Ghost Emperor Chinese-Linked Group Returns After 2 Years

Researchers observed operations from the threat actor group after an absence of over two years.
Alan J July 20, 2024

Share on LinkedInShare on Twitter
A China-linked hacking group known as Ghost Emperor has resurfaced with an updated version of its sophisticated Demodex rootkit, according to cybersecurity researchers. Ghost Emperor typically targets Southeast Asian telecom and government entities, and has modified its infection chain and added new evasion techniques to its malware arsenal.
New Ghost Emperor Demodex Infection Chain
GhostEmperor employs a multi-stage malware to achieve stealth execution and persistence and utilizes several methods to impede analysis process.
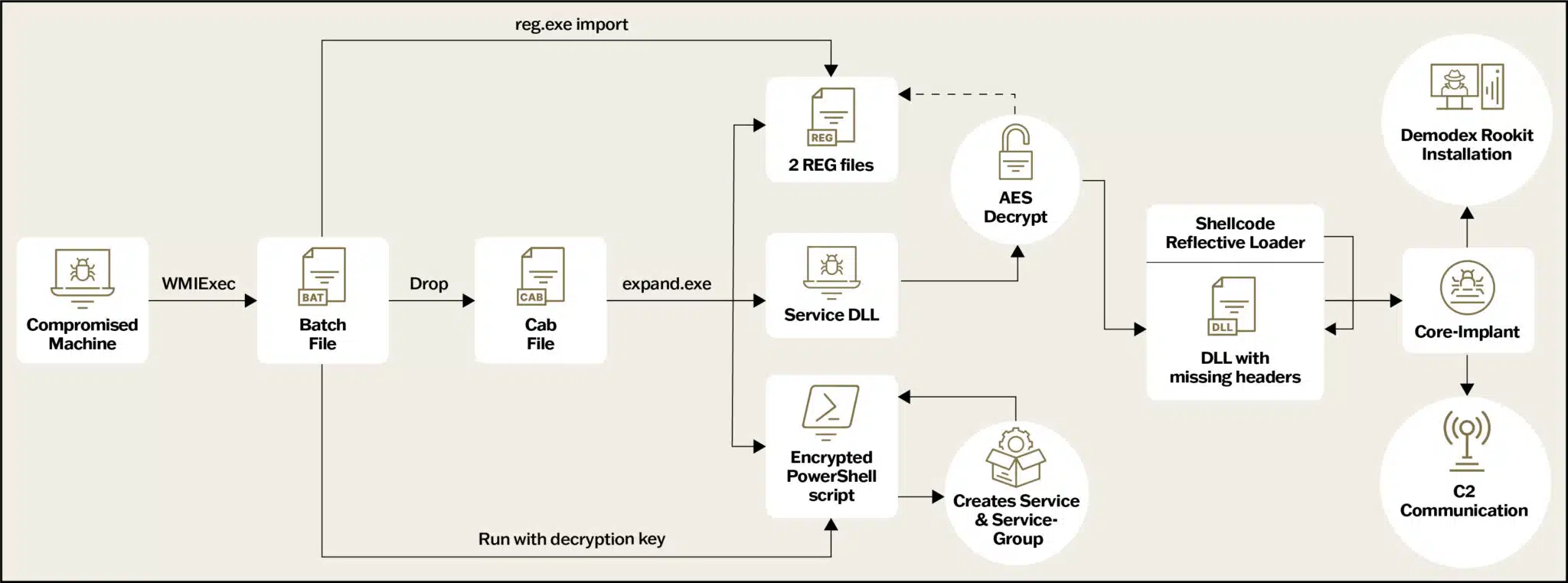
Source: sygnia.co
Researchers from Sygnia discovered that the updated Demodex infection chain begins when attackers use WMIExec, a remote execution tool, to run a batch file on the victim’s machine. The batch file drops a CAB file named “1.cab” to C:WindowsWeb, extracts four files, and imports two malicious registry files to target systems using the reg.exe import [file] command. The threat actor employs legitimate Microsoft tools, such as reg.exe and expand.exe, to achieve stealth in its attack operations.
After importing the registry keys, the batch file executes an encrypted PowerShell script to create a new service named “WdiSystem” to load a malicious Service DLL (prints1m.dll) file. The script also creates a service group called “WdiSystemhost” and runs the malicious service within this group, in order to masquerade the malware process as a legitimate Windows system process within the operating system.
The Service DLL dynamically loads necessary functions using an internal OS structure named Process Environment Block, accesses the LoadLibraryA function, and deciphers an encrypted configuration containing parameters such as initial sleep time, registry paths of the shellcode location, and a list of module and function names required for operation.
The security firm’s incident response team uncovered the new variant while investigating a network breach that affected both a client and its business partner. The malware, compiled in July 2021, shares similarities with a version analyzed by Kaspersky in 2021 but incorporates several key changes.
