Supposed Grasshopper Campaign Targets Israeli Govt And Firms

These attacks, while diverse and spanning unrelated industries, consistently utilize well-known open-source malware as part of their infection chain.
Ashish Khaitan July 3, 2024

Share on LinkedInShare on Twitter
A recent cybersecurity investigation has uncovered a sophisticated operation known as “Supposed Grasshopper,” targeting both Israeli government entities and private companies through the deployment of open-source malware.
The Supposed Grasshopper campaign, characterized by its strategic use of infrastructure and toolsets, demonstrates a blend of publicly available tools and customized developments to achieve its objectives.
Central to the Supposed Grasshopper operation is a domain identified as a command and control (C2) server, purportedly associated with an Israeli government entity. Analysts have observed a pattern of attacks extending to various private sector organizations throughout late 2023.
These attacks, while diverse and spanning unrelated industries, consistently utilize well-known open-source malware as part of their infection chain.
Decoding the Supposed Grasshopper Campaign
Infection Chain (Source: HarfangLab)
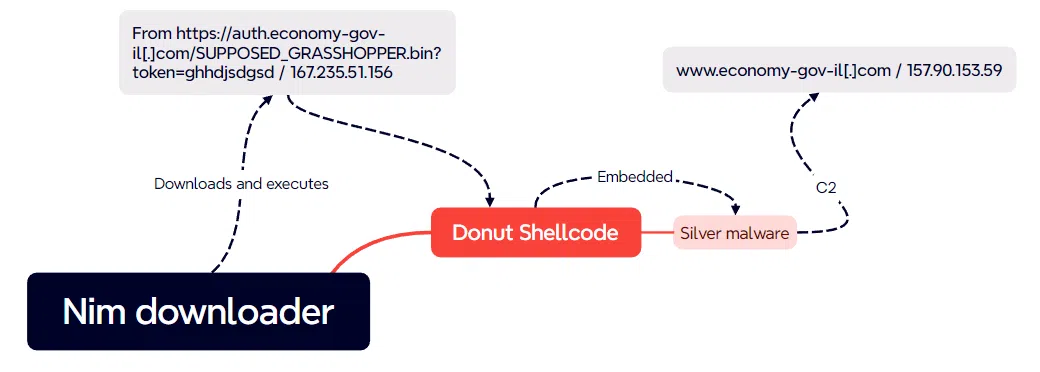
According to HarfangLab, the initial phase of the campaign involves the distribution of malicious payloads via specially crafted WordPress websites. These sites host seemingly innocuous files, such as Virtual Hard Disk (VHD) images, which, when accessed, trigger the installation of a first-stage Nim downloader. This downloader, designed by the threat actors, facilitates the retrieval and execution of subsequent malware components from remote servers under their control.
The final payload of the attack campaign comprises a hybrid of two prominent open-source projects: Donut, a framework for generating position-independent shellcode, and Sliver, a Golang-based trojan designed as a cost-effective alternative to more traditional malware like CobaltStrike. These tools empower the attackers with full control over compromised systems, allowing them to execute a wide range of malicious activities remotely.
Further investigation into the campaign’s infrastructure reveals a network of domains registered under various aliases, including impersonations of legitimate entities such as SintecMedia and Carlsberg. These domains serve as staging points and C2 servers for the malware, indicating a deliberate effort by the attackers to blend in with recognizable brands while conducting their operations.
Legitimacy and Geopolitical Concerns in Cybersecurity
Despite the campaign’s sophistication, questions remain about its true intent. Analysts speculate that the activities could potentially be attributed to legitimate penetration testing exercises due to their focused and methodical approach. However, the absence of identifiable links to known testing companies raises concerns about the campaign’s legitimacy and its potential geopolitical implications.
The discovery highlights broader challenges in cybersecurity, particularly the ease with which threat actors can leverage freely available tools and realistic tactics like WordPress websites for both legitimate and malicious purposes. This highlights the ongoing need for increased transparency and accountability in penetration testing engagements, especially when government entities and critical infrastructure are involved.
Looking ahead, cybersecurity experts anticipate similar campaigns will continue to exploit accessible attack frameworks, complicating efforts to attribute and mitigate such threats effectively. This trend further highlights the nature of cyber warfare and highlights the critical role of proactive defense measures in safeguarding against increasingly sophisticated attacks.





