0.0.0.0 Day Vulnerability Threat To Chrome, Safari, Mozilla

A newly discovered zero-day vulnerability, dubbed "0.0.0.0 Day," has exposed a critical flaw in major web browsers, allowing malicious actors to bypass security measures and potentially access sensitive user data.
Krishna Murthy August 8, 2024 Cybersecurity News, Firewall Daily, Vulnerabilities

Share on LinkedInShare on Twitter
A critical security flaw dubbed “0.0.0.0 Day” has sent shockwaves through the cybersecurity community, leaving millions of users of popular browsers like Chrome, Firefox, and Safari vulnerable to potential attacks. This vulnerability, allows malicious actors to potentially access files, messages, credentials, and other sensitive data stored on a device within a private network, specifically on the “localhost.”
What is 0.0.0.0 Day Vulnerability?
The term “0.0.0.0 Day” refers to a newly discovered vulnerability, discovered by Israeli cybersecurity startup Oligo, that attackers can exploit before a patch is available. The significance lies in the zeroes, signifying the lack of prior knowledge or awareness of vulnerability. This makes it particularly dangerous, as users and developers are caught completely off guard.

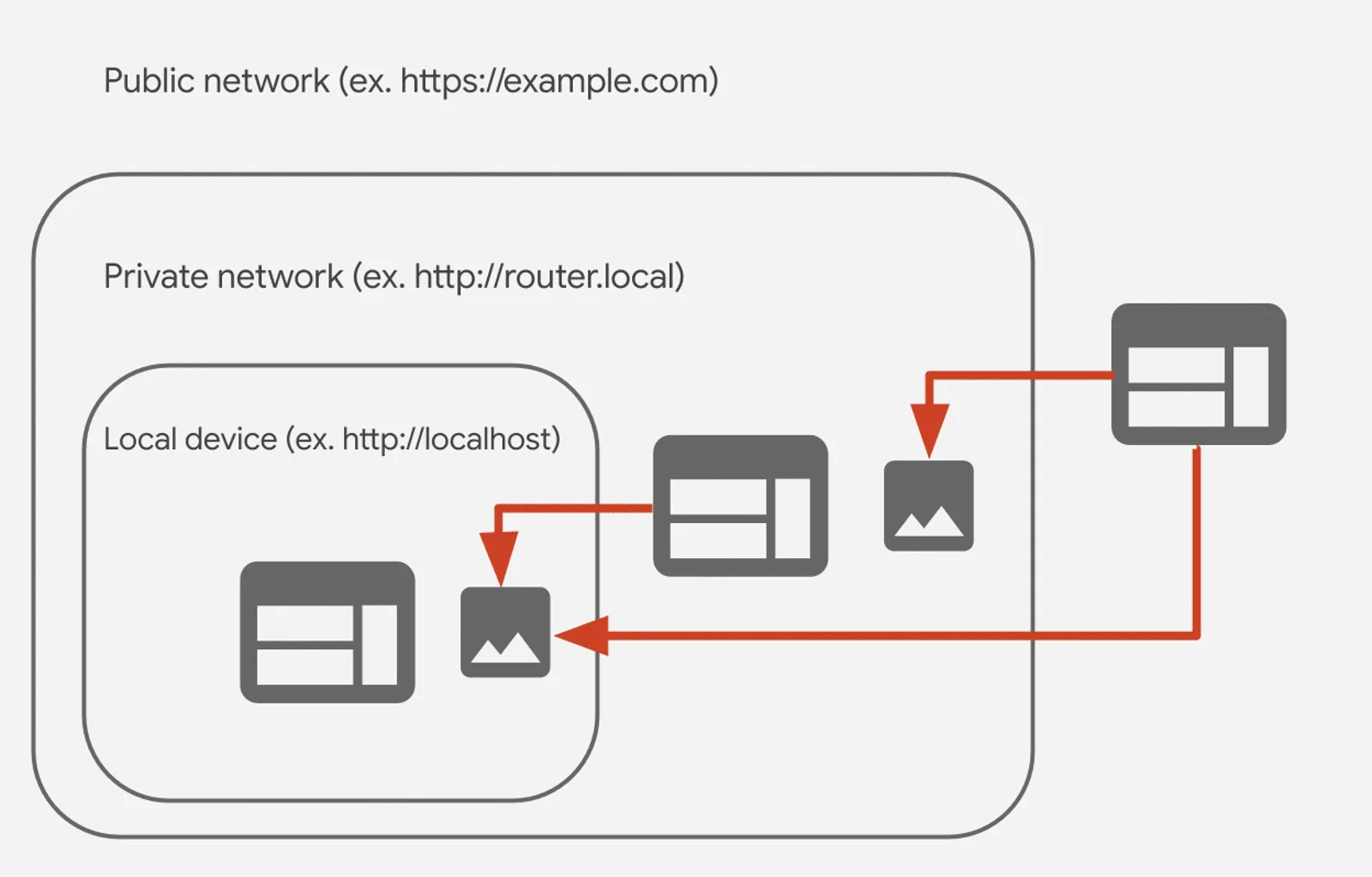
Illustration of how a public network communicates with a private network and local device using the 0.0.0.0 address. Source: Oligo
The technical details of the exploit, as outlined by the report, involve malicious websites tricking browsers into allowing them to interact with APIs (Application Programming Interfaces) running on a user’s local machine (localhost). These APIs are typically designed for internal communication within applications and should not be accessible from external sources like websites. By exploiting the 0.0.0.0 Day vulnerability, attackers could potentially gain unauthorized access to sensitive information stored on a user’s computer, steal data, or even launch malware.
Inconsistent Security Implementations Behind Flaw
The research highlights a concerning gap in browser security. Browsers are designed to act as a barrier between users and potentially harmful online content. However, the 0.0.0.0 Day vulnerability exposes a weakness in how browsers handle network requests. This inconsistency in security mechanisms across different browsers potentially grants malicious actors access to a user’s local network and the services running on it.

