CERT-IN Warns About Vulnerabilities In Palo Alto Networks

The vulnerabilities could allow attackers to gain unauthorized access, steal data, and execute malicious code. Palo Alto Networks has released patches to address these issues.
Krishna Murthy September 3, 2024 Reading Time: 3 mins read

Share on LinkedInShare on Twitter
The Indian Computer Emergency Response Team (CERT-IN) has issued advisories regarding critical vulnerabilities affecting several Palo Alto Networks applications. These vulnerabilities could allow attackers to gain unauthorized access to systems, steal sensitive information, and potentially execute malicious code.
CERT-In operates under the Ministry of Electronics and Information Technology (MeitY) in India and serves as the national agency responsible for cybersecurity. Its primary objective is to enhance the security of India’s information infrastructure and coordinate efforts to respond to cybersecurity incidents.
Vulnerabilities in Palo Alto Networks
The agency has identified three main vulnerabilities in Palo Alto Networks products: CVE-2024-5915, CVE-2024-5916, and CVE-2024-5914.
- GlobalProtect App: Privilege Escalation Vulnerability (CVE-2024-5915)
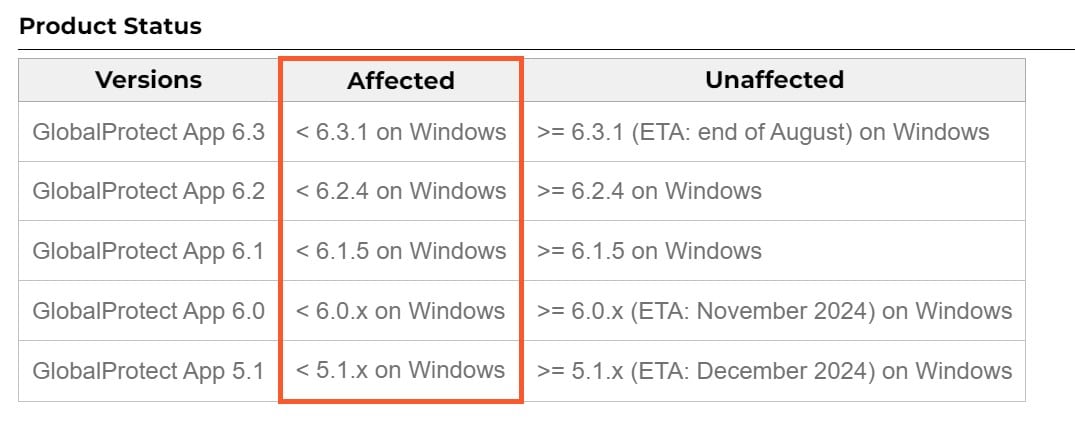
A critical vulnerability exists in older versions of the Palo Alto Networks GlobalProtect app, a software solution that enables secure remote access to corporate networks. A Privilege Escalation (PE) vulnerability in the app on Windows devices enables a local user to execute programs with elevated privileges.

