Deceptive Malware Ad Campaign Targets MacOS Users

The campaign aims to deploy the Atomic Stealer malware on infected systems. Campaign ads were traced to Hong Kong.
Alan J July 13, 2024

Share on LinkedInShare on Twitter
A sophisticated malvertising campaign is targeting Mac users searching for Microsoft Teams, highlighting the growing competition among malware creators in the macOS ecosystem. This latest attack, which uses Atomic Stealer malware, which follows closely on the heels of the Poseidon (OSX.RodStealer) project, indicates growing advancements in threats affecting macOS.
Deceptive Microsoft Teams for macOS Ad Campaign
The malicious ad campaign, which ran for several days, employed advanced filtering techniques to evade detection. Appearing as a top search result for Microsoft Teams, the ad displayed microsoft.com as its URL but actually redirected users through a series of deceptive links.
The ad was likely paid for by a compromised Google ad account. Initially, the ad redirected straight to Microsoft’s website, but after multiple attempts and tweaks, a full attack chain was finally observed.


Source: malwarebytes.com
Researchers from Malwarebytes stated that upon clicking the ad, users were subjected to a profiling process to ensure only actual people proceeded. This could help the malicious site evade detection from automated security tools and scans. A cloaking domain then separated the initial redirect from the malicious landing page, which mimicked the design of the official Microsoft Teams download site.
The ad was found to be malicious, with a display URL showing Microsoft.com, but actually leading to a fake installation page. The advertiser, located in Hong Kong, runs over a thousand unrelated ads. Upon further investigation, it was discovered that the ad was using a unique payload for each visitor, generated from a domain called locallyhyped.com.

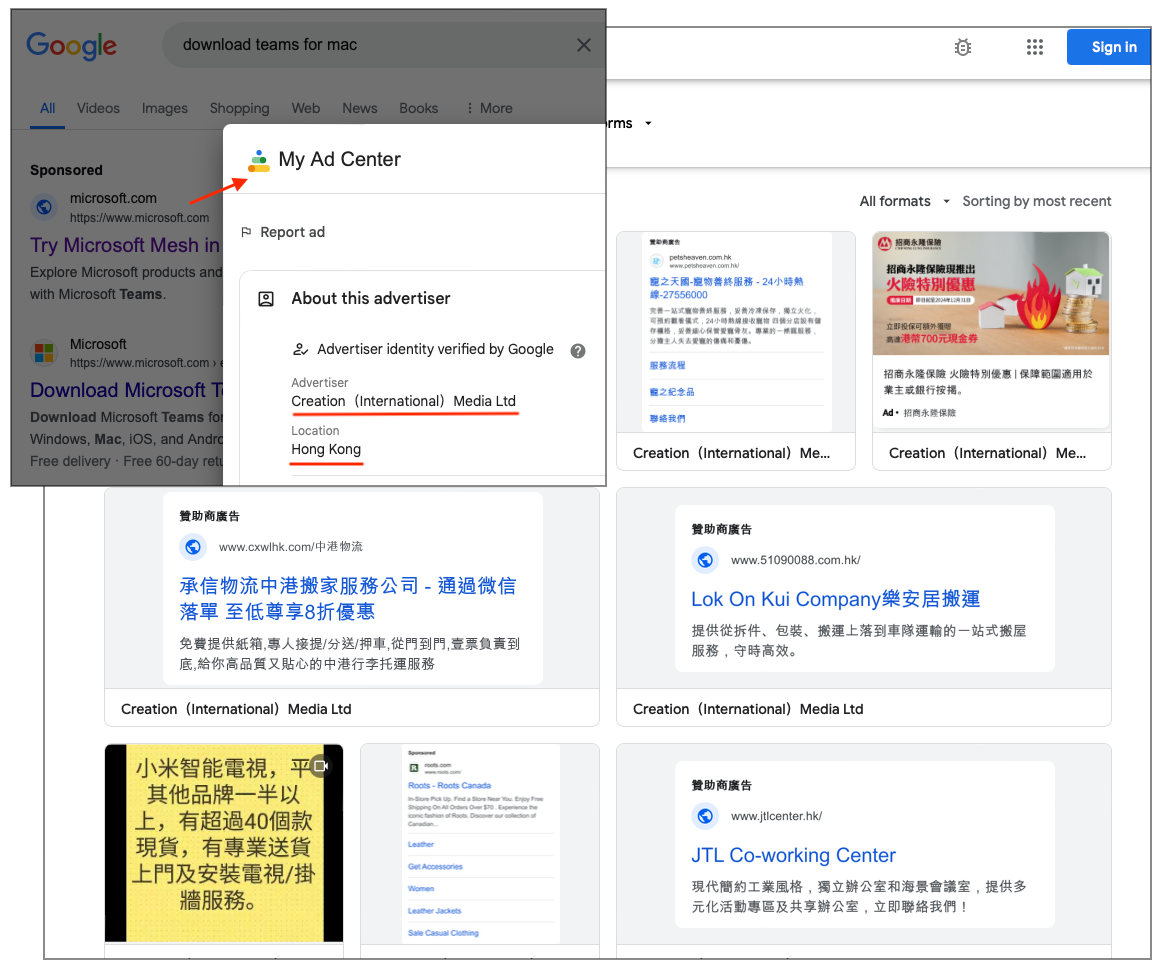
Source: malwarebytes.com
Once the downloaded file was opened, the user was instructed to enter their password and grant access to the file system, allowing the malicious application to steal keychain passwords and important files. Following data theft, the data was exfiltrated via a single POST request to a remote attacker-controlled web server.
Mitigations for macOS Devices
To avoid falling victim to such attacks, researchers advised caution while downloading applications via search engines. Malvertising and SEO poisoning attacks can have devastating consequences, and it’s crucial to use browser protection tools with the ability to block ads and malicious websites. Additionally, it’s recommended to regularly update antivirus software and use a reputable ad blocker to minimize the risk of malware infection.

