Chrome To ‘Distrust’ Entrust Certificates: A Shakeup For Web Security

Concerning pattern of “compliance failures, unmet improvement commitments, and the absence of tangible, measurable progress” led to the decision, said Google Chrome
Mihir Bagwe June 29, 2024

Share on LinkedInShare on Twitter
Google’s Chrome browser is making a significant security move by distrusting certificates issued by Entrust, a prominent Certificate Authority (CA), beginning late 2024. This decision throws a wrench into the operations of numerous websites including those of major organizations like Bank of America, ESPN, and IRS.GOV, among others.
Digital certificates (SSL/TLS) play a vital role in ensuring secure connections between users and websites. These certificates issued by trusted CAs act as a security seal – more like a blue tick for websites – and helps users gauge the legitimacy of the website. It also ensures an encrypted communication to prevent data breaches.
However, Chrome is removing Entrust from its list of trusted CAs due to a concerning pattern of “compliance failures, unmet improvement commitments, and the absence of tangible, measurable progress” over the past six years. Entrust’s repeated shortcomings in upholding security standards have led Google to lose confidence in their ability to act as a reliable CA.
“It is our opinion that Chrome’s continued trust in Entrust is no longer justified.” – Google Chrome
This move also extends to AffirmTrust, a lesser-known provider acquired by Entrust. While these certificates account for only a small fraction (0.1%) compared to Let’s Encrypt (49.7%), the impact is still significant considering organizations like Bank of America, BookMyShow, ESPN and even government websites like IRS.gov, which have high internet traffic volumes, are also certified by Entrust.
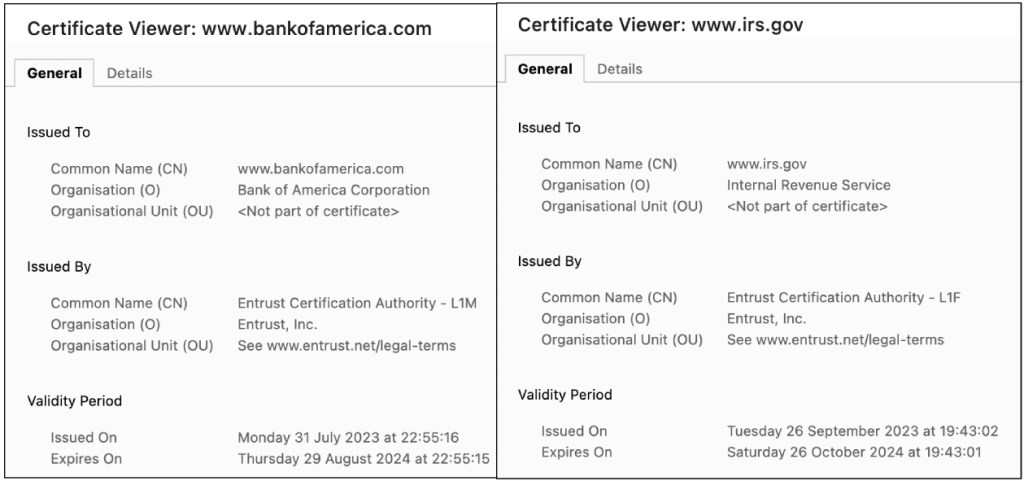
Bank of America and IRS.gov certificates as displayed on Chrome Certificate Viewer
What This Means for Users and Website Owners
Starting November 1, 2024, Chrome users encountering websites with distrusted Entrust certificates will be met with a full-page warning proclaiming the site as “not secure.”
