GootLoader Malware Employs Time-Based Delay Techniques

Researchers Detail Node.js Bypass of GootLoader Anti-Analysis Techniques
Alan J July 6, 2024

Share on LinkedInShare on Twitter
GootLoader, a sophisticated JavaScript-based malware has continued to confound cybersecurity experts with its unique evasion techniques. However, researchers have discovered a new method to circumvent its anti-analysis methods through debugging it as Node.js code in Visual Studio Code.
The research has cast new light on the malware’s inner workings and highlighted various flaws in common sandbox-based analysis methods.
Debugging GootLoader’s Evasive Techniques
While it is common among malware to perform sleep operations through the calling of the Wscript.sleep() or setTimeout() methods, most malware sandboxes easily detect these ‘malware sleeping’ methods. However, GootLoader employs advanced time-based delays and loop iterations for more effective evasion that can trick most sandbox environments.

Source: unit42.paloaltonetworks.com
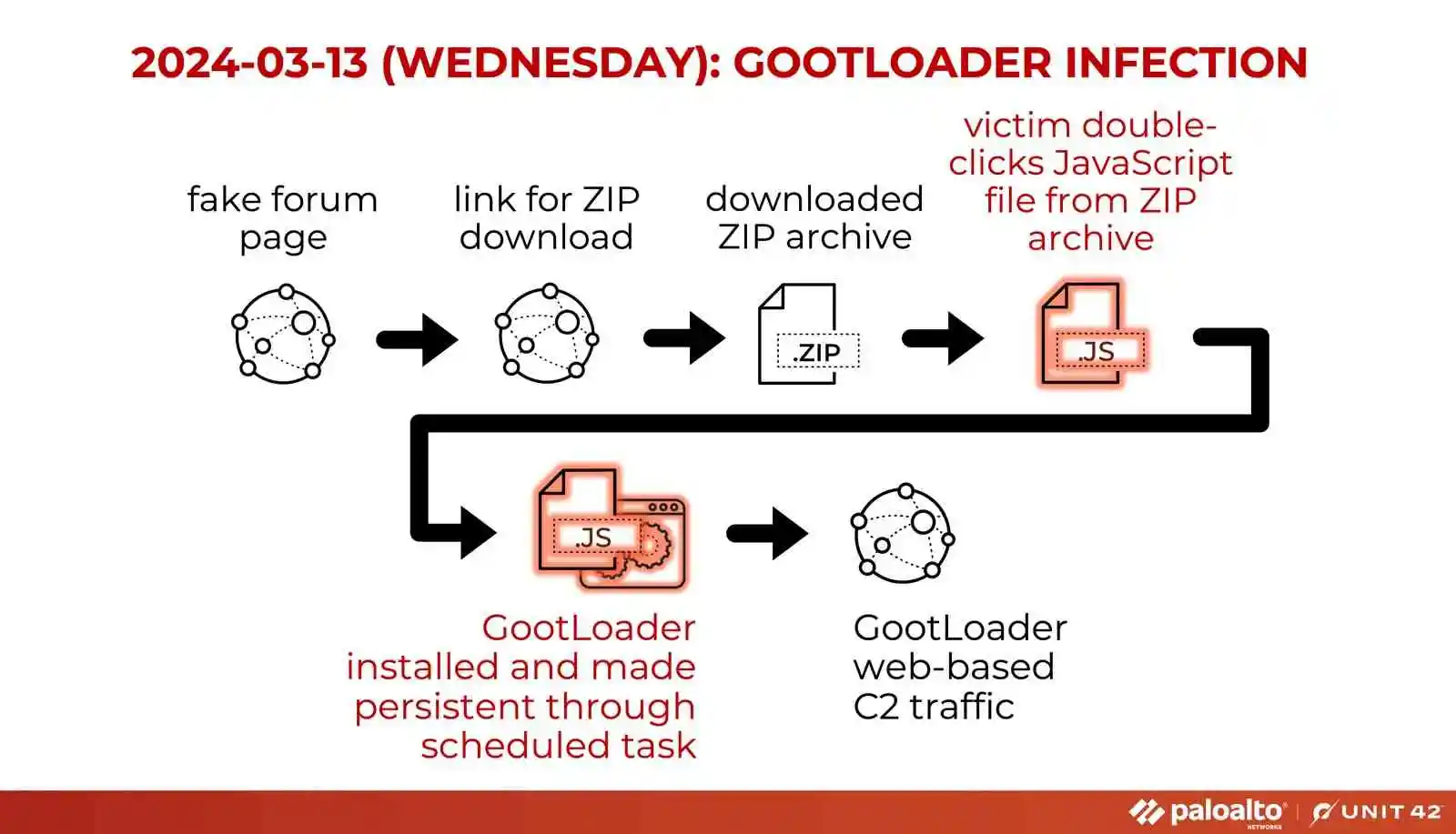
While Gootkit had been first identified in 2014, it has undergone many changes over time. The original Gootkit malware consisted a Windows executable, but since 2020 Javascript-based variants of the malware named as Gootkit Loader, were spotted being distributed through through the use of fake forum posts.
GootLoader can be used deliver several other types of malware, including ransomware. Despite these changes, the group has retained the same distribution tactics in 2024, with the forum posts nearly identical in content and appearance.
Researchers from Palto Alto Networks analyzed a GootLoader malware sample through the novel use of Node.js debugging in Visual Studio Code on a Windows host. This approach allowed for step-by-step code execution and breakpoint setting, providing further insights into the malware’s flow control and execution logic than typical standalone execution.
