Researchers Trace ‘GuardZoo’ Surveillance To Houthi Militia

While researchers are still analyzing the campaign, they have observed more than 450 unique IP addresses targeted by the tool.
Alan J July 10, 2024

Share on LinkedInShare on Twitter
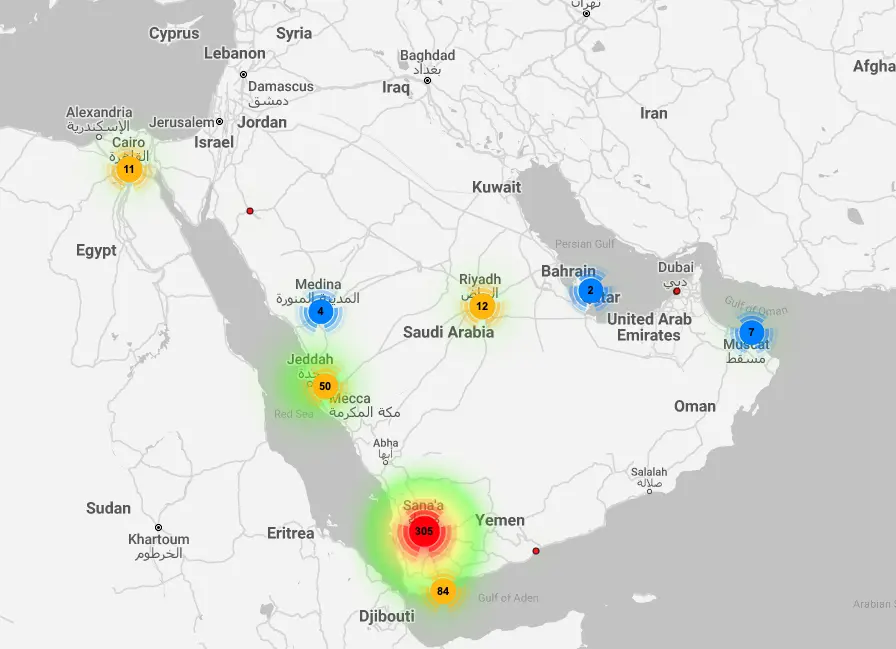
Cybersecurity researchers observed an Android surveillance campaign active since October 2019 that has targeted the military personnel of various countries in the Middle East. The researchers believe the operation has ties to a Houthi-aligned threat actor.
Referred to as “GuardZoo,” the spyware has infected devices belonging to more than 450 victims. The campaign remains active with researchers still analyzing related activity.
GuardZoo Infection of Middle Eastern Military Targets
GuardZoo is based on Dendroid RAT, an underground RAT program available for purchase at $300 that also included a binding utility to infect legitimate programs that had been leaked online in 2014.
Researchers noted many modifications to the original source code to implement additional capabilities while removing some unused functions. The GuardZoo malware uses a new C2 backend created with ASP.NET. instead of relying on the native Dendroid RAT’s PHP web panel for remote Command and Control (C2).
The researchers from Lookout attribute the campaign to a Yemeni, Houthi-aligned threat actor based on the application lures, exfiltrated data, targeting, and the C2 infrastructure location. The campaign has been observed to primarily target victims in Yemen, Saudi Arabia, Egypt, Oman, the UAE, Qatar, and Turkey.


Source: http://www.lookout.com

Source: http://www.lookout.com
The researchers observed the use of two C2 addresses, the first of which functioned as the primary address – https://wwwgoogl.zapto[.]org – and the second as a backup address: https://somrasdc.ddns[.]net. The malware is able to receive over 60 different commands from these C2 servers. These commands are mostly exclusive implementations to Guardzoo. The researchers compiled a list of some of the most notable C2 commands and their respective functions:

