Hacker Advertises Chrome Sandbox Escape Exploit For $1M

The asking price for this exploit was set at an exorbitant $1 million, payable in cryptocurrencies like Monero or Bitcoin.
Ashish Khaitan June 27, 2024

Share on LinkedInShare on Twitter
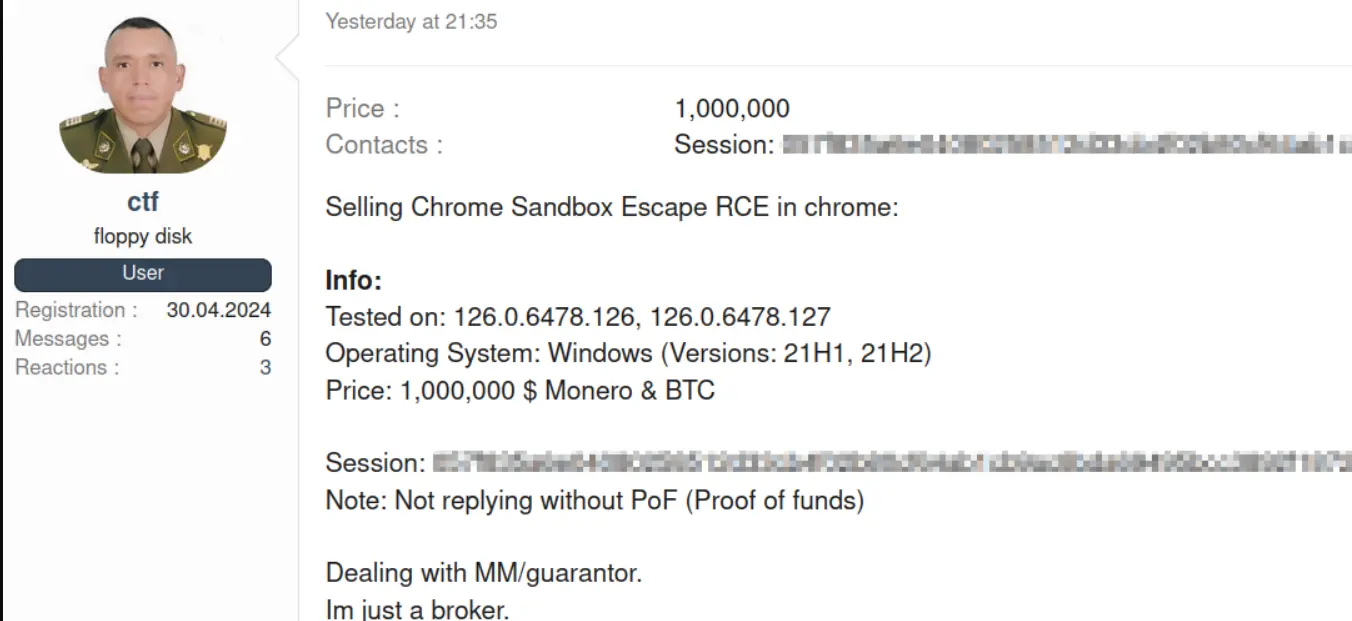
A dark web actor is advertising a zero-day exploit targeting Google Chrome. The exploit specifically targets versions 126.0.6478.126 and 126.0.6478.127 of Google Chrome for Windows, specifically the 21H1 and 21H2 versions. This exploit, which allows for Sandbox escape, was put up for sale by a threat actor identified as ‘ctf’ on the XSS forum.
The threat actor’s post on the forum detailed the nature of the exploit, highlighting its capability to execute remote code on affected systems potentially. The asking price for this exploit was set at an exorbitant $1 million, payable in cryptocurrencies like Monero or Bitcoin.
Notably, the threat actor did not provide a proof-of-concept demonstration but insisted on dealing through a mutually agreed-upon guarantor or middleman.
Dark Web Actor Selling Sandbox Escape Exploit
Source: Dark Web
Sandbox escape vulnerabilities like these pose a significant risk by allowing malicious actors to break out of the confinement typically imposed by security measures such as sandboxes.
Such exploits can enable attackers to execute arbitrary code on a system beyond the restricted environment, thereby potentially compromising sensitive data or even gaining full control over the affected machine.
In a separate incident earlier this year, vulnerabilities in the sandboxing mechanism of Judge0, an online code execution system, were also reported.
These vulnerabilities, described as critical, could similarly enable attackers to perform sandbox escapes and gain root permissions on the host machine. Tanto Security, an Australian cybersecurity firm, highlighted the severity of these flaws, which could be exploited to achieve a complete system takeover.
The Threat of Sandbox Escape Vulnerabilities
Judge0, known for facilitating online code execution for various applications including e-learning platforms and code editors, experienced these vulnerabilities due to issues in its sandbox setup scripts.
Specifically, flaws in the isolation mechanism allowed attackers to manipulate symbolic links and execute arbitrary code outside the designated sandbox environment.
The ongoing emergence of such sandbox escape vulnerabilities highlights the importance of cybersecurity practices and prompt patch management.
Organizations and individuals are advised to remain vigilant, apply security updates promptly, and employ defense-in-depth strategies to mitigate the risks posed by such exploits.