Source: Palo Alto Networks
This vulnerability, classified as CVE-2024-5915, has been addressed in app versions later than 5.4.5. Users are strongly urged to update to the latest version (as of September 3, 2024) to mitigate this risk.
Privilege escalation is a serious security concern. By exploiting this vulnerability, an attacker with initial access to a system could potentially gain administrative privileges, allowing them to take full control of the system, steal sensitive data, or deploy malware.
- PAN-OS: Information Disclosure Vulnerability (CVE-2024-5916)
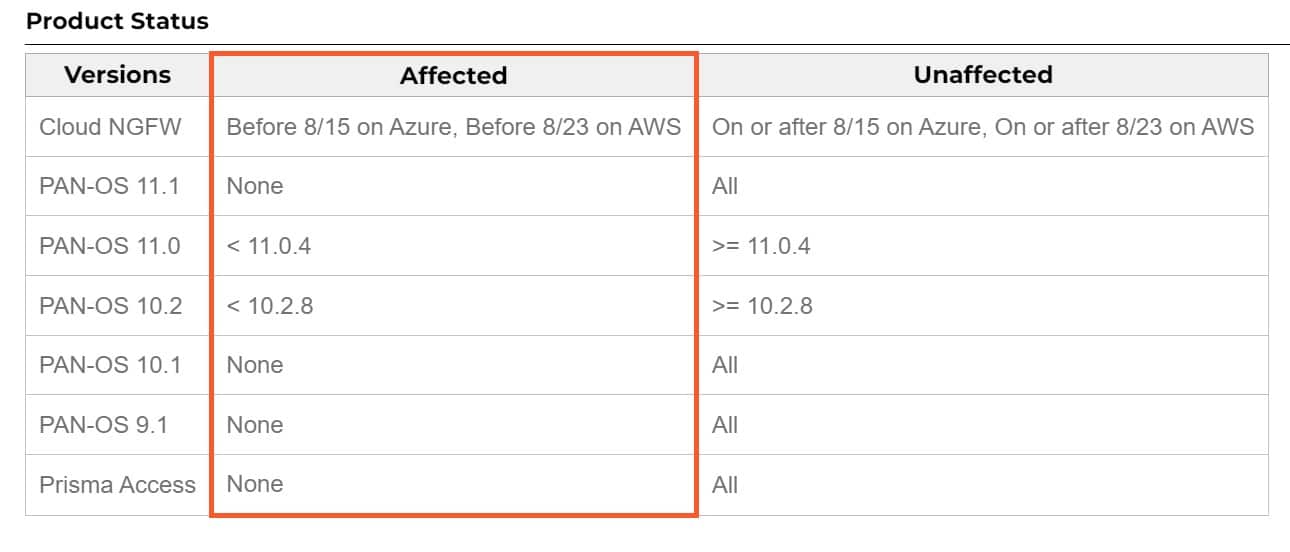
Another vulnerability, identified as CVE-2024-5916, affects Palo Alto Networks PAN-OS, a network security operating system. This vulnerability is classified as an “information exposure” issue.
An attacker who successfully exploits this vulnerability could potentially gain access to sensitive information, including passwords, secrets, and tokens used to access external systems. This information could be used to launch further attacks on the network or compromise external systems.

Source: Palo Alto Networks
The vulnerability reportedly allows even a read-only administrator with access to the configuration log to access these sensitive details. This highlights the importance of implementing the principle of least privilege, granting users only the minimum access level required to perform their tasks.
Resolution: This issue has been fixed in PAN-OS 10.2.8, PAN-OS 11.0.4, and all later PAN-OS versions. Additionally, users should revoke compromised secrets, passwords, and tokens that are configured in all server profiles of affected PAN-OS firewalls (Device > Server Profiles) after upgrading PAN-OS.
- Cortex XSOAR: Command Injection Vulnerability (CVE-2024-5914)
A third vulnerability, identified as CVE-2024-5914, resides within older versions of Palo Alto Networks Cortex XSOAR, a security automation platform. This vulnerability is classified as a “command injection” flaw within the CommonScripts Pack, a pre-built collection of scripts for automating security tasks.


Source: Palo Alto Networks
Command injection vulnerabilities allow attackers to inject malicious code into trusted applications. In the case of Cortex XSOAR, successful exploitation could allow attackers to execute arbitrary commands within the context of an integration container. This could potentially allow attackers to move laterally within the network, steal data, or disrupt security operations.
Resolution: This issue has been fixed in Cortex XSOAR CommonScripts version 1.12.33 or later. Users are strongly urged to update to the latest version to mitigate this risk.
Protecting Against the Palo Alto Networks Vulnerabilities
Palo Alto Networks has released patches to address these vulnerabilities. Users are strongly urged to update their affected software as soon as possible to mitigate these risks.
Here are some additional security recommendations:
- Implement the principle of least privilege, granting users only the access level required for their tasks.
- Regularly review and update security configurations.
- Enable multi-factor authentication (MFA) wherever possible.
- Maintain regular isolated backups of your systems.
By following these recommendations and promptly applying security patches, users can significantly reduce the risk of exploitation from these vulnerabilities.