HealthCare.gov Data Breach Claim: 7,500 Users Likely Affected
The authenticity of the claim remains unverified, and HealthCare.gov officials have not yet responded to those claims
Krishna Murthy July 12, 2024

Share on LinkedInShare on Twitter
HealthCare.gov, the health insurance exchange website operated by the United States federal government, has reportedly suffered a data breach. A threat actor has reportedly orchestrated the HealthCare.gov data breach and claimed to have leaked database from the website on dark web which contains sensitive information of approximately 7,500 users.
The claim that HealthCare.gov had been compromised surfaced on July 11 on the data leak site BreachForums. The threat actor claimed that they were revealing the stolen database of 83,000 lines, which consists of the Personally Identifiable Information (PII) of 7,500 users, including their full names, phone numbers, email addresses, mailing addresses, cities, states and zip codes.

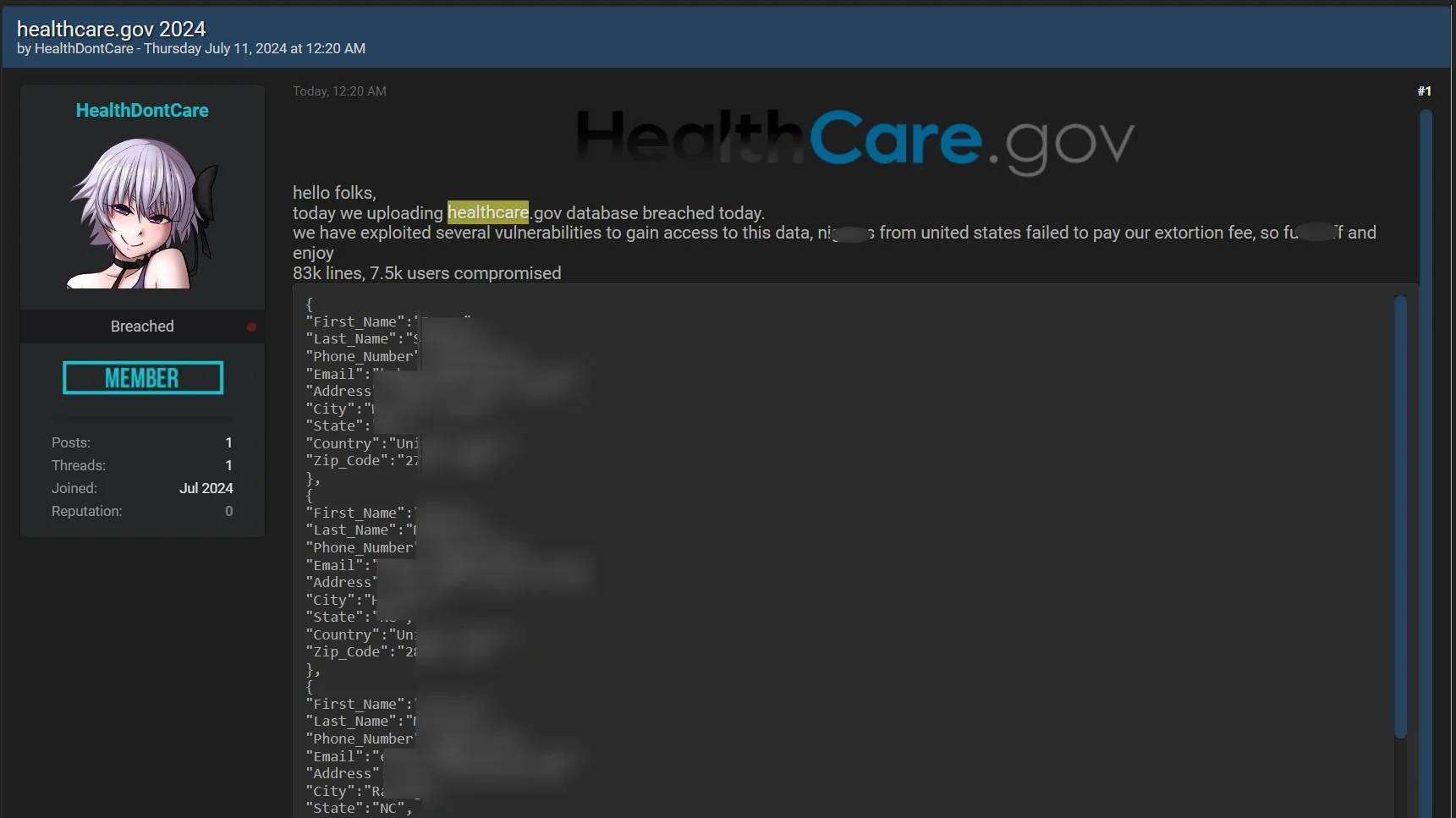
To substantiate the data breach claim, the threat actor, operating under the alias “HealthDontCare”, attached sample records in zip format.
In its claim, the bad actor wrote in the post, “Today we are uploading healthcare.gov database breached today. We have exploited several vulnerabilities to gain access to this data. N***ers from United States failed to pay our extortion fee, so f**k off and enjoy.”
Potential Impact of HealthCare.gov Data Breach
If proven, the potential consequences of this cyberattack could be critical as personal information about citizens could be exposed. The organization should take appropriate measures to protect the privacy and security of the stakeholders involved. Data breaches of this nature can lead to identity theft, potential financial frauds, and a loss of trust among citizens.
Currently, details regarding the extent of the HealthCare.gov Data Breach, the extent of data compromised, and the motive behind the cyber assault remain undisclosed.
Despite the claims made by the threat actor, the official HealthCare.gov website remain fully functional. This discrepancy has raised doubts about the authenticity of the threat actor’s assertion.
To ascertain the veracity of the claims, The Cyber Express has reached out to the officials of Centers for Medicare & Medicaid Services (CMS). As of the writing of this news report, no response has been received, leaving the cyberattack claim unverified.
HealthCare.gov Suffered Two Cyberattacks Previously
This is not the first time that HealthCare.Gov was under the scanner for data breaches. The CMS reported that sensitive data of 93,689 people was compromised during an October 16, 2018 data breach of HealthCare.Gov that targeted the Direct Enrollment pathway used by insurance agents and brokers. Initially the numbers of victims were estimated at 75,000.
According to an article by CNBC, the data breach in 2018 exposed personal details of victims including the last four digits of the Social Security number, immigration status and employer name. The exposed data consisted of information provided on insurance applications, as well as information from other federal agencies used to confirm the application details.
The breach forced CMS to shut down the Direct Enrollment pathway for a week while investigating the suspicious activity it noticed on the portal.
Owing to the breach, the CMS reached out to all affected consumers by phone and mailed notification letters to offer free credit protection and additional services to prevent and remediate issues arising from unauthorized use of data exposed as a result of the breach, including identity monitoring services, identity theft insurance, and identity restoration services.
In 2014 too, hackers had uploaded malware to a test server of HealthCare.gov. However the CMS then put out a statement that, “Our review indicates that the server did not contain consumer personal information; data was not transmitted outside the agency, and the website was not specifically targeted. We have taken measures to further strengthen security.”





