Microsoft Recovery Tool Released To Address CrowdStrike Issues

This article outlines the recovery steps and details of repair options available for Windows clients, servers, and OS hosted on Hyper-V.
Samiksha Jain July 22, 2024

Share on LinkedInShare on Twitter
In response to the widespread issues caused by the CrowdStrike Falcon agent on Windows clients and servers, Microsoft has introduced an updated recovery tool designed to streamline the repair process for IT administrators. The updated Microsoft recovery tool offers two repair options, providing flexibility in addressing the problems on affected systems.
This article outlines the recovery steps and details of repair options available for Windows clients, servers, and OS hosted on Hyper-V.
The signed Microsoft recovery tool is available for download from the Microsoft Download Center. Administrators can access the tool using the following link: Microsoft Recovery Tool. The tool includes detailed instructions for recovering Windows clients and servers, as well as OS hosted on Hyper-V environments.
Microsoft Recovery Tool: Repair Options
Microsoft provides two distinct recovery options:
- Recover from WinPE (Windows Preinstallation Environment)
- Recover from Safe Mode
Recover from WinPE
The WinPE recovery option is recommended for its efficiency and ease of use. This method does not require local administrator privileges, making it a convenient choice for IT administrators. However, if BitLocker is enabled on the device, the BitLocker recovery key will need to be manually entered.
For devices using third-party disk encryption solutions, administrators should consult the vendor’s guidance to recover the drive.
Steps for WinPE Recovery:
- Insert the USB key into the impacted device.
- Reboot the device and press F12 (or follow manufacturer-specific instructions) to enter the BIOS boot menu.
- Select the option to boot from the USB drive.
- If BitLocker is enabled, enter the BitLocker recovery key.
- The tool will run the remediation script as recommended by CrowdStrike.
- Remove the USB drive and reboot the device normally.
Recover from Safe Mode
The Safe Mode recovery option can be useful for devices with TPM-only protectors or those where the BitLocker recovery key is not readily available. This method requires access to an account with local administrator privileges.
Steps for Safe Mode Recovery:
- Insert the USB key into the impacted device.
- Reboot the device and press F12 (or follow manufacturer-specific instructions) to enter the BIOS boot menu.
- Select the option to boot from the USB drive.
- The tool will configure the machine to boot in Safe Mode.
- Reboot the device into Safe Mode.
- Run the repair.cmd script from the root of the USB drive.
- The tool will remove impacted files and restore the normal boot configuration.
- Reboot the device normally.
Additional Considerations
Some devices may have restrictions that prevent them from connecting to a USB drive. In such cases, reimaging the device may be a better option. As with any recovery process, it is advisable to test the recovery steps on multiple devices before applying them broadly across an environment.
Creating the Boot Media
To create the bootable recovery media, administrators will need the following prerequisites:
- A Windows 64-bit client with at least 8GB of free space.
- Administrative privileges on the Windows client.
- A USB drive with a minimum of 1GB and a maximum of 32GB capacity. Note that all existing data on this USB drive will be wiped.
Steps to Generate WinPE Recovery Media:
- Download the Microsoft Recovery Tool from the Microsoft Download Center.
- Extract the PowerShell script from the downloaded solution.
- Run MsftRecoveryToolForCSv2.ps1 from an elevated PowerShell prompt.
- The ADK will download and media creation will start, taking several minutes.
- Select the option to generate an ISO or USB drive and specify the drive letter.
Using Recovery Media on Hyper-V Virtual Machines
The recovery media can also be used to remediate impacted Hyper-V virtual machines. Administrators should select the option to generate an ISO when creating the recovery media. For non-Hyper-V virtual machines, follow the hypervisor vendor’s instructions to use the recovery media.
Steps to Recover Hyper-V Virtual Machines:
- Add a DVD Drive under Hyper-V settings > SCSI Controller.
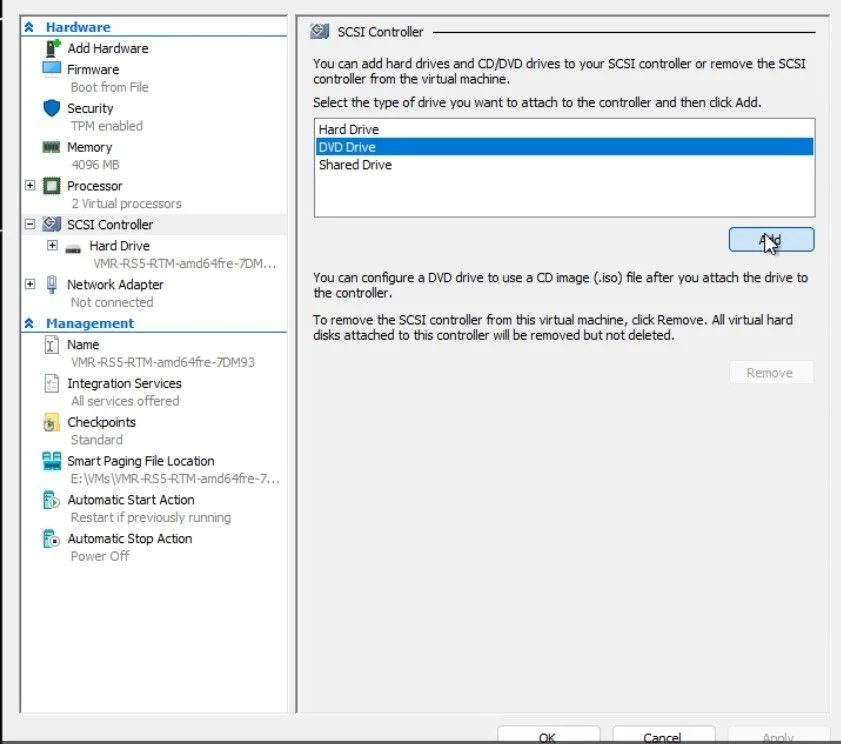
Screenshot for where to add the DVD Drive
2. Add the recovery ISO as an Image file under Hyper-V settings > SCSI Controller > DVD Drive.
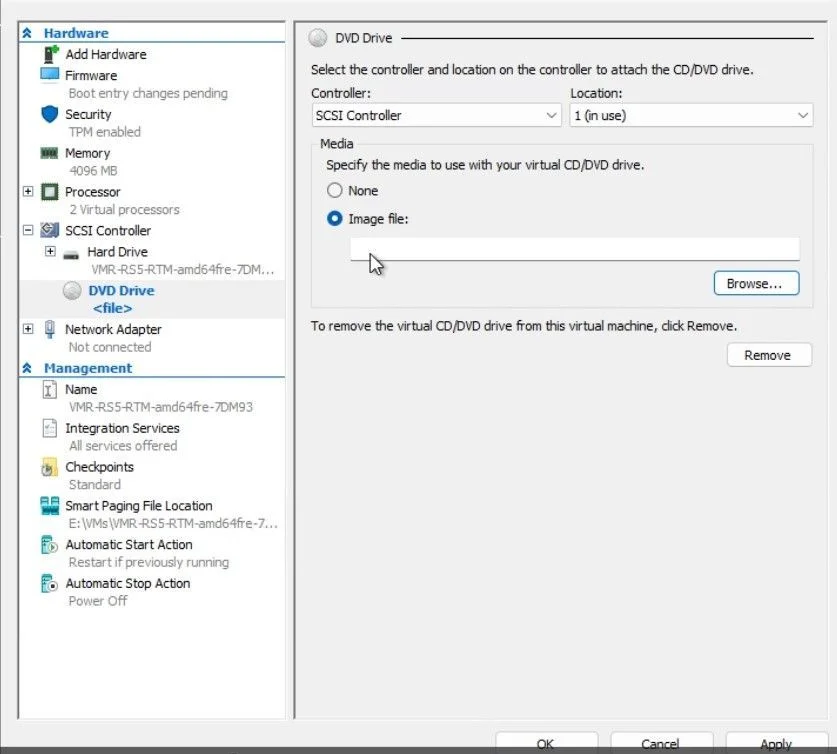
Screenshot of where to add the image file
3. Change the boot order to move the added DVD Drive to the first boot entry.