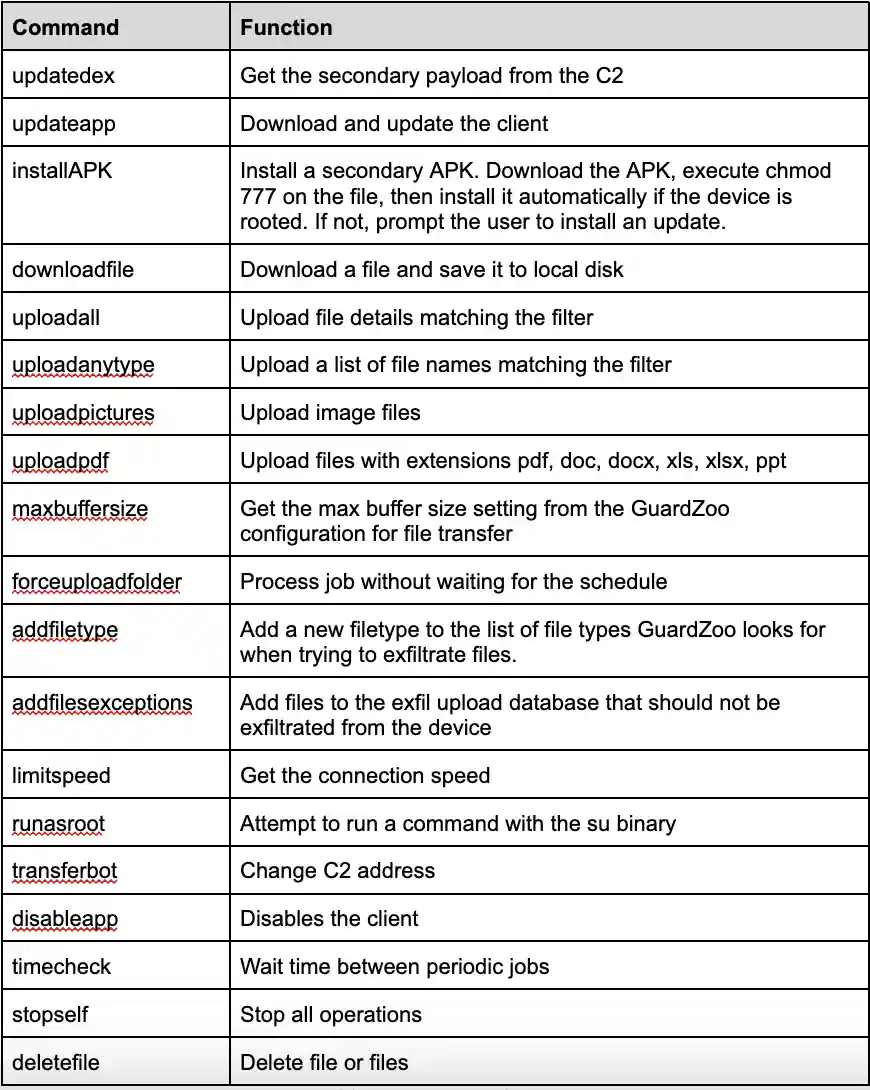
Source: http://www.lookout.com
GuardZoo can collect a wide range of data from infected devices, including photos, documents, location data, saved GPS routes and tracks, device model number, mobile carrier, and Wi-Fi configuration. Moreover, it can enable the actor to deploy additional invasive malware on the infected device. The device’s location, model, and cellular service carrier can also be collected.
The surveillanceware is distributed via WhatsApp, WhatsApp Business, and direct browser download, and uses military themes to lure victims. Lookout researchers have observed recent samples of GuardZoo posing as religious, e-book, and military-themed apps, such as ‘The Holy Quran,’ ‘Constitution of the Armed Forces,’ ‘Limited – Commander and Staff,’ and ‘Restructuring of the New Armed Forces.’


Source: http://www.lookout.com
Researchers Trace Houthi Connection
Researchers found evidence linking GuardZoo to Yemen’s Houthi militia, which the U.S. government recently redesignated as a global terrorist group.
Analysis of server logs revealed that many of the identified victims appeared to be members of the pro-Hadi forces in Yemen. Additionally, the malware’s C2 servers were found to be hosted on YemenNet infrastructure belonging to an ISP that is state-owned by the Yemeni government.
Researchers noted that some of the log entries indicated that the devices belonged forces aligned with President Hadi’s government that operates from Aden. One of the exfiltrated documents contained phrases that translated to “Very Confidential, Republic of Yemen, Ministry of Defense, Chief of the General Staff, War Operations Department, Insurance division.“
Protection Against GuardZoo
Aaron Cockerill, Executive Vice President of Product & Security at the security firm, stated, “These spyware packages can be used to collect a wide range of data from infected devices, which in the case of GuardZoo, could put military personnel and operations at risk. We urge security professionals to be aware of this threat and to take steps to protect their users, and work and personal data.”
To protect both business and personal Android devices from GuardZoo and other surveillanceware, the researchers have recommended the following basic steps:
- Keep your operating system and apps up to date, as most updates nowadays are related to security patches.
- Only install apps from Google Play, not third-party sources. If you receive a message asking you to install an app from a website, immediately block the number and report the incident to your IT or Security team.
- Be mindful of the permissions that mobile apps ask for. Overly invasive permissions, even from legitimate apps, could create data risk for your organization.
- Implement a mobile security solution that can detect and protect against malware and keep your organization safe.





