Multiple Flaws Found In Emerson Rosemount Gas Chromatographs

The security team successfully emulated a gas chromatograph model to study potential vulnerabilities.
Alan J June 28, 2024

Share on LinkedInShare on Twitter
Security experts have identified multiple vulnerabilities in widely used industrial gas chromatographs manufactured by Emerson Rosemount. These flaws could potentially allow malicious actors to access sensitive information, disrupt operations and execute unauthorized commands.
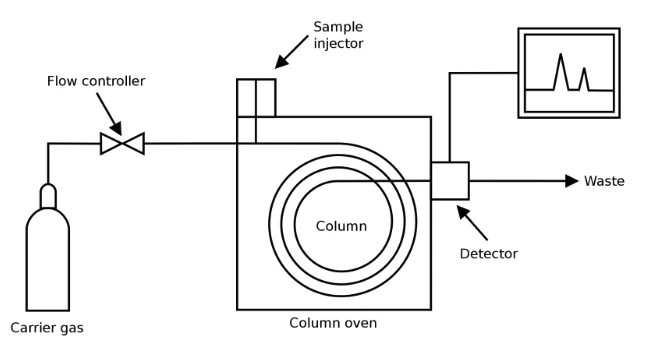
Gas chromatographs are critical instruments used for analyzing chemical compounds across a range of industries, including environmental facilities, hospitals, and food processing companies. These devices are critical for ensuring the accuracy of gas measurements and the safety of the environment, patients, and consumers.
Flaws in Emerson Rosemount Gas Chromatographs
Operational technology security firm Claroty discovered the vulnerabilities, which include two command injection flaws and two authentication bypass issues. If exploited, these flaws could enable unauthenticated attackers to run arbitrary commands, access sensitive data and gain administrative control.
Source: Wikipedia

Emulated system (Source: claroty.com)
To study the Emerson Rosemount 370XA gas chromatograph, commonly used in industrial settings for gas analysis, the researchers took efforts to emulate the systems. This complex process was undertaken because the physical device could cost over $100,000 while the research was limited to a six-week project.
The emulation process involved download and extraction of the device firmware from the official Emerson Rosemount website, and a search for an application that could implements its proprietary protocols. The researchers used the QEMU emulator to emulate the PowerPC architecture used by the gas chromatograph and run the extracted firmware. Upon investigation, the researchers were able to uncover four key vulnerabilities:
- CVE-2023-46687: Allows remote execution of root-level commands without authentication (CVSS score: 9.8)
- CVE-2023-49716: Enables authenticated users to run arbitrary commands remotely (CVSS score: 6.9)
- CVE-2023-51761: Permits unauthenticated users to bypass authentication and gain admin access by resetting passwords (CVSS score: 8.3)
- CVE-2023-43609: Allows unauthenticated users to access sensitive information or cause denial-of-service (CVSS score: 6.9)
The U.S. Cybersecurity and Infrastructure Security Agency issued an advisory in January warning that successful attacks could lead to “denial-of-service conditions” and unauthorized system access. The affected models include GC370XA, GC700XA and GC1500XA running firmware versions 4.1.5 and earlier.
Industry Impact and Mitigation
Gas chromatographs play a crucial role in various sectors, from environmental monitoring to medical diagnostics. Compromised devices could have far-reaching consequences.
In food processing, attacks on chromatographs might prevent accurate bacteria detection, halting production. In healthcare settings, disrupted blood sample analysis could impact patient care.
Emerson has released updated firmware addressing these vulnerabilities. The Claroty researchers said they “appreciate Emerson for its swift response and cooperation, which demonstrates their dedication to our shared goal.”
Emerson advises customers to apply the patches and implement best practices in the cybersecurity industry according to current standards.
The firm stated, “In addition, Emerson recommends end users continue to utilize current cybersecurity industry best practices and in the event such infrastructure is not implemented within an end user’s network, action should be taken to ensure the Affected Product is connected to a well-protected network and not
connected to the Internet.
In its advisory CISA shared the following recommendations for securing these systems:
- Minimize network exposure: Ensure that control system devices and/or systems, are not publicly accessible from the internet.
- Locate control system networks: Place remote devices behind firewalls and isolate them from business networks
- Secure Remote Access: Use Virtual Private Networks (VPNs) to secure remote access. However, the agency also warned of potential inherent risks in VPNs, asking organizations and businesses to be aware of them.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures,” the advisory stated.





