-
BrainsHacking

In today’s The Tentacle, we explore the USD0++ depeg drama that shook DeFi this weekend. Usual Money’s abrupt redemption changes…
In today’s The Tentacle, we explore the USD0++ depeg drama that shook DeFi this weekend. Usual Money’s abrupt redemption changes…
-
BrainsHacking

-
BrainsHacking

JUST IN: 🇺🇸 President-elect Trump expected to issue executive orders related to crypto policies on his first day in office. : …
JUST IN: 🇺🇸 President-elect Trump expected to issue executive orders related to crypto policies on his first day in office.…
-
🚨 🚨 🚨 350,371 #SOL (62,123,850 USD) transferred from unknown wallet to unknown wallet
🚨 🚨 🚨 350,371 #SOL (62,123,850 USD) transferred from unknown wallet to unknown wallet Details : Whale Alert 🔥Go to…
-
Trump Expected To Issue Executive Orders Pertaining To Crypto On Day One: Washington Post
Trump Expected To Issue Executive Orders Pertaining To Crypto On Day One: Washington Post 🔗 velo.xyz 🔥Go to our website,…
-
JUST IN: BlackRock says “Bitcoin is the world’s leading and most widely adopted crypto asset.” : Watcher Guru…
JUST IN: BlackRock says “Bitcoin is the world’s leading and most widely adopted crypto asset.” : Watcher Guru 🔥Go to…
-
🔥 🔥 🔥 50,000,000 #USDC (50,008,725 USD) burned at USDC Treasury
🔥 🔥 🔥 50,000,000 #USDC (50,008,725 USD) burned at USDC Treasury Details : Whale Alert 🔥Go to our website, https://brainshacking.com.…
-
BrainsHacking

Spot XRP ETF to Be Approved This Year, Says Top Analyst; US Congressman Discloses XRP, SOL and BTC Holdings; 8.32 Trillion in 24…
Spot XRP ETF to Be Approved This Year, Says Top Analyst; US Congressman Discloses XRP, SOL and BTC Holdings; 8.32…
-
JUST IN: BlackRock says crypto has “outpaced growth for mobile phones and the internet.” : Watcher Guru…
JUST IN: BlackRock says crypto has “outpaced growth for mobile phones and the internet.” : Watcher Guru 🔥Go to our…
-
Coinbase announced that it will support the Peanut the Squirrel (PNUT) token on the Solana network, with trading set to begin on…
Coinbase announced that it will support the Peanut the Squirrel (PNUT) token on the Solana network, with trading set to…
-
🔥 🔥 🔥 50,000,000 #USDC (50,015,916 USD) burned at USDC Treasury
🔥 🔥 🔥 50,000,000 #USDC (50,015,916 USD) burned at USDC Treasury Details : Whale Alert 🔥Go to our website, https://brainshacking.com.…
-
🇳🇬 Shipping bitcoin miners to off-grid areas of Nigeria ⚡️ : Bitcoin
🇳🇬 Shipping bitcoin miners to off-grid areas of Nigeria ⚡️ : Bitcoin 🔥Go to our website, https://brainshacking.com. ‼️ Subscribe to…
-
BrainsHacking

Dogecoin Founder’s Bitcoin Crash Tweet Sparks Hot Discussion
Dogecoin Founder’s Bitcoin Crash Tweet Sparks Hot Discussion https://www.investing.com/news/cryptocurrency-news/dogecoin-founders-bitcoin-crash-tweet-sparks-hot-discussion-3810148
-
BrainsHacking

Semler Scientific Increases Bitcoin Bag to 2,321 BTC With Latest Purchase
Semler Scientific Increases Bitcoin Bag to 2,321 BTC With Latest Purchase https://www.investing.com/news/cryptocurrency-news/semler-scientific-increases-bitcoin-bag-to-2321-btc-with-latest-purchase-3810147
-
BrainsHacking
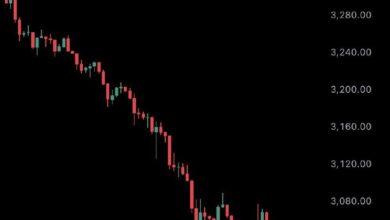
JUST IN:JUST IN: $ETH falls under $3,000. : Watcher Guru
JUST IN:JUST IN: $ETH falls under $3,000. : Watcher Guru 🔥Go to our website, https://brainshacking.com. ‼️ Subscribe to the main…
-
🚨 🚨 🚨 🚨 🚨 🚨 🚨 150,000,000 #USDT (150,006,009 USD) transferred from Tether Treasury to #Bitfinex…
🚨 🚨 🚨 🚨 🚨 🚨 🚨 150,000,000 #USDT (150,006,009 USD) transferred from Tether Treasury to #Bitfinex Details : Whale…
-
BrainsHacking

