Fin7 CyberCriminal Gang Sells Tools To Evade EDR Detection

The group sells and distributes several of these EDR bypass tools across underground forums.
Alan J July 17, 2024

Share on LinkedInShare on Twitter
FIN7, a financially motivated threat actor group with origins in Russia, has shown a persistent determination to evolve and adapt its tactics despite setbacks and arrests, utilizing multiple pseudonyms to mask its true identity and sustain its criminal operations.
The group, which has been active since 2012, initially focused on point-of-sale malware for financial fraud, but shifted to ransomware operations in 2020, affiliating with well-known ransomware-as-a-service groups and launching its own independent programs.
FIN7 Underground Operations
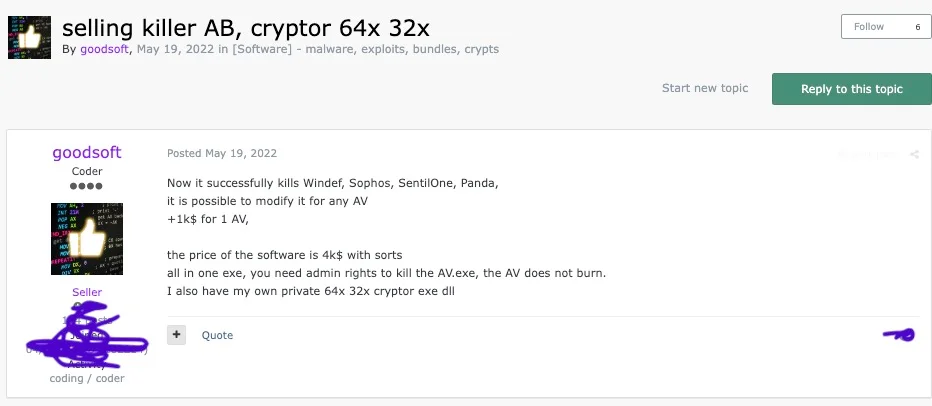
New research from SentinelOne has uncovered FIN7’s recent activities in underground criminal forums, where the group markets its tools and services under various fake aliases. Of these tools, the group has most prominently been selling a highly specialized tool labelled as AvNeutralizer (also known as AuKill) that is designed to disable most security solutions.

Source:sentinelone.com
Advertisements for the AvNeutralizer tool appeared on multiple different forums under various usernames, for sale in prices ranging from $4,000 to $15,000. Researchers state that the tool’s widespread adoption by various ransomware groups suggests it is no longer exclusive to a single threat actor’s operations.
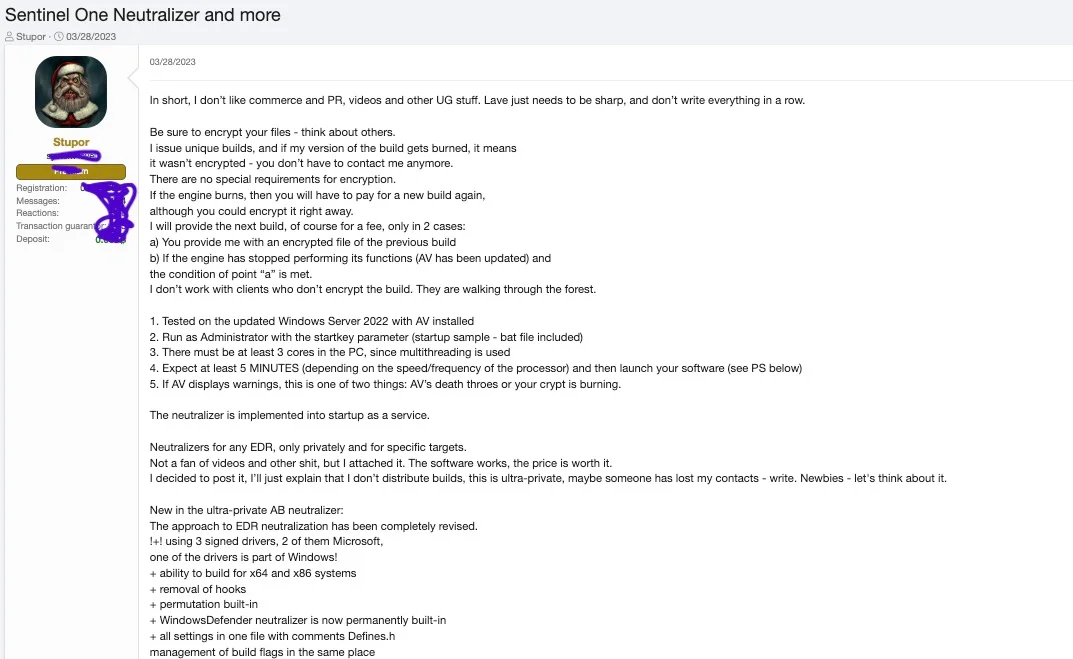
Researchers identified several usernames – including “goodsoft,” “lefroggy,” “killerAV” and “Stupor” – that suggested association with the FIN7 cybercriminal group in promoting its tools and services, such as a post-exploitation framework labelled as “PentestSoftware.”

Source:sentinelone.com
The group’s use of multiple identities across different forums appears to be a strategy to mask its true identity while maintaining its illicit operations.
FIN7 Arsenal Used in Operations
The FIN7 cybercriminal group’s success in executing sophisticated cyberattack operations relies on a versatile toolkit that includes:
- Powertrash: A heavily obfuscated PowerShell script used to reflectively load malware in memory, evading detection.
- Diceloader: A minimal backdoor allowing attackers to establish command and control channels and load additional modules.
- SSH-based backdoor: A persistence mechanism using OpenSSH and 7zip to maintain access to compromised systems.
- Core Impact: A commercial penetration testing tool repurposed for malicious activities.
- AvNeutralizer: A specialized tool for disabling security solutions.
Analysis of Powertrash samples revealed a timeline of FIN7’s malware evolution, showing a transition from Carbanak to Diceloader (also known as Lizar) in early 2021. The group has also incorporated the Core Impact pentesting tool into its arsenal, in correlation with observed underground forum activity where FIN7-associated accounts actively sought cracked copies of the software.
FIN7’s infrastructure includes command and control servers for Diceloader, which researchers have tracked across various countries and hosting providers. In one instance, an exposed server revealed the group’s use of an SSH-based backdoor for stealthy file exfiltration.
The group’s adoption of commercial tools like Core Impact demonstrates its commitment to using sophisticated, hard-to-detect methods for compromising target networks.
The new research sheds light on FIN7’s persistent adaptability and ongoing evolution in its operations, which include adoption of automated attack methods such as the targeting of publicly-facing servers through the use of automated SQL injection attacks.
Additionally, the group’s development and sale of specialized independently-developed tools such as AvNeutralizer in various criminal underground forums bolster the group’s impact and influence among other cybercriminals while demonstrating its technical expertise.
Fin7’s use of multiple identities and active collaboration with other threat actor groups makes it much more challenging for researchers to attribute their operations. The researchers said they hope the research would inspire more efforts to understand and protect against FIN7’s continually evolving attack tactics.