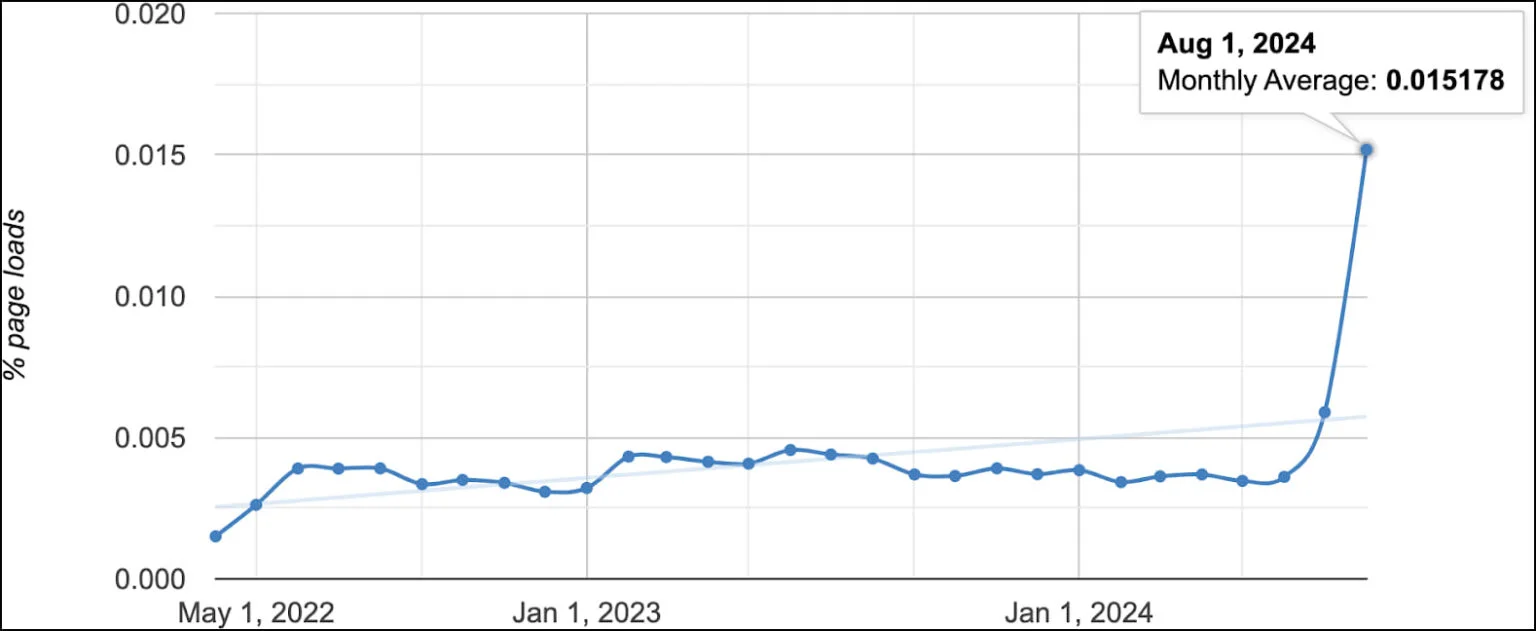
Number of websites communicating with 0.0.0.0
Source: Oligo
Impact on Major Browsers
The security implications of this vulnerability are far-reaching. Here’s a closer look at the potential impact on major browsers:
- Chrome Zero-Day Vulnerability: Google Chrome, the world’s most popular browser, is undoubtedly a prime target for attackers. A successful exploit of the 0.0.0.0 Day vulnerability could allow attackers to bypass Chrome’s security mechanisms and gain access to a user’s local network. This could expose sensitive data stored on a user’s computer, compromise corporate networks if a user is working remotely, or even facilitate the installation of malware.
- Firefox Zero-Day Vulnerability: While not as widely used as Chrome, Firefox is still a popular choice for many users. A successful exploit of the 0.0.0.0 Day vulnerability could have similar consequences for Firefox users. Attackers could potentially gain access to local networks, steal data, or launch malware attacks.
- Safari Zero-Day Vulnerability: Apple’s Safari browser, the default browser on Apple devices, is also potentially vulnerable to the 0.0.0.0 Day exploit. While Apple has a reputation for robust security, this vulnerability highlights the ever-present need for vigilance. A successful exploit could give attackers access to a user’s local network on their Mac or iOS device, potentially compromising sensitive data or facilitating further attacks.
In response to this security flaw, Apple and Google updated that are working to address the issue by closing the loophole. Reports indicate that Apple Safari will block all attempts to query the 0.0.0.0 IP address in the upcoming macOS 15 Sequoia beta version. Similarly, Google Chrome’s security team is also working on a fix. Google is rolling out updates to block access to 0.0.0.0, with complete implementation expected by Chrome 133.
Microsoft, on the other hand, had already implemented a block on the 0.0.0.0 IP address in Windows operating systems. Mozilla, however, has taken a different stance. A Mozilla spokesperson expressed concerns to Forbes that imposing tighter restrictions might introduce significant compatibility issues. As the discussion on standards and the assessment of these compatibility risks is ongoing, Firefox has yet to implement the proposed restrictions. Instead, Mozilla plans to continue engaging in the process to ensure a balanced approach.
The discovery of the 0.0.0.0 Day vulnerability highlights the ongoing challenge of maintaining browser security in an increasingly complex threat landscape. Browser developers must continue to invest in research and development to stay ahead of cybercriminals. Users must also remain vigilant and adopt best practices to protect themselves from emerging threats.





