CISA Advisory On GeoServer And GeoTools Vulnerabilities

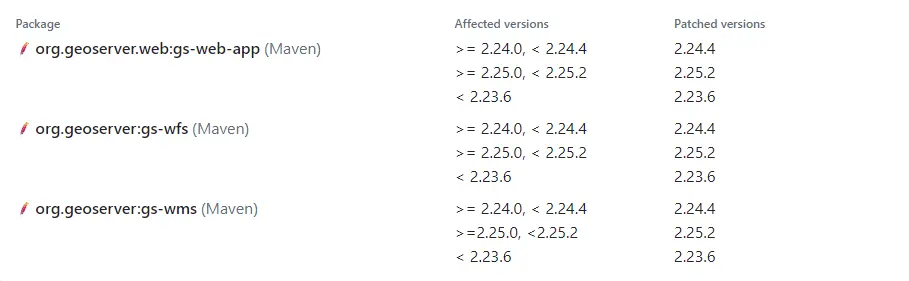
GeoServer and GeoTools versions before 2.23.6, 2.24.0-2.24.3, and 2.25.0-2.25.1 are vulnerable with a CVSS score of 9.8 under CVE-2024-36401 and CVE-2024-36404.
Ashish Khaitan July 16, 2024

Share on LinkedInShare on Twitter
The Cybersecurity and Infrastructure Security Agency (CISA) of the United States has issued a critical security advisory regarding vulnerabilities in GeoServer and GeoTools software, emphasizing the urgent need for action to mitigate potential risks.
These GeoServer and GeoTools vulnerabilities, particularly affecting versions before 2.23.6, 2.24.0 to 2.24.3, and 2.25.0 to 2.25.1, are categorized under the CVE-2024-36401 and CVE-2024-36404 identifiers, with a high CVSS score of 9.8.
Exploiting these vulnerabilities allows for remote code execution (RCE) through specially crafted input, posing serious threats to systems utilizing these open-source geospatial data management tools.
Exploring GeoServer and GeoTools Vulnerabilities
GeoServer, implemented in Java, serves as a critical server for sharing and editing geospatial data, adhering to Open Geospatial Consortium (OGC) standards such as Web Feature Service (WFS) and Web Coverage Service (WCS). Its integration with GeoTools, another essential Java library for geospatial data processing, further amplifies the impact of these vulnerabilities across a broad spectrum of geospatial applications.
According to the advisory released by GeoServer project maintainers, the vulnerability arises from improperly evaluating property names as XPath expressions. This flaw enables unauthenticated users to exploit multiple OGC request parameters, potentially executing arbitrary code within GeoServer instances. This exploitation can compromise the confidentiality, integrity, and availability of geospatial data, highlighting the critical nature of these vulnerabilities.
Furthermore, GeoTools, an underlying library leveraged by GeoServer for complex geospatial data operations, shares similar vulnerabilities involving XPath expression injections (CVE-2024-36404). These vulnerabilities stem from how GeoServer interacts with the GeoTools library API, inadequately handling element type attribute names passed to the commons-jxpath library. Malicious actors can exploit this oversight to inject crafted XPath expressions, facilitating unauthorized remote code execution.
The impact of these vulnerabilities extends to core functionalities of GeoServer and GeoTools, impacting operations reliant on geospatial data management and processing. The exploitation scenarios identified include vulnerabilities in WFS GetFeature, WFS GetPropertyValue, WMS GetMap, WMS GetFeatureInfo, WMS GetLegendGraphic, and WPS Execute requests, highlighting the breadth of potential attack vectors.
Mitigation Against Vulnerabilities in GeoServer and GeoTools Software

Source: GeoServer
To address these security concerns, immediate remediation measures are recommended. Users and administrators are advised to upgrade their GeoServer installations to versions 2.23.6 or later, 2.24.4 or later, and 2.25.2 or later. Similarly, GeoTools users should update to versions 29.6 or later, 30.4 or later, or 31.2 or later. These updates include patches that mitigate the identified vulnerabilities, reinforcing the security posture of GeoServer and GeoTools installations.
For users unable to immediately update, interim protection can be achieved by removing the vulnerable gt-complex-x.y.jar file from the GeoServer directory. This action, while effective in mitigating immediate risks, may temporarily affect certain functionalities dependent on this module. Organizations and users should carefully evaluate the trade-offs between security and operational continuity in implementing these measures.
The GeoServer and GeoTools vulnerabilities underscore the critical importance of proactive security practices within geospatial data environments. By promptly applying security updates and patches provided by the respective project maintainers, users can mitigate risks associated with the potential exploitation of these vulnerabilities.
GeoServer and GeoTools are foundational components in geospatial data processing, widely adopted for their robust capabilities in managing and serving geospatial information. However, the discovery of vulnerabilities by CISA emphasizes the need for vigilance and proactive security measures in open-source software ecosystems.