The analysis revealed that the malware employs time-consuming while loops and array functions to deliberately delay the execution of its malicious code through the use of self-induced sleep periods to obfuscate its true nature.
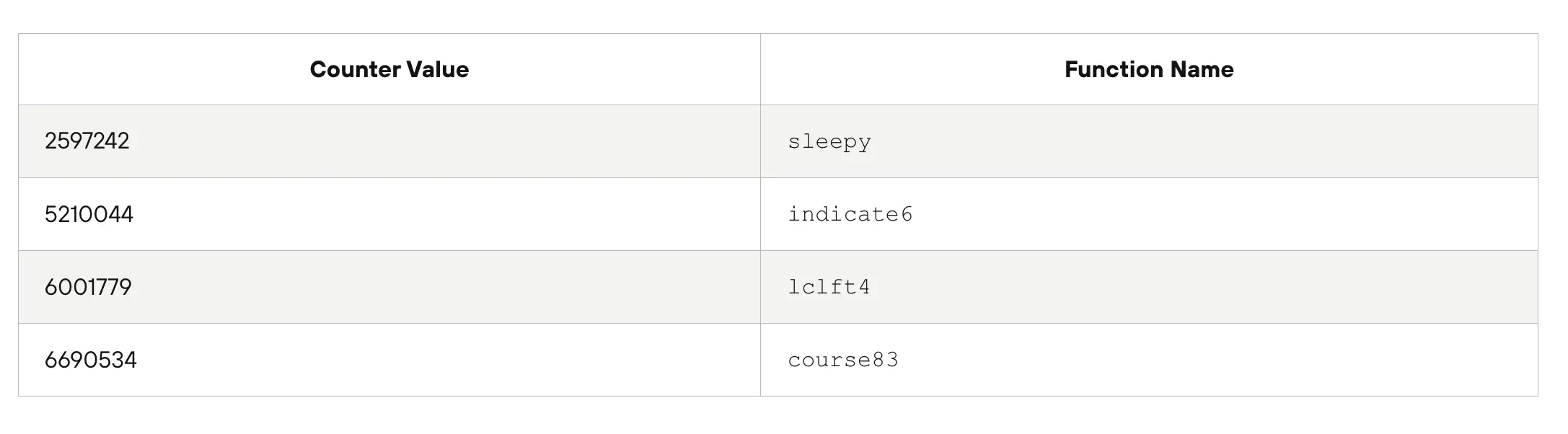
The researchers observed an infinite loop function, that supplied a variable with the same value on repeat , and upon stepping further into the malware‘s code, had discovered a ‘horseq7’ function array name. Upon analysis the code appeared to be stuck in a loop as it had taken over 10 minutes for the function to obtain the required counter value within the analysis environment.
This function appeared to be where the actual malicious program began execution, with the researcher identifying several different counter values and respective functions.

Source: unit42.paloaltonetworks.com
Flaws Within Sandbox Testing in Security Environments
Sandboxing techniques are commonly employed by security researchers to identify malicious binaries, their behaviour and execution within the benefit of a controlled environment. These sandboxes environments can face hurdles such as the passing of large volumes of binaries against limited resources.
GootLoader’s intricate evasive techniques present various hurdles for sandbox environments, particularly those with severely limited computing resources, and time-constrained analysis.
Understanding these techniques is crucial for researchers to develop more effective detection and analysis methods, such as enhanced sandbox environments to handle time-based evasion tactics and development of more sophisticated static and dynamic analysis tools which can potentially detect such circumventing functions.