.]221[.]121[.]160:80
tudoprafrente[.]org
tudoprafrente[.]co:7958
Downloads:
hxxps://intimaciones[.]afip[.]gob[.]ar[.]kdental[.]cl/Documentos_Intimacion/
hxxps://techpowerup[.]net/cgefacturacl/descargafactmayo/eletricidad/
hxxps://christcrucifiedinternational[.]org/descargafactmayo/eletricidad/
By adhering to these guidelines, maintaining vigilance and scrutinising possible attack indications, organizations and individuals can significantly reduce their risk of falling victim to the Mekotio banking trojan.




