Critical Bazaar Vulnerability CVE-2024-40348: Directory Traversal Flaw Threatens System Integrity – The Cyber Express

The Bazaar v1.4.3 vulnerability allows attackers to perform directory traversal via the /api/swaggerui/static component without authentication.
Ashish Khaitan July 22, 2024

Share on LinkedInShare on Twitter
A critical security flaw, CVE-2024-40348, has emerged in Bazaar v1.4.3, posing substantial risks due to its potential for directory traversal by unauthenticated attackers. Discovered by security researcher 4rdr, this Bazaar vulnerability allows malicious actors to exploit the /api/swaggerui/static component, compromising system integrity and confidentiality.
The vulnerability in Bazaar v1.4.3 centers around the /api/swaggerui/static component, where attackers can execute directory traversal attacks without requiring authentication. This allows them to manipulate paths improperly and gain unauthorized access to sensitive directories and files, significantly impacting system availability and confidentiality.
Directory traversal (or path traversal) is a security exploit where an attacker manipulates user input to access files and directories outside the intended scope of an application’s file system. By submitting crafted input that includes special characters like “../”, attackers exploit vulnerabilities in the application’s input validation process. This can lead to unauthorized access to sensitive files, configurations, or system files that compromise confidentiality and integrity.
Understanding Bazaar Vulnerability CVE-2024-40348 and Proof of Concept (PoC)
Source: X
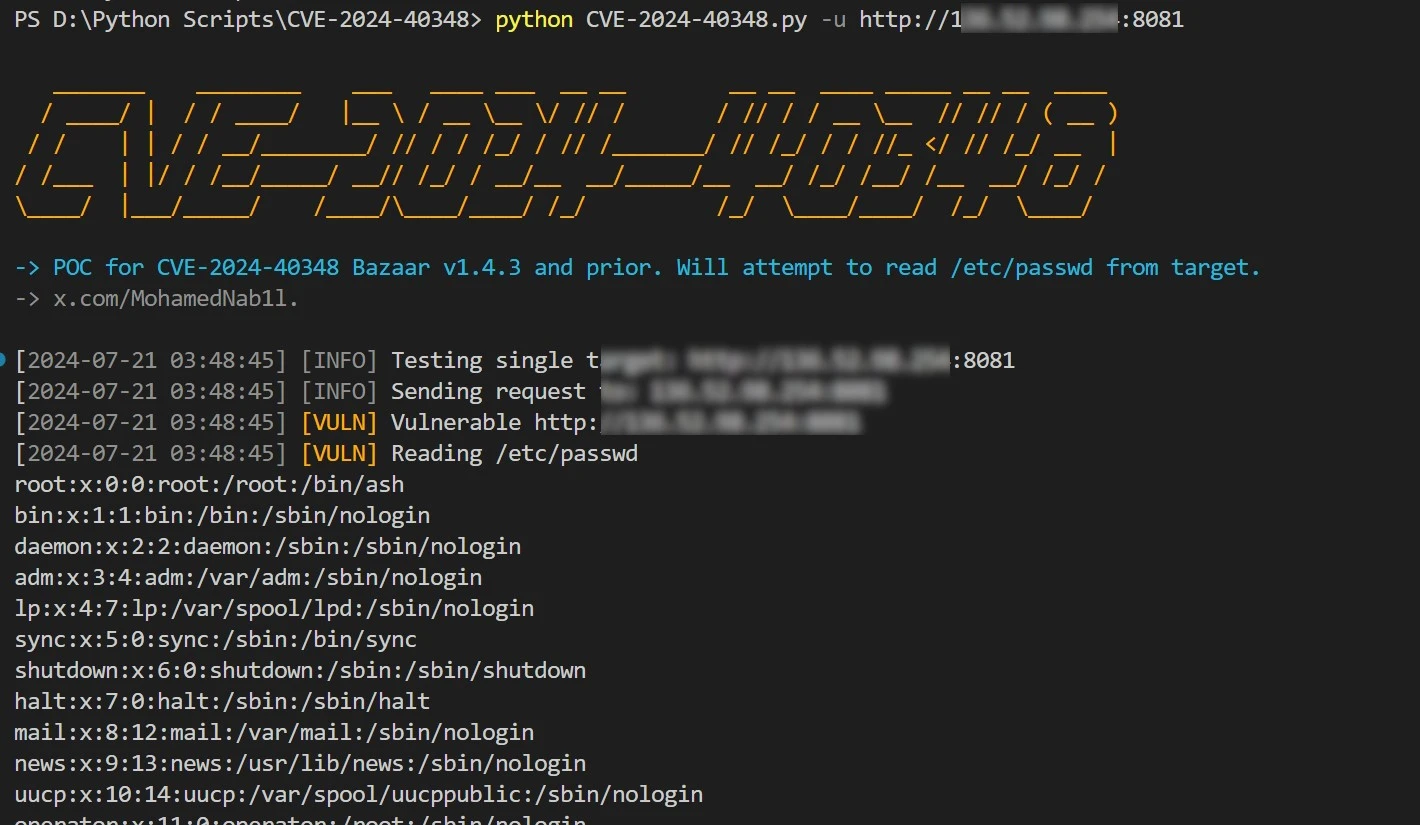
Security experts have developed a Proof of Concept (PoC) to demonstrate the exploitability of CVE-2024-40348. The PoC is designed to showcase how the Bazaar vulnerability can be weaponized, potentially leading to severe consequences such as ransomware deployment. By leveraging this PoC, attackers can exploit the vulnerability to execute arbitrary code and compromise targeted systems.
The vulnerability manipulates user input within the /api/swaggerui/static component, facilitating the traversal of directory paths. This manipulation can be exploited to access restricted directories outside the intended scope, exposing critical system files and compromising data integrity. The Common Weakness Enumeration (CWE) categorizes this issue under CWE-22, emphasizing its severity in terms of confidentiality, integrity, and availability.
CVE-2024-40348 in Action and Counter Measures
The exploitation of CVE-2024-40348 has been observed in the wild, highlighting its immediate threat to systems using Bazaar v1.4.3 and earlier versions. Attackers exploit the vulnerability to access sensitive files, as demonstrated by attempts to read system files like /etc/passwd from vulnerable targets. This exploitation highlights the urgent need for mitigation strategies and security patches to protect against potential breaches.
Currently, there are no known countermeasures or security patches available specifically addressing CVE-2024-40348. Security recommendations include monitoring system logs for suspicious activities, implementing stringent access controls, and conducting regular vulnerability assessments. Organizations are advised to replace or restrict the affected components until an official patch is released by Bazaar.
The vulnerability assessment for CVE-2024-40348 indicates its severity based on the Common Vulnerability Scoring System (CVSS). While specific CVSS scores are pending, the nature of the vulnerability suggests high potential impact on affected systems. Organizations are encouraged to stay updated with the latest security advisories and apply patches promptly upon release.




