BlackBasta Ransomware Attack: Client, Employee Data At Risk?

Gang claims access to sensitive client, executive, employee data and more at financial services and retail firms.
Krishna Murthy June 25th, 2024

Share on LinkedInShare on Twitter
The notorious BlackBasta ransomware group is claiming credit for carrying out cyberattacks on major multinationals in the U.S. The ransomware gang claims it has access to sensitive data of financial services firm Key Benefit Administrators and healthcare apparel retailer Scrubs & Beyond.
BlackBasta was recently suspected to have exploited a Microsoft zero-day prior to Microsoft’s release of a patch for the vulnerability back in March.
Decoding BlackBasta Ransomware’s Alleged Attack
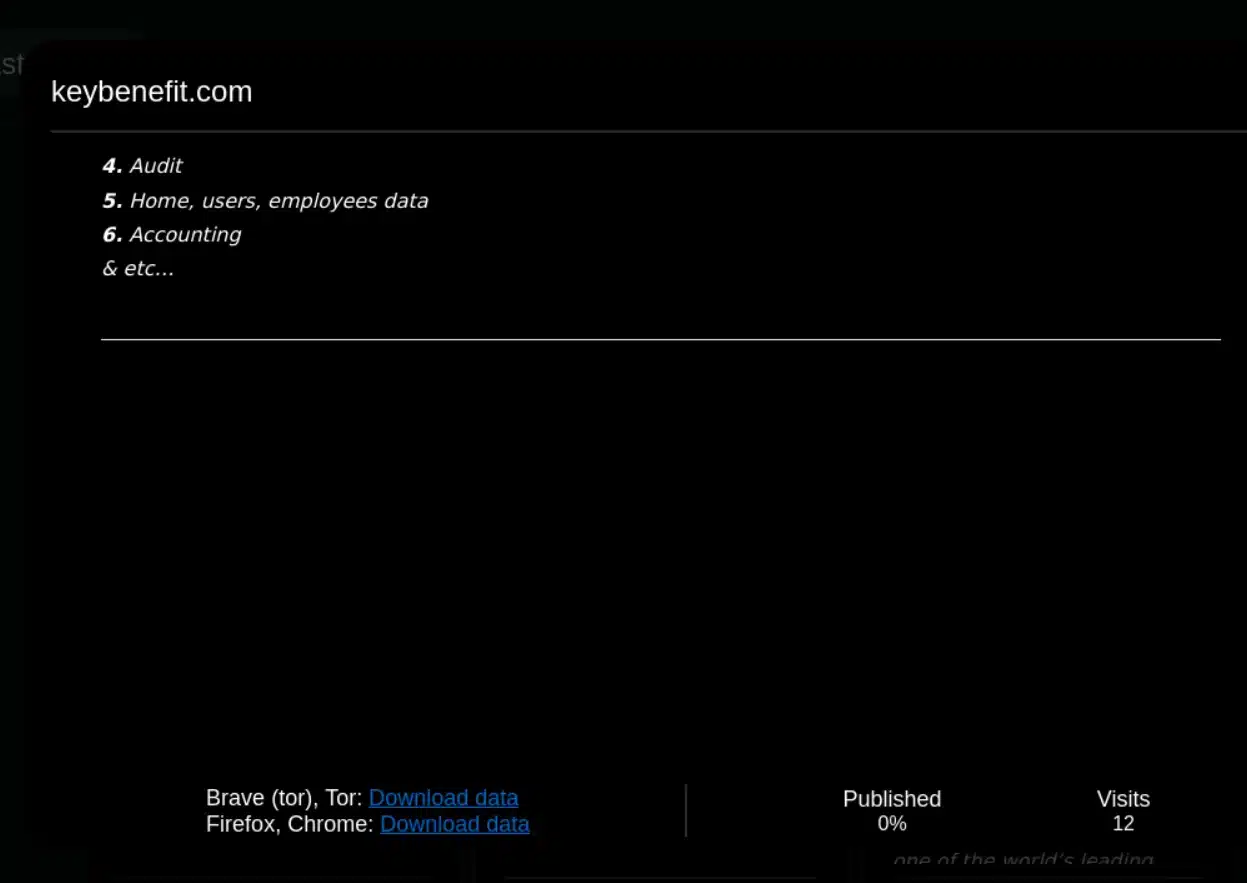
The first organization targeted by BlackBasta is Key Benefit Administrators, Inc., which offers financial services. The company provides employment benefit services that manages pension, retirement, health, and welfare funds. BlackBasta claims to have access to 2.5TB of sensitive data of the firm, including client, executive, and employee info.
