CRYSTALRAY Targets 1500 Victims Worldwide

The group abuses a wide range of legitimate open-source security tools to exploit known vulnerabilities and deploy backdoors.
Alan J July 12, 2024

Share on LinkedInShare on Twitter
A threat actor group dubbed ‘CRYSTALRAY’ has dramatically scaled up its attack operations, targeting over 1,500 victims worldwide with a sophisticated arsenal of open-source security tools. Researchers first observed the group’s activities in in February 2024 and have been observing its evolving tactics.
The group’s primary goals appear to be credential theft, cryptomining and maintaining persistent long-term access to compromised systems. The group’s tactics reflect a concerning trend of weaponization of legitimate open-source security tools by threat actor groups for malicious intent and illicit financial gain.
CRYSTALRAY Reconnaissance and Initial Access
Researchers from Sysdig observed that the group had significantly scaled up its operations, to target over targeting over 1,500 victims with the abuse of a wide range of legitimate open-source security tools to exploit known vulnerabilities and deploy backdoors.
CRYSTALRAY’s attack chain begins with careful reconnaissance of potential victims, the group uses tools from ProjectDiscovery, an open-source organization, to identify targets. CRYSTALRAY’s arsenal of tools includes zmap, asn, httpx, nuclei, platypus, and SSH-Snake.
To gain initial access, the group often modifies existing proof-of-concept exploits for known vulnerabilities, testing them before deployment against real-world targets. These operations tend to focus on specific countries, with the United States and China accounting for over half of their observed victims.

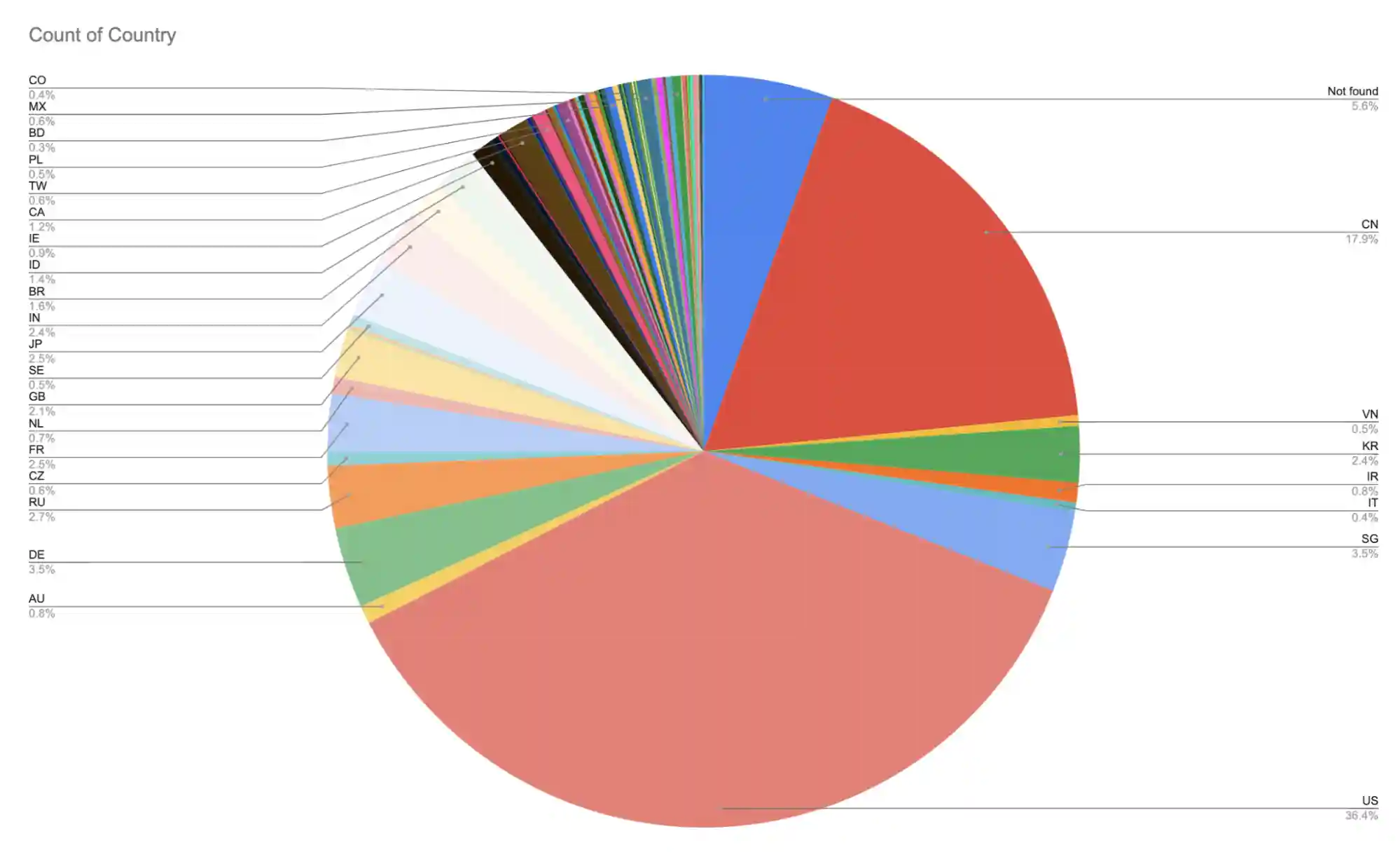
Chart of targeted countries (Source: sysdig.com)
The attackers employ a tool called “ASN” to generate lists of specific IP addresses for targeted countries. They then use “zmap,” a network scanner, to probe these IPs for vulnerabilities ripe for exploit in commonly-used platforms such as Confluence, Weblogic and ActiveMQ.
The httpx module is used to verify the presence of vulnerable running services with a httpx_output.txt file generated to filter invalid results. Nuclei is then used to perform vulnerability scans, identifying CVEs such as CVE-2022-44877 (Arbitrary command execution flaw), CVE-2021-3129(Another Arbitrary code execution flaw), and CVE-2019-18394 (Server-side request forgery).
Lateral Movement, Data Theft and Crypto-Mining
After breaching a system, CRYSTALRAY focuses on lateral movement and data collection. A key tool in their arsenal is SSH-Snake, an open-source worm that spreads through networks using stolen SSH credentials.