Screen shot of the original boot order.
4. Start the virtual machine and boot to the ISO image.
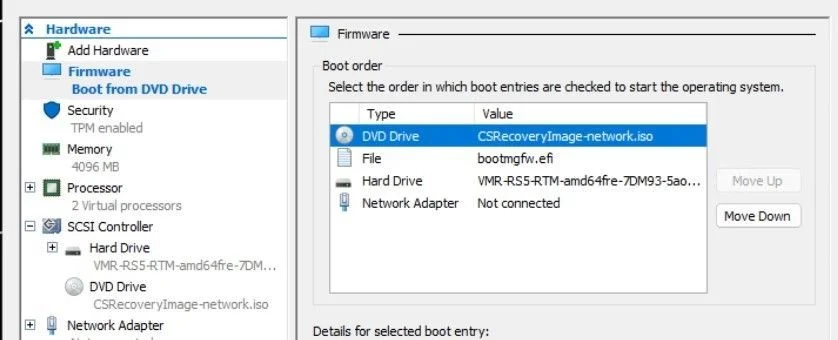
Screenshot of change the boot order.
5. Follow the appropriate recovery steps (WinPE or Safe Mode) as described above.
6. Restore the boot order to its original settings.
7. Reboot the virtual machine normally.
Background on the CrowdStrike Falcon Agent Issue
On Friday, July 20, Windows users worldwide were hit by the Blue Screen of Death (BSOD), a critical error attributed to a file named “csagent.sys” associated with CrowdStrike’s Falcon Sensor.
This issue led to sudden crashes upon startup or reboot, causing significant disruptions across various sectors, including major banks, media companies, tech firms, and critical infrastructures like airports and airlines.
Discussions on social media revealed the widespread nature of the problem, with users from Germany, India, Japan, and the U.S. sharing their frustrating experiences. The Australian government assured the public that this was not a cybersecurity incident and urged calm, stating there was no reason to panic.
Conclusion
Microsoft’s proactive release of the recovery tool provides a vital solution for IT admins and users affected by the CrowdStrike Falcon agent issue. By following the detailed recovery steps and choosing the appropriate recovery option, users can restore normal operations to their impacted devices.