Source: Ransomware.live
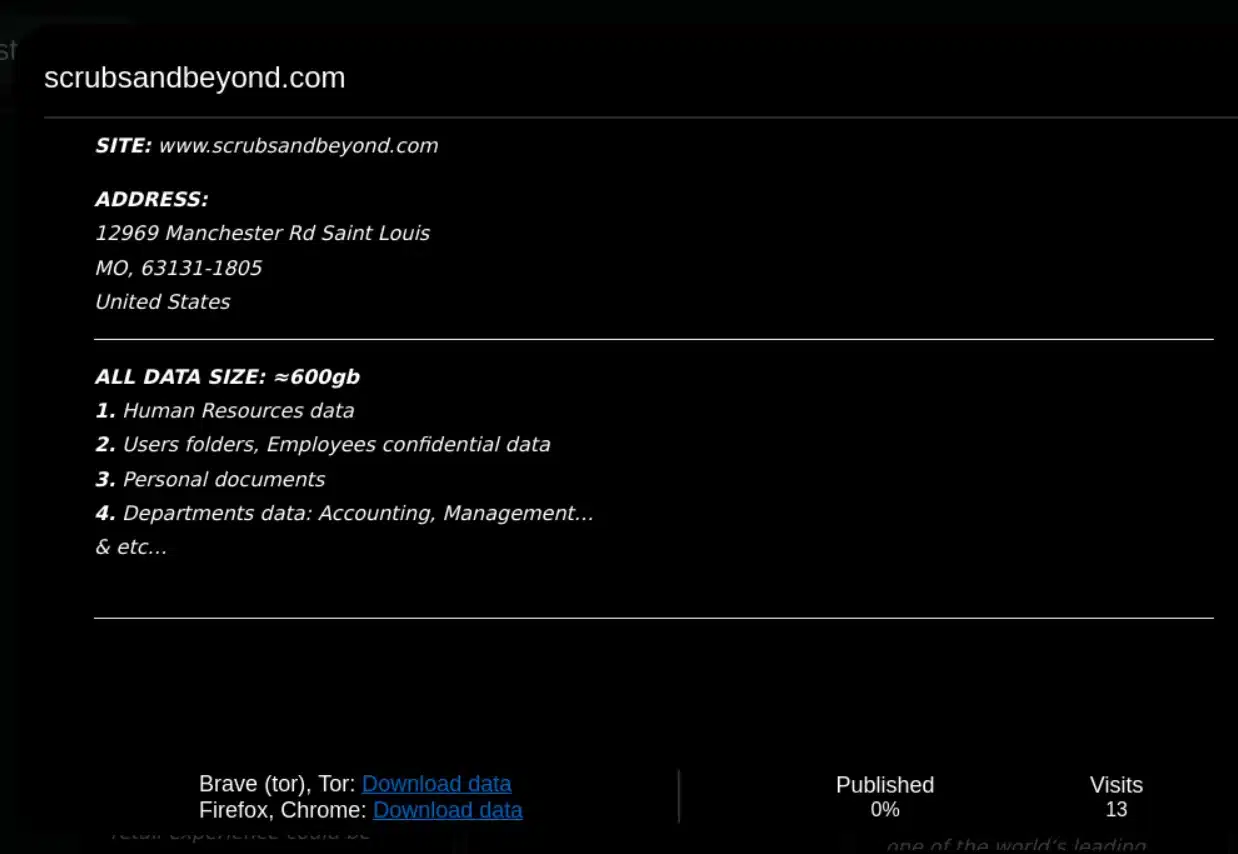
The other organization targeted by the ransomware group is Scrubs & Beyond, which is the largest retailer of healthcare apparel and accessories in the U.S.
The ransomware crew claims to have accessed 600GB of the organization’s sensitive data, including HR, employee, and departmental files.
Source: Ransomware.live
Until an official statement is released by the two firms, the facts behind the BlackBasta ransomware attack claim will likely remain elusive.
If BlackBasta’s claims are proven true, the implications could be significant. The compromise of sensitive legal information and client data could have broad consequences, not only for the firms concerned but also for its clients and partners.
How Does BlackBasta Group Operate?
BlackBasta is a highly active ransomware group that has quickly gained a reputation for targeting high-value organizations across various industries. BlackBasta typically uses sophisticated phishing campaigns, and exploits known vulnerabilities in software to obtain access to their targets’ systems. After gaining access, the group encrypts critical data and demands hefty ransoms for its release.
Previous Attacks By BlackBasta
A recent joint security advisory from the U.S. Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Department of Health and Human Services (HHS), and Multi-State Information Sharing and Analysis Center (MS-ISAC) stated that Black Basta has, through its affiliates, compromised more than 500 organizations all over the world.
The victims include organizations that span 12 of 16 critical infrastructure sectors, including the Healthcare and Public Health (HPH) sector. A few of BlackBasta’s victims include Microsoft, Hyundai Europe, Capita, The American Dental Association, Yellow Pages Canada, and Dish, among others.
How to Protect Against Ransomware
The ever-present threat of ransomware requires vigilant cybersecurity practices by consumers and organizations alike.
Keeping software and operating systems up-to-date: Many ransomware attacks exploit vulnerabilities in outdated software and operating systems. By keeping software and operating systems up-to-date, you can minimize the possibility of a ransomware attack.
Backing up important data: If your files are encrypted by ransomware, you may be able to restore them from a backup. By regularly backing up important data, you can increase the chances that you can recover your files if they are encrypted by ransomware. However, those backups should be immutable and ransomware-resistant – a good backup service provider may be your surest bet.
Using antivirus software: Antivirus software can detect and remove various types of malware, including ransomware. By using antivirus or endpoint security software, you can reduce the risk of a ransomware attack.
Being cautious of suspicious emails: Many ransomware attacks are spread via phishing emails. You can lower the risk of a ransomware attack by being wary of suspicious emails and refraining from clicking on links or opening attachments from unknown sources.
Educating employees about cybersecurity: Employees play a critical role in defending against cyberattacks. It is of utmost importance that they understand the best practices and know how to identify and report suspicious activities.
Isolating critical workloads and data: Isolating your most important data and applications with technologies such as microsegmentation, VLANs, firewalls and strict access and permission controls will create an extra layer of security that will make it that much harder for ransomware to infect your most critical systems.