-
Bithumb, the second largest cryptocurrency exchange in South Korea, will launch Ancient 8 (A8) and DRIFT Korean Won trading pair…
Bithumb, the second largest cryptocurrency exchange in South Korea, will launch Ancient 8 (A8) and DRIFT Korean Won trading pairs.…
-
JUST IN: 🇺🇸 President Biden announces $770 one-time payment to California wildfire victims. : Watcher Guru…
JUST IN: 🇺🇸 President Biden announces $770 one-time payment to California wildfire victims. : Watcher Guru 🔥Go to our website,…
-
According to Wired Italia, Italy’s largest banking group, Intesa Sanpaolo, purchased 11 bitcoins with a total value of approxima…
According to Wired Italia, Italy’s largest banking group, Intesa Sanpaolo, purchased 11 bitcoins with a total value of approximately 1…
-
FTX/Alameda conducted its monthly SOL redemption and transfer today: 182,421 SOL (US$32.35 million) was redeemed from the stake …
FTX/Alameda conducted its monthly SOL redemption and transfer today: 182,421 SOL (US$32.35 million) was redeemed from the stake and distributed…
-
BrainsHacking

Introducing ConsoleKit by Brahma, a toolkit which brings agents onchain – 𝕏/@…
Introducing ConsoleKit by Brahma, a toolkit which brings agents onchain – 𝕏/@jainargh : Leviathan News 🔥Go to our website, https://brainshacking.com.…
-
The US Court of Appeals for the Third Circuit has issued an opinion in cryptocurrency exchange Coinbase’s civil case with the SE…
The US Court of Appeals for the Third Circuit has issued an opinion in cryptocurrency exchange Coinbase’s civil case with…
-
Bitcoin $95,000
Bitcoin $95,000 🔥Go to our website, https://brainshacking.com. ‼️ Subscribe to the main channel, https://t.me/BrainsHacking to participate in prize drawings and…
-
Dogecoin $0.34
Dogecoin $0.34 🔥Go to our website, https://brainshacking.com. ‼️ Subscribe to the main channel, https://t.me/BrainsHacking to participate in prize drawings and…
-
🚨 🚨 🚨 🚨 30,000,000 #XRP (76,151,365 USD) transferred from #Upbit to unknown wallet
🚨 🚨 🚨 🚨 30,000,000 #XRP (76,151,365 USD) transferred from #Upbit to unknown wallet Details : Whale Alert 🔥Go to…
-
BrainsHacking

Watcher Guru
Watcher Guru 🔥Go to our website, https://brainshacking.com. ‼️ Subscribe to the main channel, https://t.me/BrainsHacking to participate in prize drawings and…
-
BrainsHacking

JUST IN: 🇨🇳 Chinese officials consider selling TikTok US to Elon Musk, Bloomberg reports. : Watcher Guru…
JUST IN: 🇨🇳 Chinese officials consider selling TikTok US to Elon Musk, Bloomberg reports. : Watcher Guru 🔥Go to our…
-
Pump fun: Fee Account transferred about 122,620 SOL to Kraken at 2:10 UTC+8 today through a wallet: 8sp5im…Rac3sM, worth about…
Pump fun: Fee Account transferred about 122,620 SOL to Kraken at 2:10 UTC+8 today through a wallet: 8sp5im…Rac3sM, worth about…
-
💵 💵 💵 50,000,000 #USDC (50,020,000 USD) minted at USDC Treasury
💵 💵 💵 50,000,000 #USDC (50,020,000 USD) minted at USDC Treasury Details : Whale Alert 🔥Go to our website, https://brainshacking.com.…
-
BrainsHacking

frxETH V2 is now live.
frxETH V2 is now live. $sfrxETH is the highest-yielding major liquid staked ETH, with hundreds of millions in TVL earning…
-
🚨 🚨 🚨 🚨 🚨 🚨 🚨 🚨 🚨 🚨 2,400 #BTC (227,011,078 USD) transferred from unknown wallet to #Gemini…
🚨 🚨 🚨 🚨 🚨 🚨 🚨 🚨 🚨 🚨 2,400 #BTC (227,011,078 USD) transferred from unknown wallet to #Gemini…
-
BrainsHacking