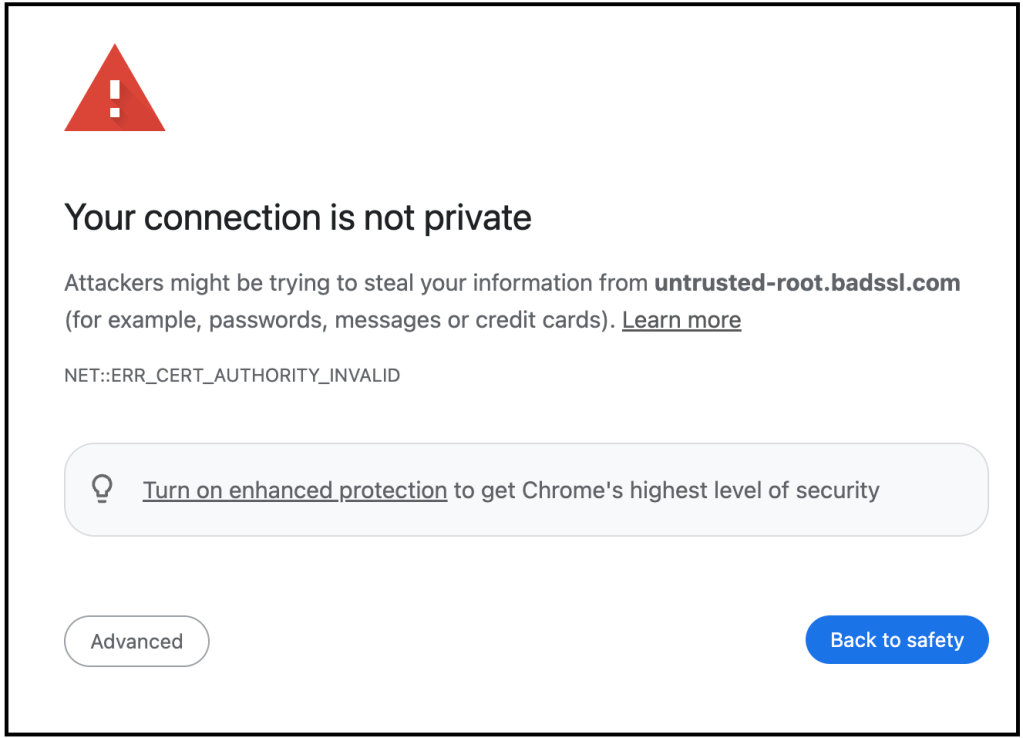
Sample of how Chrome will display warning for websites having a certificate from Entrust or AffirmTrust (Source: Google)
This warning only applies to certificates issued after October 31, 2024, providing a grace period for websites with existing Entrust certificates. However, as certificates have lifespans, website owners must transition to a different CA before expiration. Considering its market share Let’s Encrypt, a free and trusted option, comes highly recommended.
This shift is crucial for maintaining a secure web environment. When a CA fails to meet expectations, it jeopardizes the entire internet ecosystem. Chrome’s decision prioritizes user protection by eliminating trust in potentially compromised certificates.
Website owners using impacted Entrust certificates should act swiftly to switch to a different CA. The Chrome Certificate Viewer can be used to identify certificates issued by Entrust. While this may seem inconvenient, it’s necessary to ensure continued user access without security warnings.
Potential Workaround Only on Internal Networks
Large organizations managing internal networks have some leeway. Chrome allows enterprises to bypass these changes by installing the affected certificates as trusted on their local networks. This ensures internal websites using these certificates function normally.
The Entrust Controversy: A Deeper Look
Further context emerges from discussions on Mozilla’s Bug Tracker (Bug 1890685). It reveals a critical issue – Entrust’s failure to revoke a specific set of Extended Validation (EV) TLS certificates issued between March 18 and 21, 2024. This violated their own Certification Practice Statement (CPS).
Entrust opted against revoking the certificates, citing potential customer confusion and denying any security risks. However, this decision sparked outrage. Critics emphasized the importance of proper revocation procedures to uphold trust in the CA system. Entrust’s prioritization of customer convenience over security raised concerns about their commitment to strict adherence to security best practices.
A detailed post on Google Groups by Mike Shaver sheds further light on the situation. Shaver expresses doubt in Entrust’s ability to comply with WebPKI and Mozilla Root Store Program (MRSP) requirements. Despite attempts to address these concerns, Entrust’s handling of certificate revocation, operational accountability, and transparency remain under scrutiny.
Shaver points out Entrust’s tendency to prioritize customer convenience over strict adherence to security standards. He also criticizes the lack of detailed information regarding organizational changes and Entrust’s failure to meet Mozilla’s incident response requirements. Until Entrust demonstrates substantial improvements and transparency, continued trust in their certificates poses a significant risk to the overall web PKI and the security of internet users.
But this is not the end of it. In fact it is just the tip of the ice berg. Shaver’s comments in the forum are in response to a host of compliance incidents between March and May related to Entrust. Ben Wilson summarized these recent incidents in a dedicated wiki page.
“In brief, these incidents arose out of certificate mis-issuance due to a misunderstanding of the EV Guidelines, followed by numerous mistakes in incident handling including a deliberate decision to continue mis-issuance,” Wilson said.
This is a very serious shortcoming on Entrust’s behalf considering the stringent norms and root store requirements, he added.
However, Chrome’s decision to distrust Entrust certificates sends a strong message – prioritizing user safety requires holding CAs accountable for upholding the highest security standards.





