Russian Hackers Used New Backdoors To Spy On European MFA

Dubbed “LunarWeb” and “LunarMail” these novel backdoors are attributed to the Turla cyberespionage group, believed to be aligned with Russian interests
Mihir Bagwe May 16th, 2024

Share on LinkedInShare on Twitter
Researchers recently uncovered two new backdoors implanted within the infrastructure of a European Ministry of Foreign Affairs (MFA) and its diplomatic missions.
Slovakian cybersecurity firm ESET who found these two new backdoors dubbed “LunarWeb” and “LunarMail,” attributed them to the Turla cyberespionage group believed to be aligned with Russian interests.
Turla has operated since at least 2004, possibly starting in the late 1990s. Linked to the Russian FSB, Turla primarily targets high-profile entities like governments and diplomatic organizations in Europe, Central Asia and the Middle East. Notably, they have breached significant organizations such as the US Department of Defense in 2008 and the Swiss defense company RUAG in 2014.
Researchers believe the Lunar toolset that has been used since at least 2020 is an addition to the arsenal of Russia-aligned cyberespionage group Turla based on the similarities between the tools’ tactics, techniques, and procedures (TTPs) and past activities.
LunarWeb Backd: Used to Navigate the Digital Terrain
LunarWeb backdoor stealthily infiltrates servers, establishing its foothold within the targeted infrastructure. Operating covertly, it communicates via HTTP(S) while mirroring legitimate traffic patterns to obfuscate its presence.
Concealment is key in LunarWeb’s playbook. For this the backdoor used steganography technique. This backdoor covertly embeds commands within innocuous images, effectively evading detection mechanisms.
LunarWeb’s loader, aptly named LunarLoader, showcases remarkable versatility, the researchers noted. Whether masquerading as trojanized open-source software or operating in standalone form, this entry point demonstrates the adaptability of the adversary’s tactics.
LunarMail: Used to Infiltrate Individual Workstations
LunarMail takes a different approach as compared to LunarWeb. It embeds itself within Outlook workstations. Leveraging the familiar environment of email communications, this backdoor carries out its spying activities remaining hidden amidst the daily deluge of digital correspondence that its victims receive on their workstations.

LunarMail Operation (credit: ESET)
On first run, the LunarMail backdoor collects information on the environment variables, and email addresses of all outgoing email messages. It then communicates with the command and control server through the Outlook Messaging API to receive further instructions.
LunarMail is capable of writing files, setting email addresses for C&C communication, create arbitrary processes and execute them, take screenshots and more.
Similar to its counterpart, LunarMail harnesses the power of steganography albeit within the confines of email attachments. By concealing commands within image files, it perpetuates its covert communication channels undetected.
LunarMail’s integration with Outlook extends beyond mere infiltration. It manipulates email attachments, seamlessly embedding encrypted payloads within image files or PDF documents which facilitates unsuspicious data exfiltration.
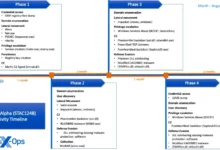
Initial Access and Discovery
The initial access vectors of the Turla hackers, though not definitively confirmed, point towards the exploitation of vulnerabilities or spearphishing campaigns. The abuse of Zabbix network monitoring software is also a potential avenue of compromise, the researchers said.
The compromised entities were primarily affiliated with a European MFA, which meant the intrusion was of a strategic nature. The investigation first began with the detection of a loader decrypting and running a payload from an external file, on an unidentified server.
This was a previously unknown backdoor, which the researchers named LunarWeb. A similar attack chain with LunarWeb was then found deployed at a diplomatic institution of a European MFA but with a second backdoor – named LunarMail.
In another attack, researchers spotted simultaneous deployments of a chain with LunarWeb at three diplomatic institutions of this MFA in the Middle East, occurring within minutes of each other.
“The attacker probably had prior access to the domain controller of the MFA and utilized it for lateral movement to machines of related institutions in the same network,” the researchers noted.
The threat actors displayed varying degrees of sophistication in the compromises. The coding errors and different coding styles used to develop the backdoors suggested that “multiple individuals were likely involved in the development and operation of these tools.”
Russian State Hackers Biggest Cyber Threat
Recently, Google-owned Mandiant in a detailed report stated with “high confidence” that Russian state-sponsored cyber threat activity poses the greatest risk to elections in regions with Russian interest including the European Union, the United Kingdom and the United States.
Russia’s approach to election interference is multifaceted, blending cyber intrusion activities with information operations aimed at influencing public perceptions and sowing discord.
Russian state-aligned cyber threat actors target election-related infrastructure for various reasons including applying pressure on foreign governments, amplifying issues aligned with Russia’s national interests, and retaliating against perceived adversaries. Groups like APT28 and UNC4057 conduct cyber espionage and information operations to achieve these objectives, Mandiant said.