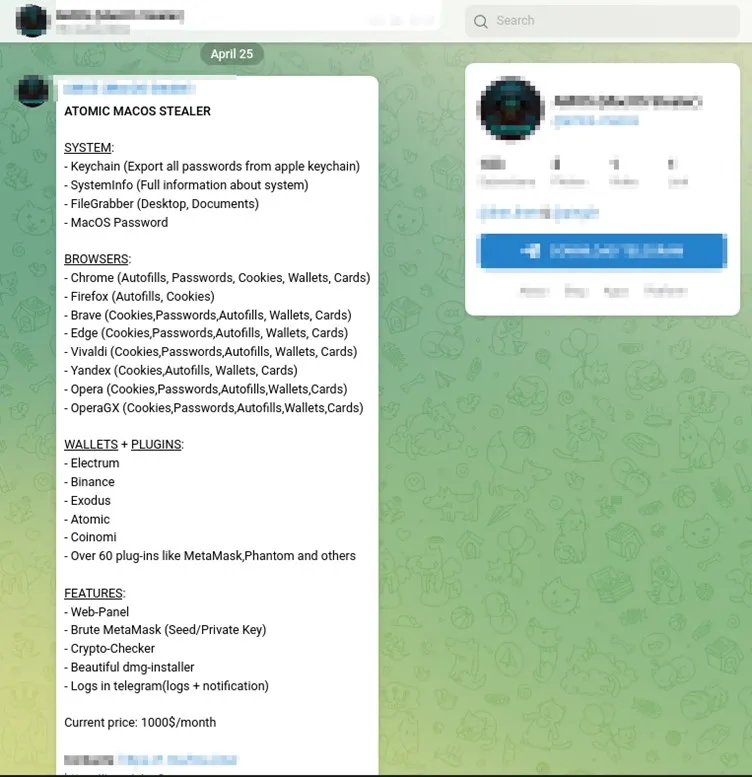
This campaign underscores the increasing sophistication of macOS malware due to the keen interest demonstrated by threat actors in compromising the operating system’s environment. Last year, researchers from Cyble Research and Intelligence Labs (CRIL) observed that the Atomic Stealer used in this campaign, had been offered via Telegram at the price of $1000 USD per month.





