Hackers Exploit RDPWrapper And Tailscale In Crypto Attacks

This campaign uses RDPWrapper and Tailscale to gain unauthorized access and control victim systems through multiple stages.
Ashish Khaitan July 18, 2024

Share on LinkedInShare on Twitter
A new sophisticated campaign has been discovered targeting individuals involved in the cryptocurrency market. This campaign utilizes a multi-stage approach, primarily leveraging RDPWrapper and Tailscale to facilitate unauthorized access and establish control over victim systems.
The attack begins with a malicious Zip file containing a shortcut (.lnk) file. Upon execution, this shortcut triggers a PowerShell script download from a remote server, initiating a sequence of actions designed to compromise the victim’s system. Notably, the PowerShell script is obfuscated to evade detection mechanisms.
An Overview of the RDPWrapper and Tailscale Campaign
The campaign involves several malicious components, including PowerShell scripts, batch files, Go-based binaries, and exploits targeting a vulnerable driver known as Terminator (Spyboy). Although Terminator was not immediately activated during initial infections, its potential use highlights the threat actor’s intent to escalate privileges post-infection.

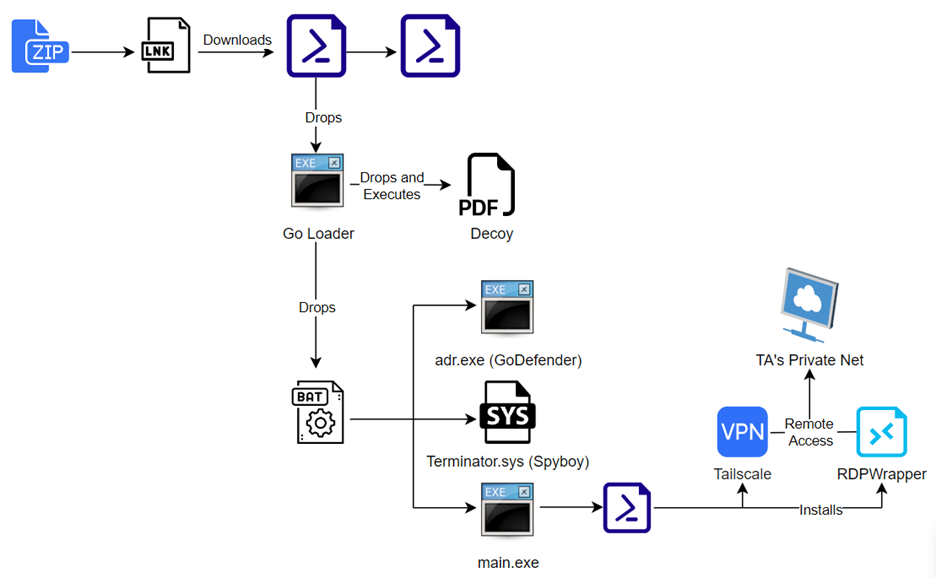
Infection Chain of RDPWrapper and Tailscale campaign (Credit: Cyble)
According to Cyble Research and Intelligence Labs (CRIL), a unique aspect of this campaign is the exploitation of legitimate tools such as RDPWrapper and Tailscale. RDPWrapper enables multiple Remote Desktop Protocol (RDP) sessions per user, circumventing the default Windows restriction of one session per PC. This capability allows threat actors to maintain persistent access to compromised systems discreetly.
Tailscale, on the other hand, is employed by threat actors to establish a secure, private network connection. By configuring Tailscale, attackers add the victim’s machine as a node on their private network, facilitating remote command execution and data exfiltration without direct visibility from conventional network security measures.
Geographic and Industry Targeting
The attackers have tailored their approach with geographic and industry-specific targeting in mind. Evidence suggests a focus on Indian users within the cryptocurrency ecosystem, as indicated by the deployment of a decoy PDF related to cryptocurrency futures trading on CoinDCX, a prominent Indian exchange platform.
Following initial infection, the malware drops and executes a Go-based loader that performs anti-virtualization and anti-debugging checks. It then downloads additional payloads, including GoDefender (adr.exe) and potentially malicious drivers like Terminator.sys. These payloads are designed to evade detection and enhance control over the compromised system.
Furthermore, the malware configures the system to allow for multiple concurrent RDP sessions using RDPWrapper. It also manipulates system registries and installs software like Tailscale to maintain persistent access and facilitate further malicious activities.
Strategic Implications and Recommendations for Mitigation
Once established, RDP access grants threat actors significant control over compromised devices. They can execute commands, deploy ransomware, exfiltrate sensitive data, or pivot to other systems within the network, potentially causing severe operational and financial damage.
Cyble’s investigation revealed similarities between this campaign and previous incidents involving the StealC malware strain. The reuse of the same decoy PDF and attack techniques suggests a common threat actor behind these operations, possibly targeting cryptocurrency users with varying attack vectors.
To mitigate the risks of sophisticated cyber campaigns targeting cryptocurrency users, Cyble recommends proactive measures. Monitoring should include detection of base64-encoded PowerShell scripts and unauthorized software installations like RDP wrappers.
Enhanced security configurations involve strengthening UAC settings, monitoring Defender exclusion paths, and implementing strong authentication for RDP sessions. Network segmentation is crucial to isolate critical systems and minimize the impact of potential compromises.
Threat actors exploit tools such as RDPWrapper and Tailscale to evade detection and maintain persistent access, posing significant operational and financial risks. Maintaining vigilance, implementing proactive security measures, and staying updated with threat intelligence are essential to effectively defend against these advanced cyber threats in today’s digital environment.