Fire Token Launches Presale for Tokenized Bitcoin Mining Operation in Canada
Fire Token Launches Presale for Tokenized Bitcoin Mining Operation in Canada https://www.investing.com/news/cryptocurrency-news/fire-token-launches-presale-for-tokenized-bitcoin-mining-operation-in-canada-3810102
-
🚨 122,620 #SOL (21,748,048 USD) transferred from unknown wallet to #Kraken
🚨 122,620 #SOL (21,748,048 USD) transferred from unknown wallet to #Kraken Details : Whale Alert 🔥Go to our website, https://brainshacking.com.…
-
BrainsHacking
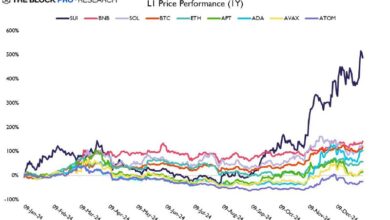
-
15,000,000 #XLM (6,247,668 USD) transferred from #Coinbase Withdrawals to unknown wallet
15,000,000 #XLM (6,247,668 USD) transferred from #Coinbase Withdrawals to unknown wallet Details : Whale Alert 🔥Go to our website, https://brainshacking.com.…
-
BrainsHacking
Pantera Capital’s 2025 Blockchain Letter predicts Bitcoin’s DeFi rise, blockchain adoption via TradFi gateways, and stablecoins …
Pantera Capital’s 2025 Blockchain Letter predicts Bitcoin’s DeFi rise, blockchain adoption via TradFi gateways, and stablecoins boosting USD dominance, while…
-
🚨 🚨 🚨 🚨 972 #BTC (89,058,957 USD) transferred from #Robinhood to unknown wallet
🚨 🚨 🚨 🚨 972 #BTC (89,058,957 USD) transferred from #Robinhood to unknown wallet Details : Whale Alert 🔥Go to…
-
🚨 🚨 🚨 🚨 🚨 112,958,640 #USDC (112,975,527 USD) transferred from Coinbase Institutional to unknown wallet…
🚨 🚨 🚨 🚨 🚨 112,958,640 #USDC (112,975,527 USD) transferred from Coinbase Institutional to unknown wallet Details : Whale Alert…
-
BrainsHacking

-
1,850 Bitcoin Stun Binance in Surprising Whale Move: Details
1,850 Bitcoin Stun Binance in Surprising Whale Move: Details https://www.investing.com/news/cryptocurrency-news/1850-bitcoin-stun-binance-in-surprising-whale-move-details-3810012
-
HTX 2025 Outlook: Five Sectors to Look Forward to, and How Trump’s Policy Will Affect Crypto Industry …
HTX 2025 Outlook: Five Sectors to Look Forward to, and How Trump’s Policy Will Affect Crypto Industry https://www.investing.com/news/cryptocurrency-news/htx-2025-outlook-five-sectors-to-look-forward-to-and-how-trumps-policy-will-affect-crypto-industry-3809948
-
BrainsHacking

“hello world computer” – after all the talks around their activity and strategy recently in the Ethereum community, a first post…
“hello world computer” – after all the talks around their activity and strategy recently in the Ethereum community, a first…
-
BrainsHacking

A message from our sponsors at f(x) Protocol: Ready for up to 7X $ETH exposure—without funding fees or liquidation worries? xPOS…
A message from our sponsors at f(x) Protocol: Ready for up to 7X $ETH exposure—without funding fees or liquidation worries?…
-
Solana $180
Solana $180 🔥Go to our website, https://brainshacking.com. ‼️ Subscribe to the main channel, https://t.me/BrainsHacking to participate in prize drawings and…
-
Bitcoin $92,000
Bitcoin $92,000 🔥Go to our website, https://brainshacking.com. ‼️ Subscribe to the main channel, https://t.me/BrainsHacking to participate in prize drawings and…
