How Operation ShadowCat Targets Indian Politics

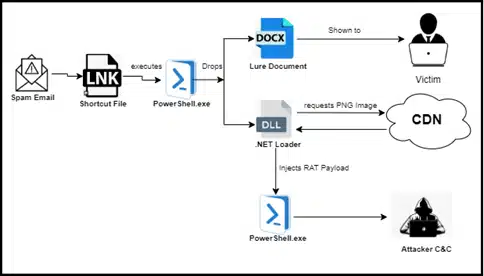
The infection process unfolds with a PowerShell command embedded within the .LNK file, initiating the download and execution of a .NET loader.
Ashish Khaitan July 25, 2024

Share on LinkedInShare on Twitter
Cybersecurity researchers have uncovered a sophisticated cyber espionage campaign dubbed “Operation ShadowCat”. This operation, orchestrated by a suspected Russian-speaking hacker group, employs advanced techniques to infiltrate systems, primarily targeting individuals with a vested interest in Indian political affairs.
ShadowCat begins with the distribution of malicious files disguised as innocuous documents related to Indian parliamentary proceedings. These files, often in the form of deceptive .LNK shortcuts masquerading as legitimate Office documents, serve as the initial point of entry for unsuspecting victims.
Once executed, these shortcuts trigger a sequence of events orchestrated to deploy a stealthy Remote Access Trojan (RAT) onto the victim’s machine.
Unravelling Operation ShadowCat
Attack-Chain of Operation ShadowCat ()
According to Cyble Research and Intelligence Labs (CRIL), the infection process unfolds with a PowerShell command embedded within the .LNK file, initiating the download and execution of a .NET loader. This loader is crucial as it acts as a conduit for delivering the final payload—a RAT written in the Go programming language.
This RAT is designed not only to establish persistent control over compromised systems but also to facilitate further malicious activities, including the deployment of ransomware and exfiltration of sensitive data.
The cybercriminals behind ShadowCat leverage sophisticated techniques to evade detection and maintain persistence. Central to their strategy is the use of steganography—a method of concealing malicious payloads within seemingly innocuous PNG images hosted on Content Delivery Networks (CDNs).
By embedding Gzip-compressed payloads within these images, the attackers ensure that the malicious code remains hidden until runtime, thereby bypassing traditional security measures.
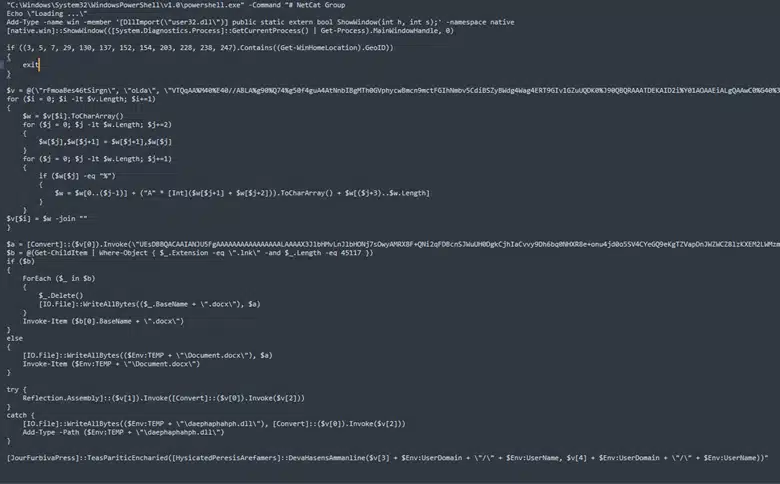
Malicious PowerShell script ()
Moreover, the deployment of the RAT involves intricate steps, including Asynchronous Procedure Call (APC) injection into the PowerShell.exe process. This technique allows the malware to execute its payload discreetly, leveraging the unsuspecting host system’s resources without raising questions.
Targeted Audience and Countermeasures
The choice of lures—documents related to Indian political affairs—suggests a deliberate targeting strategy aimed at specific individuals within the political, journalistic, and analytical communities. Potential victims include government officials, political analysts, journalists, researchers, and think tanks actively monitoring and reporting on Indian parliamentary proceedings. This selective targeting highlights the strategic intent of the threat actors to acquire sensitive information and potentially influence political narratives.
Interestingly, the attackers have implemented geo-location-based execution prevention mechanisms to exclude certain regions, particularly those where Russian-speaking communities reside. This geographical exclusion tactic provides further clues pointing toward the origin or affiliation of the threat actors behind the Operation.
The Operation represents a sophisticated cyber espionage campaign targeting individuals interested in Indian political affairs. To defend against such threats, organizations and individuals are urged to implement rigorous cybersecurity measures. This includes enhancing email security protocols to effectively detect and quarantine suspicious attachments, especially those with .LNK extensions.
Additionally, deploying advanced endpoint protection solutions is essential to identify and mitigate PowerShell-based attacks and malicious .NET loaders. Furthermore, educating users about the risks posed by phishing attacks and social engineering tactics is crucial in building resilience against cyber espionage campaigns.