SeleniumGreed Campaign Targets Cryptocurrency Users Online

This threat leverages the popular Selenium WebDriver API and has raised significant concerns about the security of cloud environments.
Ashish Khaitan July 26, 2024

Share on LinkedInShare on Twitter
Threat actors are increasingly targeting exposed Selenium Grid services to deploy cryptominers, a campaign dubbed “SeleniumGreed.” This threat leverages the popular Selenium WebDriver API and has raised significant concerns about the security of cloud environments.
Selenium Grid is an integral component of the Selenium suite, used primarily for running tests across multiple machines and environments. It consists of a central hub that manages test distribution to various nodes, which are individual machines capable of executing tests.
The grid allows parallel test execution on different browsers and operating systems, reducing testing time and ensuring consistency across various setups.
The SeleniumGreed Campaign
Selenium, an open-source testing framework, is extremely popular among developers and testers. Its Docker image has been pulled from Docker Hub over 100 million times, highlighting its widespread use. Despite its benefits, Selenium Grid was not initially designed with internet exposure in mind and lacks built-in security features, making it susceptible to abuse if not properly configured.
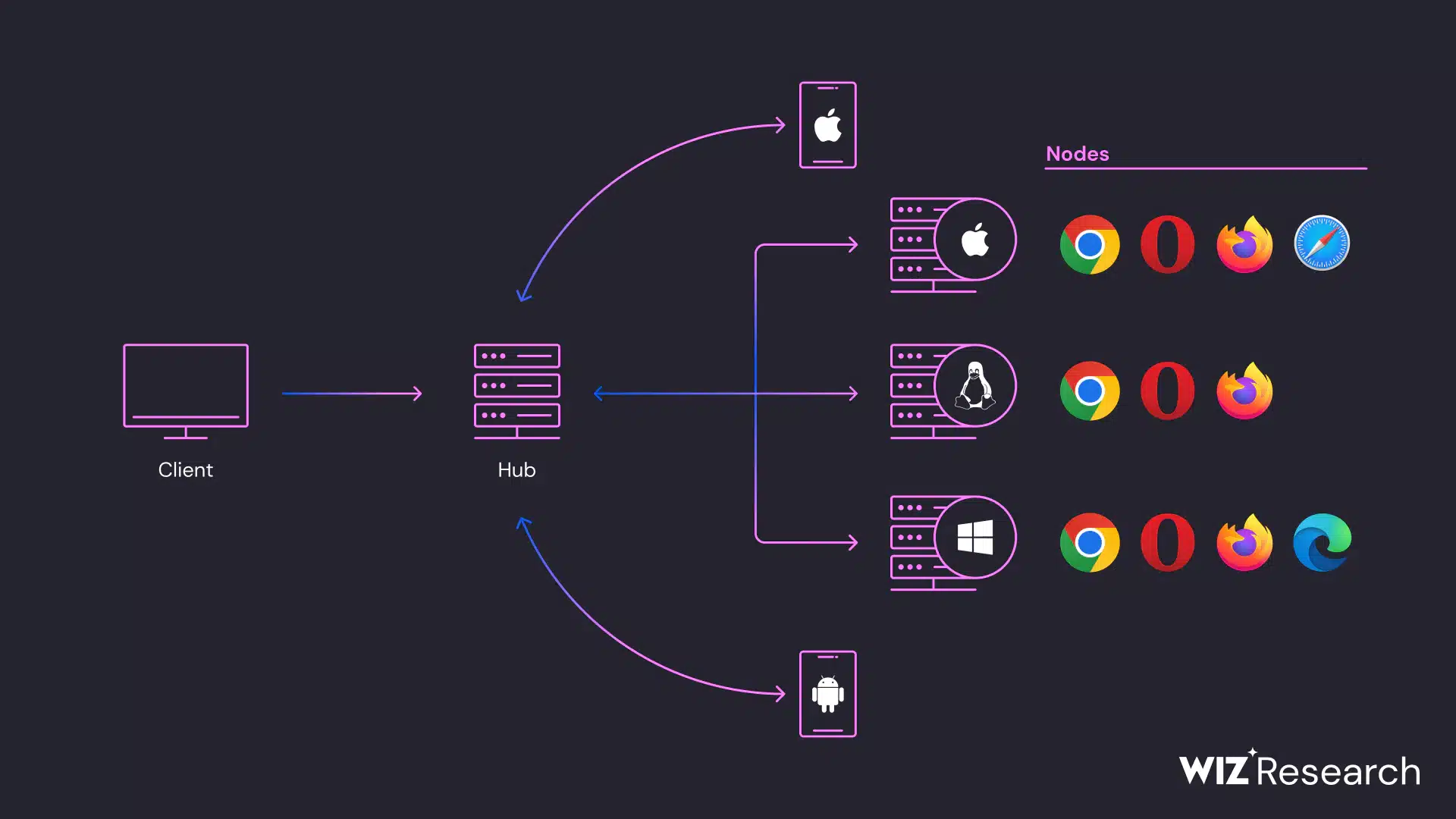
Selenium Grid architecture (Source: Wiz)
The SeleniumGreed campaign exploits the default misconfigurations in Selenium Grid services to execute cryptomining scripts. By default, Selenium Grid instances do not have authentication enabled, leaving them vulnerable to unauthorized access. This flaw allows attackers to utilize the Selenium WebDriver API to interact with the underlying system of the exposed nodes, including executing remote commands and downloading files.
Recent observations from Wiz researchers have shown that threat actors are exploiting these vulnerabilities by deploying cryptominers such as a modified XMRig miner. The attack flow typically involves using older versions of Selenium (v3.141.59) to execute remote commands that install and run the miner. Notably, this issue is not confined to outdated versions; even the latest versions of Selenium Grid can be compromised if exposed to the internet.
Attackers typically begin by sending requests to vulnerable Selenium Grid hubs, configuring the Chrome binary path to point to a Python interpreter. This allows them to run arbitrary Python scripts on the affected machine. For example, the attackers may use these scripts to establish a reverse shell, which is then used to download and execute cryptomining software.
In one instance, the attacker used a reverse shell to deploy a custom version of the XMRig miner, which was modified with UPX headers to evade detection. This miner dynamically generates its pool IP address at runtime and utilizes specific TLS fingerprinting features to ensure communication only with servers under the attacker’s control. This sophisticated approach helps the attacker avoid detection and maintain control over the mining operations.
Attackers Exploit Selenium Grid and Vulnerability Statistics
Data from FOFA indicates that over 30,000 instances of Selenium Grid are exposed globally, many of which operate on the default port 4444. This widespread exposure significantly increases the risk of remote command execution attacks, emphasizing the critical need for robust security measures in Selenium Grid deployments.
To protect against such threats, organizations should implement several key strategies. Firstly, network security controls are essential; using firewalls to manage both inbound and outbound traffic and restricting access to trusted IP ranges can help safeguard Selenium Grid services. Additionally, enabling basic authentication on Selenium Grid instances will prevent unauthorized access.
Regular network and vulnerability scanning is also crucial to identify and address exposed services and potential vulnerabilities. Furthermore, deploying runtime detection mechanisms will enable real-time identification and response to online threats.
The SeleniumGreed campaign highlights a significant security gap in the configuration of Selenium Grid services. As attackers continue to exploit these vulnerabilities for cryptomining, organizations must implement robust security measures and stay informed about emerging threats. By taking proactive steps to secure Selenium Grid deployments, organizations can protect their cloud environments from this growing threat.





