Polyfill Supply Chain Attack Potentially Affected ‘Tens Of Millions’ Of Websites

The Polyfill supply chain attack has the potential to be the largest-ever digital supply chain attack.
Paul Shread June 27, 2024

Share on LinkedInShare on Twitter
Claims, counterclaims, website shutdowns, redirections and DDoS attacks were among the highlights (or lowlights) as news of the Polyfill supply chain attack entered its second day.
After Polyfill(.)io was shut down by registrar Namecheap, the allegedly compromised JavaScript CDN service relaunched at Polyfill(.)com, and claimed it had been “maliciously defamed.”
Meanwhile, the researchers who first reported the supply chain compromise were hit by a DDoS attack, while many security researchers wondered how such a widely used web component could have been sold to a Chinese company in the first place.
Here are the latest developments in the attack, which is potentially the largest-ever digital supply chain attack. While the full extent of malware distributed through the CDN remains unknown, initial estimates were that more than 100,000 websites were using the service.
However, in a post on X, Cloudflare CEO Matthew Prince said “Tens of millions of websites (4% of the web) uses Polyfill(.)io. Extremely concerning malware has been discovered impacting any site using Polyfill.” He also said Cloudflare was automatically replacing Polyfill links with its own mirror.
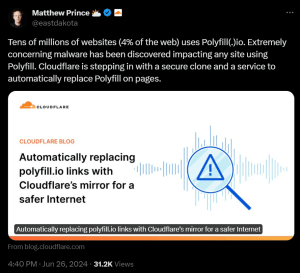
Extent of website exposure to Polyfill(.)io (source: X)
Extent of Polyfill Supply Chain Attack Unknown, But Big Names Among Users
Some of the biggest names turning up in a search for cdn(.)polyfill(.)io include Intuit, JSTOR, the World Economic Forum, a Coldwell Banker real estate site, major educational sites like Brandeis University, the technical standards organization ASTM, the Bank of Ireland, Live Nation sites for Spain and the UK, the RAINN anti-sexual violence organization, data management vendor AvePoint, investment company MSCI, industrial network company Moxa, the Environmental Defense Fund, and the Dubai Airports Company.
The extent of the Polyfill supply chain attack may be unknown for some time. In February, a Chinese company bought the Polyfill domain and the Github account, and concern about the deal surfaced almost immediately.
The Sansec researchers who initially publicly disclosed the threat two days ago noted that since the acquisition, “this domain was caught injecting malware on mobile devices via any site that embeds cdn.polyfill.io. Any complaints were quickly removed from the Github repository.”
The researchers said that the polyfill code is dynamically generated based on the HTTP headers, “so multiple attack vectors are likely.” Sansec decoded one particular malware strain that redirects mobile users to a sports betting site using a fake Google analytics domain (googie-anaiytics(.)com).
The researchers said they were subsequently hit by a DDoS attack after publishing their initial report.
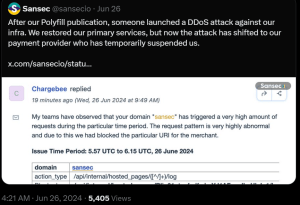
Researchers hit by DDoS attack (source: X)
Google Started Blocking Ads in Mid-June
It’s not clear how long the threat has been known – it is standard practice for threat researchers to wait to reveal their findings until affected parties have had a chance to fix vulnerabilities – but Google has apparently been rejecting ads that link to the googie-anaiytics domain since at least mid-June.
In a letter to advertisers, Google cited redirects coming from “a few different third-party web resource providers including Polyfill.io, Bootcss.com, Bootcdn.net, or Staticfile.org” for the rejected ads.
Mitigations Set Up By Cloudflare, Fastly
To mitigate supply chain risk, Cloudflare released an automatic JavaScript URL rewriting service that will rewrite any link to polyfill(.)io found in a website proxied by Cloudflare to a link to the company’s mirror under cdnjs. Cloudflare also charged that Polyfill was falsely misusing the Cloudflare name and logo on its website.
Fastly – which hosted the CDN for free before it was sold – had also set up an alternative service based on the Polyfill open source project.
Developer Andrew Betts, who had created the Polyfill service project, said in an X post at the time of the sale in February that “No website today requires any of the polyfills in the polyfill.io library. Most features added to the web platform are quickly adopted by all major browsers, with some exceptions that generally can’t be polyfilled anyway, like Web Serial and Web Bluetooth.”
Polyfill Owner Responds
The Polyfill(.)io owners took to X to respond to the malware charges. “Someone has maliciously defamed us,” said a post to the Polyfill_Global account. “We have no supply chain risks because all content is statically cached. Any involvement of third parties could introduce potential risks to your website, but no one would do this as it would be jeopardize (sic) our own reputation.”

Polyfill response (source: X)
The Cyber Express will continue to update readers as this story evolves.





