New Chinese Espionage Threat Targeted Southeast Asian Government Organization

A sophisticated Chinese espionage threat group was discovered by Sophos researchers during a threat hunting exercise.
Paul Shread June 5th, 2024

Share on LinkedInShare on Twitter
Threat actors linked to Chinese state interests have been targeting an unnamed high-profile Southeast Asian government organization since at least March 2022, according to new research from Sophos.
The Chinese espionage threat, dubbed “Crimson Palace” by the researchers, was first observed in May 2023 by Sophos MDR’s Mark Parsons, who uncovered “a complex, long-running Chinese state-sponsored cyberespionage operation” during a threat hunt across Sophos Managed Detection and Response telemetry. The threat actors appear to remain active.
VMware DLL Sideloading Discovery Launched Investigation
MDR launched the hunt after the discovery of a DLL sideloading technique that exploited VMNat.exe, a VMware component, the Sophos researchers wrote in a report published today.
The investigation uncovered “at least three clusters of intrusion activity” between March 2023 and December 2023. The threat hunt uncovered previously unreported malware associated with the threat clusters, as well as a new improved variant of the EAGERBEE malware. Sophos is tracking the clusters as Cluster Alpha (STAC1248), Cluster Bravo (STAC1807), and Cluster Charlie (STAC1305).
“While our visibility into the targeted network was limited due to the extent to which Sophos endpoint protection had been deployed within the organization, our investigations also found evidence of related earlier intrusion activity dating back to early 2022,” the researchers wrote. “This led us to suspect the threat actors had long-standing access to unmanaged assets within the network.”
Chinese Espionage Threat Uses Familiar Tools and Infrastructure
The Crimson Palace clusters were found to use tools and infrastructure connected to Chinese threat actors BackdoorDiplomacy, REF5961, Worok, TA428, Unfading Sea Haze and the APT41 subgroup Earth Longzhi. Sophos “has observed the actors attempting to collect documents with file names that indicate they are of intelligence value, including military documents related to strategies in the South China Sea,” the report said.
“Though we are currently unable to perform high-confidence attribution or confirm the nature of the relationship between these clusters, our current investigation suggests that the clusters reflect the work of separate actors tasked by a central authority with parallel objectives in pursuit of Chinese state interests,” the researchers wrote.
Cluster Bravo appears to have been short lived, observed operating only in March 2023. Cluster Alpha’s last active known implant ceased C2 communications in August 2023, “and we have not seen the cluster of activity re-emerge in the victim network. However, the same cannot be said for Cluster Charlie.” Cluster Charlie has been active at least through April 2024.
“After a few weeks of dormancy, we observed the actors in Cluster Charlie re-penetrate the network via a web shell and resume their activity at a higher tempo and in a more evasive manner,” the researchers said. Activities included exfiltration efforts, and “instead of leaving their implants on disks for long periods of time, the actors used different instances of their web shell to re-penetrate the network for their sessions and began to modulate different C2 channels and methods of deploying implants on target systems.”
While the clusters had their own patterns of behavior, “the timing of operations and overlaps in compromised infrastructure and objectives suggest at least some level of awareness and/or coordination between the clusters in the environment,” they wrote.
The researchers detailed differences and overlaps between the clusters in a Venn diagram republished below.
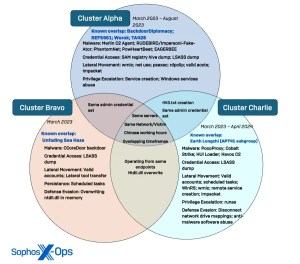
Tactics and overlap of the Crimson Palace threat clusters (source: Sophos)
Chinese Espionage Threat Uses Novel Malware, DLL, Evasion
Tactics of the Chinese espionage threat actors include accessing critical IT systems, performing reconnaissance of specific users, collecting sensitive military and technical information, and deploying various malware implants for command-and control (C2) communications.
Sophos researchers noted three key findings on the threat actors’ tools and tactics.
Novel malware variants: Researchers identified the use of previously unreported malware they call CCoreDoor that was concurrently discovered by BitDefender, and PocoProxy, and an updated variant of EAGERBEE malware with the ability to “blackhole communications to antivirus (AV) vendor domains in the targeted organization’s network.” Other malware variants they noted include NUPAKAGE, Merlin C2 Agent, Cobalt Strike, PhantomNet backdoor, RUDEBIRD malware, and the PowHeartBeat backdoor.
Extensive dynamic link library (DLL): Researchers observed more than 15 distinct DLL sideloading scenarios, most of which abused Windows Services, legitimate Microsoft binaries, and AV vendor software.
Prioritization of evasive tactics and tools: The researchers noted “many novel evasion techniques, such as overwriting dll in memory to unhook the Sophos AV agent process from the kernel, abusing AV software for sideloading, and using various techniques to test the most efficient and evasive methods of executing their payloads.”
Sophos cited 10 researchers for their work investigating the threat: Colin Cowie, Jordon Olness, Hunter Neal, Andrew Jaeger, Pavle Culum, Kostas Tsialemis, and Daniel Souter of Sophos Managed Detection and Response, and Gabor Szappanos, Andrew Ludgate, and Steeve Gaudreault of SophosLabs.