Enhanced Evasion Techniques
The attack operation employs an EDR evasion technique by setting a specific mitigation policy to its processes, forbidding the loading of DLLs that are not signed by Microsoft. This limits user-mode hooking and helps circumvent analysis tools. The service also reads two encrypted registry keys, decrypts the shellcode, and sets up a reflective loader to execute the core-implant DLL.
The researchers note that Ghost Emperor has implemented the following new methods to evade detection
- EDR Evasion: The malware sets a process mitigation policy that prevents loading of non-Microsoft signed DLLs, potentially blocking security software from injecting monitoring code.
- Dynamic Function Loading: The malicious DLL dynamically loads necessary functions, making static analysis more difficult.
- Encrypted Configuration: Key parameters, including registry paths and required function names, are stored in an encrypted configuration within the DLL.
- Reflective Loading: A position-independent shellcode acts as a reflective loader for the core implant, which is stored as a corrupted PE file to resist analysis.
The researchers have shared the following list of IOCs (Indicators of Compromise)
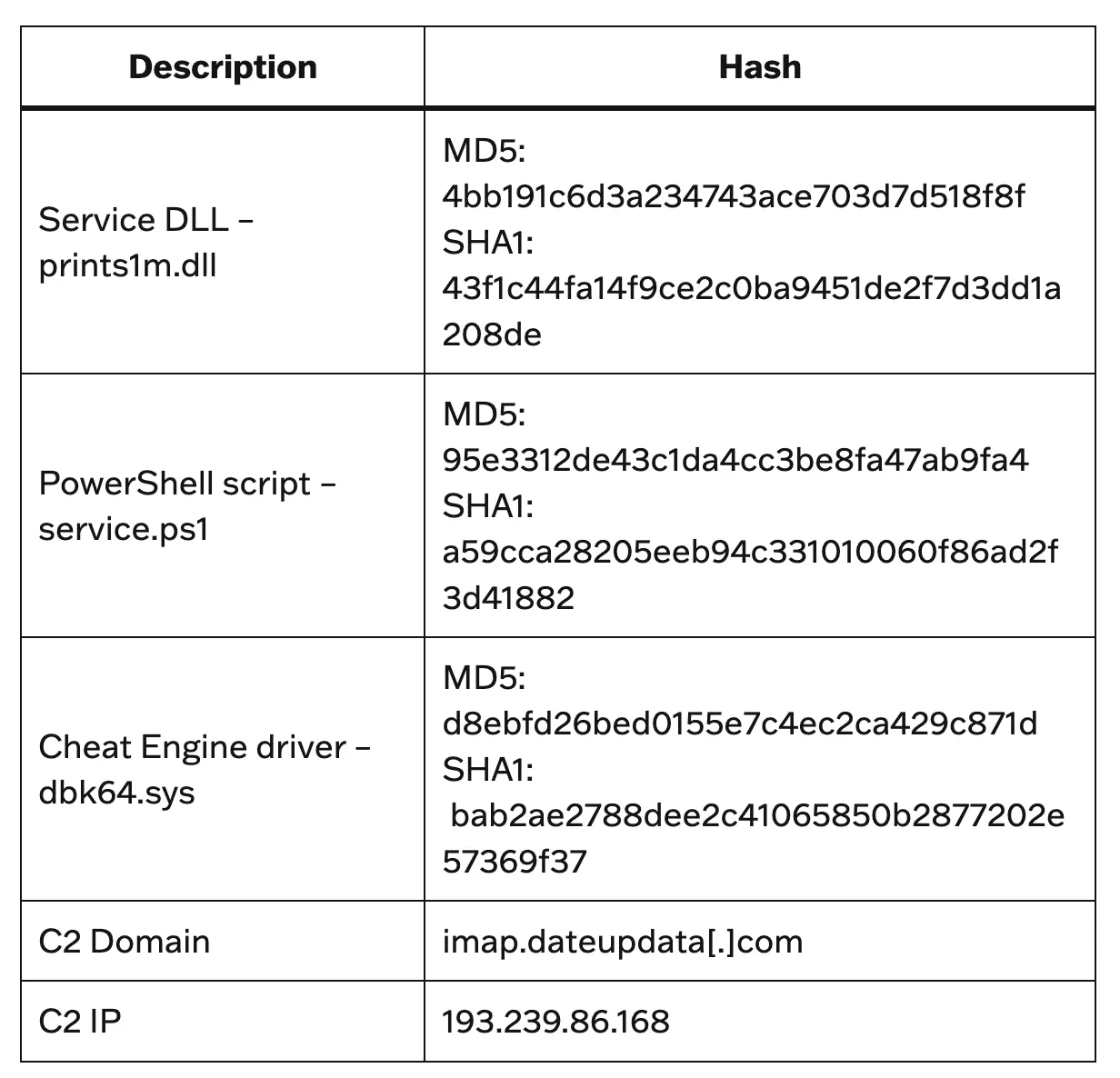
Source: sygnia.co
The Ghost Emperor threat actor group is the latest among several Chinese-linked APTs that demonstrate advanced techniques and evolved capabilities in its operations, raising concerns among governments, independent researchers and security firms about threats from the region.




