Critical SQL Injection Vulnerability In Fortra FileCatalyst Workflow

The vulnerability arises from improper input validation within the application's handling of SQL queries.
Ashish Khaitan June 27, 2024

Share on LinkedInShare on Twitter
A critical security flaw has been reported in Fortra FileCatalyst Workflow, a widely used platform designed for efficient file exchange and collaboration within private cloud environments.
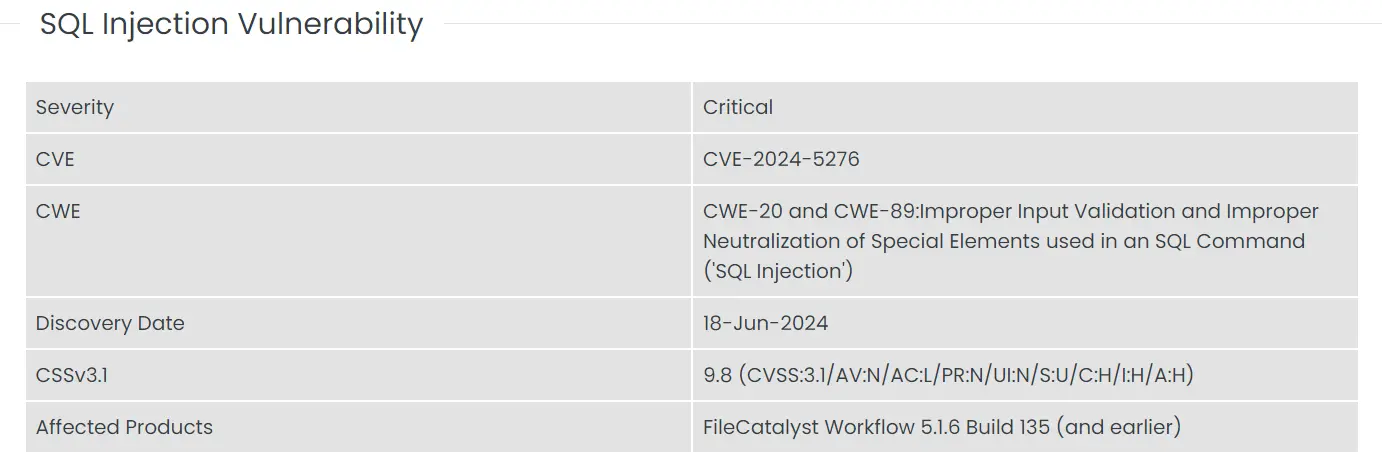
This vulnerability, identified as CVE-2024-5276, allows remote attackers to exploit SQL injection to potentially create unauthorized administrative accounts and manipulate the application’s database.
Fortra FileCatalyst Workflow serves as a pivotal tool for organizations requiring rapid and secure data transfers across large file sizes. It facilitates seamless collaboration in secure, private cloud spaces, making it indispensable for many businesses globally.
Understanding Fortra FileCatalyst Workflow Vulnerability
Source: Fortra
Tenable researchers discovered Fortra FileCatalyst Workflow vulnerability or CVE-2024-5276 on June 18, 2024, marking it as a critical vulnerability due to its potential impact. This flaw affects versions up to and including FileCatalyst Workflow 5.1.6 Build 135.
The vulnerability arises from improper input validation within the application’s handling of SQL queries, specifically through the ‘jobID’ parameter in various URL endpoints. Exploitation of this flaw can allow attackers to inject malicious SQL code, thereby gaining unauthorized access to the system.
Fortra promptly addressed the issue following Tenable’s responsible disclosure. In their security bulletin, Fortra clarified that while the vulnerability allows for the creation of admin users and manipulation of data, it does not facilitate data theft directly.
They have released a fix in FileCatalyst Workflow version 5.1.6 Build 139, which patches the vulnerability and is strongly recommended for all users.
Mitigation and Upgrade Steps
Users of affected versions (up to Build 135) are advised to upgrade immediately to the patched version (Build 139) to mitigate the risk of exploitation. For those unable to upgrade immediately, disabling anonymous access on the Workflow system can reduce exposure to potential attacks leveraging CVE-2024-5276.
As of the latest reports, there have been no documented cases of CVE-2024-5276 being actively exploited. However, given the severity of the vulnerability and the availability of exploit details, organizations are urged to prioritize updates to safeguard their systems against potential threats.
The identification and swift response to CVE-2024-5276 highlight the critical importance of proactive security measures in maintaining the integrity and confidentiality of organizational data. Fortra’s proactive approach in releasing a patch highlights the rise of vulnerabilities within internet devices and the security of user data.
For more information on CVE-2024-5276 and to download the latest patched version of FileCatalyst Workflow, visit the official Fortra FileCatalyst Workflow website.