NEW: 🟠 Tether is officially Licensed in El Salvador 🇸🇻
NEW: 🟠 Tether is officially Licensed in El Salvador 🇸🇻 This milestone would finalize all formalities needed to finally relocate…
-
BrainsHacking

Robinhood to pay $45M SEC penalty for securities law violations, Including Identity theft and system security failures.
Robinhood to pay $45M SEC penalty for securities law violations, Including Identity theft and system security failures. – CNBC :…
-
BrainsHacking

Bitcoin’s surge drove weekly trade volumes across 40+ centralized exchanges to $213 billion post-U.S. elections, the highest sin…
Bitcoin’s surge drove weekly trade volumes across 40+ centralized exchanges to $213 billion post-U.S. elections, the highest since May 2021.…
-
FOX Business reporter Eleanor Terrett reported that U.S. Senator Elizabeth Warren sent a 31-page letter to Treasury Secretary no…
FOX Business reporter Eleanor Terrett reported that U.S. Senator Elizabeth Warren sent a 31-page letter to Treasury Secretary nominee Scott…
-
JUST IN: 🇺🇸 Donald Trump’s inauguration will feature tech leaders and a “Crypto Ball” honoring him as the “first crypto presid…
JUST IN: 🇺🇸 Donald Trump’s inauguration will feature tech leaders and a “Crypto Ball” honoring him as the “first crypto…
-
BrainsHacking

Bankless hosts David Hoffman and Ryan Sean Adams faced criticism following accusations of dumping Aiccelerate’s Solana-based AIC…
Bankless hosts David Hoffman and Ryan Sean Adams faced criticism following accusations of dumping Aiccelerate’s Solana-based AICC token. – Protos…
-
Bitcoin price today: back above $94k as dip buyers return after sell off
Bitcoin price today: back above $94k as dip buyers return after sell off https://www.investing.com/news/cryptocurrency-news/bitcoin-price-today-falls-for-3rd-straight-day-to-94k-on-fed-rate-jitters-3808365
-
Moemate Starts Ecosystem Development with $Mates Launch of 6m+ Users on 14th January
Moemate Starts Ecosystem Development with $Mates Launch of 6m+ Users on 14th January https://www.investing.com/news/cryptocurrency-news/moemate-starts-ecosystem-development-with-mates-launch-of-6m-users-on-14th-january-3810409
-
BrainsHacking
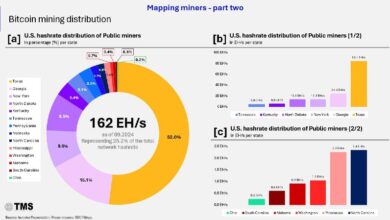
🇺🇸 Texas mines more than half (52%) of America’s new bitcoin everyday ⚡️ : Bitcoin
🇺🇸 Texas mines more than half (52%) of America’s new bitcoin everyday ⚡️ : Bitcoin 🔥Go to our website, https://brainshacking.com.…
-
20,192,563 #XLM (8,504,637 USD) transferred from #Binance Withdrawals to Scam
20,192,563 #XLM (8,504,637 USD) transferred from #Binance Withdrawals to Scam Details : Whale Alert 🔥Go to our website, https://brainshacking.com. ‼️…
-
JUST IN: 🇺🇸 President-elect Trump expected to repeal crypto accounting policy requiring banks holding digital assets to count …
JUST IN: 🇺🇸 President-elect Trump expected to repeal crypto accounting policy requiring banks holding digital assets to count them as…
-
Ripple $2.5
Ripple $2.5 🔥Go to our website, https://brainshacking.com. ‼️ Subscribe to the main channel, https://t.me/BrainsHacking to participate in prize drawings and…
-
Bitcoin $93,000
Bitcoin $93,000 🔥Go to our website, https://brainshacking.com. ‼️ Subscribe to the main channel, https://t.me/BrainsHacking to participate in prize drawings and…
-
According to The Washington Post, David Sacks and the Trump transition team are working closely with cryptocurrency industry lea…
According to The Washington Post, David Sacks and the Trump transition team are working closely with cryptocurrency industry leaders to…