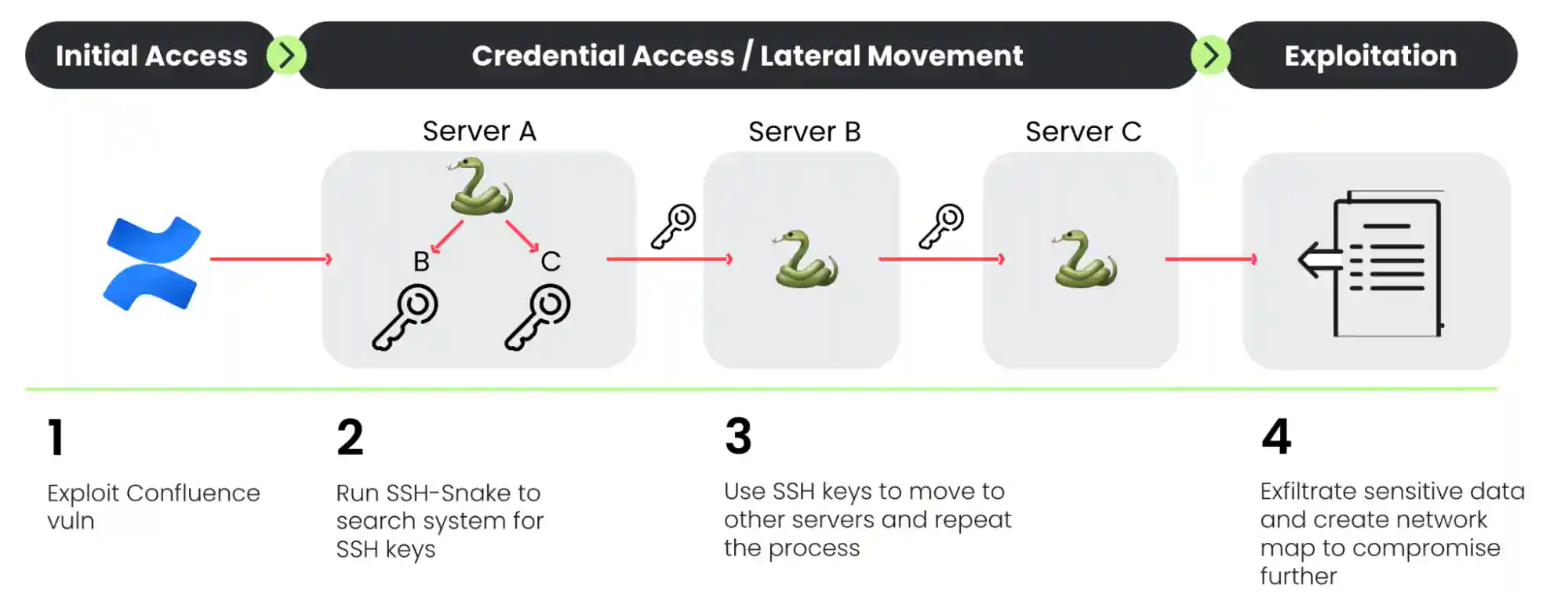
Source: sysdig.com
The group moves beyond server access and compromise, to search for credentials such as passwords or API keys of popular cloud providers stored as environment variables in files such as .env configurations, potentially allowing them to expand their reach into victims’ cloud infrastructure. The group automates the SSH-Snake tool to extract and exfiltrate credential data back to attacker-ownerd command-and-control servers.
Ultimately, the group deploys cryptominers on breached systems by hijacking the host’s processing power, with a script killing any existing cryptominers to maximize profit. While the researchers traced these deployed mining workers to a specific pool and discovered they were making roughly $200/month, starting in April, the group switched to a new configuration, making it impossible for the researchers to determine its current revenue.
Researchers have offered the following recommendations to protect against these attacks:
- Reduce potential cloud attack surface through secure vulnerability, identity, and secrets management to prevent automated attacks.
- Organizations required to expose applications to the public Internet, may face additional vulnerabilities and therefore should prioritize vulnerability remediation to reduce their risk of exposure
- Cameras/runtime detections that enable organizations to detect successful attacks and take immediate remediate action, allowing for in-depth forensic analysis to determine root cause of attacks.
The scale and sophistication of CRYSTALRAY’s operations highlight the growing threat posed by cybercriminals leveraging open-source security tools.





